| New Threat Detection Added | 5 (DinodasRAT, Firebird RAT, Matsnu Malware, DarkGate RAT and Ducktail Malware) |
| New Threat Protections | 96 |
Weekly Detected Threats
The following threats were added to Crystal Eye XDR this week:
|
Threat name:
|
DinodasRAT | |||||||||||||||||||||
|
DinodasRAT, also known as XDealer, is a sneaky malware that gives attackers full control of your computer. This multi-platform threat can spy on you, steal data, and even run programs remotely. DinodasRAT has versions for Windows and Linux, and it's especially dangerous because it can hide its tracks. Developed from a legitimate remote access tool, it's been linked to cyberespionage campaigns targeting governments.
|
||||||||||||||||||||||
|
Threat Protected:
|
02 | |||||||||||||||||||||
|
Rule Set Type:
|
|
|||||||||||||||||||||
|
Class Type:
|
Trojan-activity | |||||||||||||||||||||
|
Kill Chain:
|
|
|||||||||||||||||||||
|
Threat name:
|
Firebird RAT | ||||||||||||||||||||||||
|
Firebird RAT, also known as Hive RAT, was a malicious remote access tool that masquerades as a legitimate administration tool and grants attackers full control of infected devices. Firebird boasted stealthy features and could steal passwords, spy on victims, and even turn their machines into parts of large botnets. Thankfully, in April 2024, authorities arrested those believed to be behind Firebird's creation and distribution.
|
|||||||||||||||||||||||||
|
Threat Protected:
|
01 | ||||||||||||||||||||||||
|
Rule Set Type:
|
|
||||||||||||||||||||||||
|
Class Type:
|
Trojan-activity | ||||||||||||||||||||||||
|
Kill Chain:
|
|
||||||||||||||||||||||||
|
Threat name:
|
Matsnu Malware | ||||||||||||||||||||||||
|
Matsnu is a sneaky Windows Trojan that acts as a backdoor for attackers. It infects your system and hides, impersonating other software to avoid detection. Once in, it can download and run malicious programs on your machine. This malware uses clever tricks like domain generation algorithms to connect with its command centre, making it harder to block. Matsnu is a serious threat that can steal data or encrypt your files.
|
|||||||||||||||||||||||||
|
Threat Protected:
|
01 | ||||||||||||||||||||||||
|
Rule Set Type:
|
|
||||||||||||||||||||||||
|
Class Type:
|
Trojan-activity | ||||||||||||||||||||||||
|
Kill Chain:
|
|
||||||||||||||||||||||||
|
Threat name:
|
DarkGate RAT | ||||||||||||||||||||||||
|
DarkGate, lurking since 2018, is a Remote Access Trojan (RAT) for hire. Sold on cybercrime forums, it grants attackers full control of infected devices. Disguised as harmless files, DarkGate can steal your data, spy on your keystrokes, and even take control of your webcam. This RAT is known for evading detection and has exploited Windows vulnerabilities in the past. Stay vigilant, keep your software updated, and be cautious of suspicious links or attachments to avoid DarkGate's grasp.
|
|||||||||||||||||||||||||
|
Threat Protected:
|
01 | ||||||||||||||||||||||||
|
Rule Set Type:
|
|
||||||||||||||||||||||||
|
Class Type:
|
Trojan-activity | ||||||||||||||||||||||||
|
Kill Chain:
|
|
||||||||||||||||||||||||
|
Threat name:
|
Ducktail Malware | ||||||||||||||||||||||||
|
Ducktail malware, active since 2021, targets Facebook Business accounts. This Vietnamese cybercrime operation spreads through fake job postings, often on LinkedIn. Luring marketing professionals, they send archives with malware disguised as PDFs containing fashion industry content. Ducktail steals Facebook session cookies to hijack ad accounts, potentially causing financial losses and privacy issues for businesses.
|
|||||||||||||||||||||||||
|
Threat Protected:
|
03 | ||||||||||||||||||||||||
|
Rule Set Type:
|
|
||||||||||||||||||||||||
|
Class Type:
|
Trojan-activity | ||||||||||||||||||||||||
|
Kill Chain:
|
|
||||||||||||||||||||||||
Known exploited vulnerabilities (Week 1 - May 2024)
|
Threat
|
CVSS
|
Description | |
|
CVE-2024-29988
|
8.8 (High)
|
Microsoft SmartScreen Prompt Security Feature Bypass Vulnerability
|
|
|
CVE-2023-7028
|
7.5 (High)
|
GitLab Community and Enterprise Editions Improper Access Control Vulnerability
|
Updated Malware Signatures (Week 1 - May 2024)
|
Threat
|
Description
|
|
|
Upatre
|
Upatre is also a malware dropper that downloads additional malware on an infected machine. It is usually observed to drop banking trojan after the initial infection.
|
|
|
Remcos
|
Remcos functions as a remote access trojan (RAT), granting unauthorised individuals the ability to issue commands on the compromised host, record keystrokes, engage with the host's webcam, and take snapshots. Typically, this malicious software is distributed through Microsoft Office documents containing macros, which are often attached to malicious emails.
|
|
|
QuasarRat
|
A remote access trojan that was made available to the public as an open-source project. Once installed on a victim’s machine, it is capable of keylogging, data and screen capturing among other things. It is also known to be highly customisable depending on the threat actor’s intended need.
|
|
|
Bifrost
|
A remote access trojan that enables its operator to take control of a victim machine and steal data. It is usually distributed through spam and phishing emails.
|
| Ransomware Report | |
|
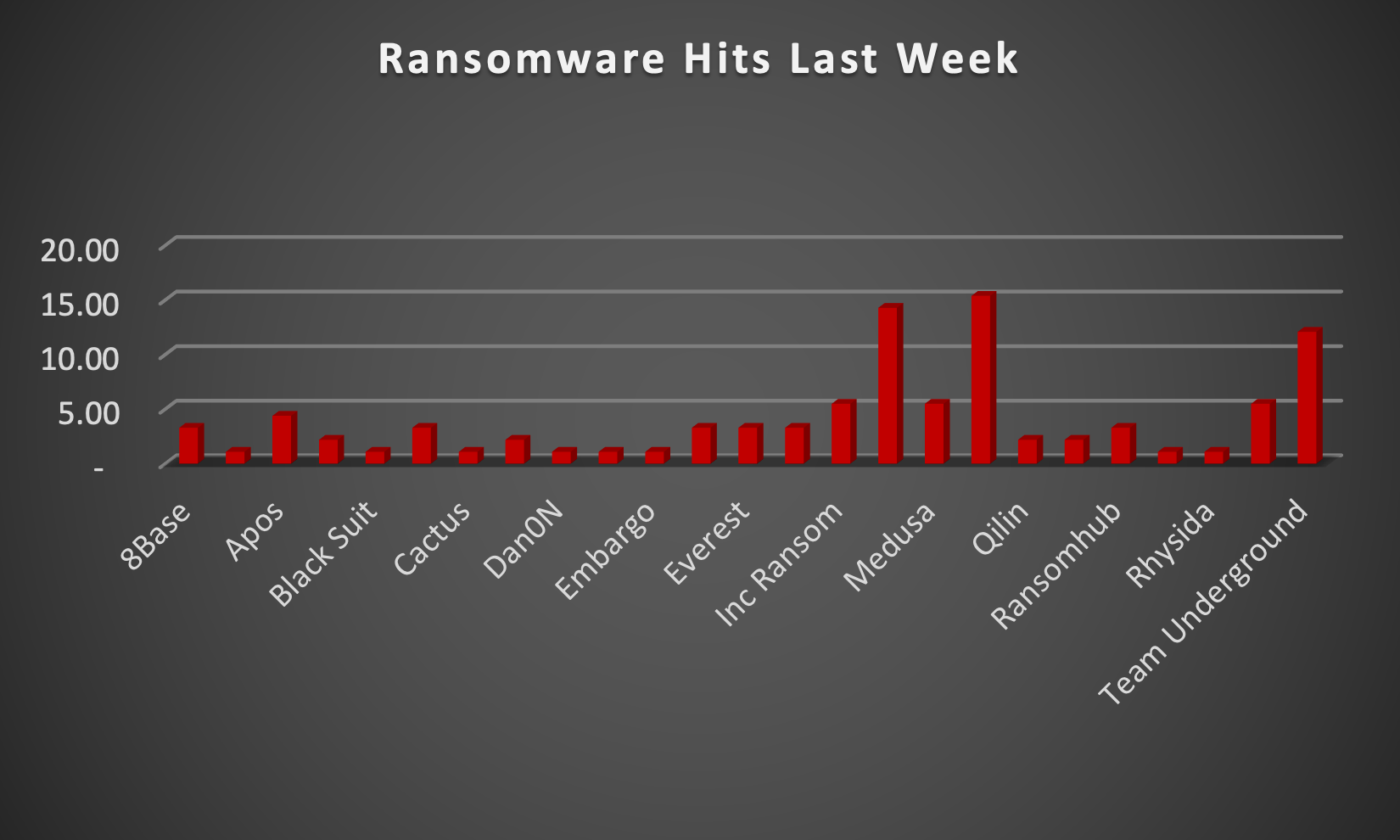
The Red Piranha Team actively collects information on organisations globally affected by ransomware attacks from various sources, including the Dark Web. In the past week alone, our team uncovered new ransomware victims and updates on previous victims across 20 different industries spanning 26 countries. This underscores the widespread and indiscriminate impact of ransomware attacks, emphasising their potential to affect organisations of varying sizes and sectors worldwide. Play ransomware stands out as the most prolific, having updated a significant number of victims (15%) distributed across multiple countries. In comparison, LockBit3.0 ransomware updated 14% victims, in the past week. The following list provides the victim counts in percentages for these ransomware groups and a selection of others. |
|
| Name of Ransomware Group | Percentage of new Victims last week |
|
8Base
|
3.30%
|
|
Akira
|
1.10%
|
|
Apos
|
4.40%
|
|
Bianlian
|
2.20%
|
|
Black Suit
|
1.10%
|
|
Blackbasta
|
3.30%
|
|
Cactus
|
1.10%
|
|
Cloak
|
2.20%
|
|
Dan0N
|
1.10%
|
|
Darkvault
|
1.10%
|
|
Embargo
|
1.10%
|
|
Eraleign (Apt73)
|
3.30%
|
|
Everest
|
3.30%
|
|
Hunters
|
3.30%
|
|
INC Ransom
|
5.49%
|
|
Lockbit3.0
|
14.29%
|
|
Medusa
|
5.49%
|
|
Play
|
15.38%
|
|
Qilin
|
2.20%
|
|
RA Group
|
2.20%
|
|
Ransomhub
|
3.30%
|
|
Ransomware Blog
|
1.10%
|
|
Rhysida
|
1.10%
|
|
Space Bears
|
5.49%
|
|
Team Underground
|
12.09%
|
|
Team Underground Ransomware Team Underground is a relatively new ransomware group that emerged in 2023. While not as notorious as some established actors, they have garnered attention for their tactics and the information they offer alongside their typical extortion attempts. Tactics, Techniques, and Procedures (TTPs) Delivery: The exact infection vector used by Team Underground is still under investigation. However, some reports suggest they might leverage spam campaigns with malicious attachments or exploit unpatched vulnerabilities in software to gain initial access. Encryption: Team Underground utilises a custom-made ransomware executable built with Microsoft Visual C/C++ and designed for 64-bit systems. The ransomware encrypts victim files and unlike many strains, doesn't alter filenames or extensions. Exfiltration: In a unique twist, Team Underground claims to steal data during the attack process. Their ransom note mentions exfiltrating sensitive information like financial records, employee data, and confidential agreements. This adds another layer of pressure on victims, as leaking such information could be disastrous. Ransom Note: Team Underground's ransom note, titled "!readme!!!.txt", stands out for offering more than just a decryption key in exchange for a ransom payment (which can be as high as $3 million!). They promise to provide details on exploited network vulnerabilities and even offer recommendations for improved information security. It is unclear if these are genuine offers or simply a ploy to build trust with victims. Leak Site: Team Underground maintains a leak site on the dark web where they threaten to publish stolen data if the ransom is not paid. Exploited Vulnerabilities Specific vulnerabilities exploited by Team Underground have not been publicly disclosed yet. However, their ability to gain access to systems suggests they target unpatched software vulnerabilities or weaknesses in network security. Recommendations:
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
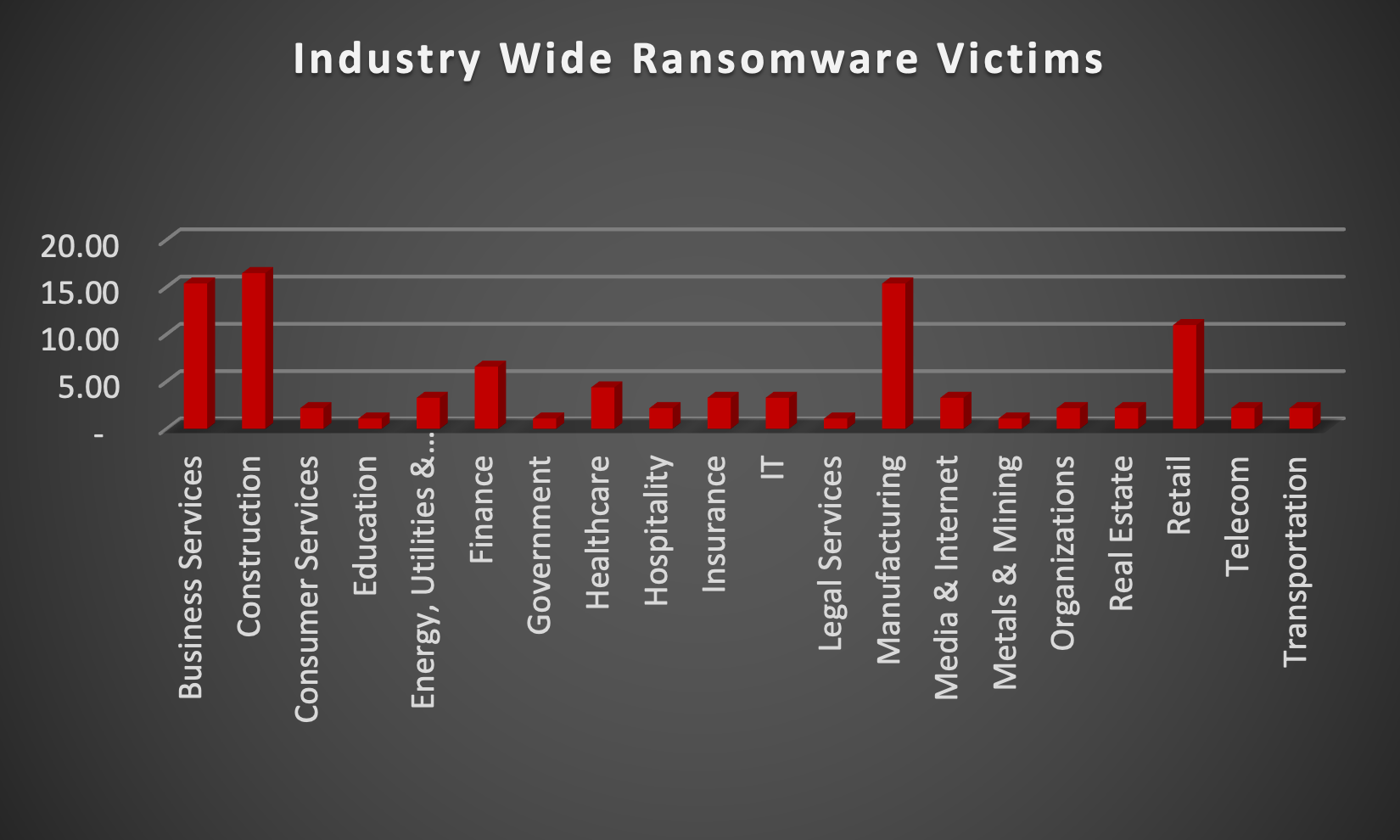
Upon further investigation, it has been identified that ransomware has left its mark on 20 different industries worldwide. Notably, the Manufacturing industry bore the brunt of the attacks in the past week, accounting for 15% of victims. There are a few key reasons why the manufacturing sector is a prime target for ransomware groups:
- High Disruption Potential: Manufacturing relies heavily on interconnected systems and just-in-time production. A ransomware attack can grind operations to a halt, causing significant financial losses due to production delays and lost revenue. This pressure to get back online quickly can make manufacturers more willing to pay the ransom.
- Vulnerable Legacy Systems: Many manufacturers use legacy control systems (OT) that haven't been updated for security. These older systems often lack robust security features, making them easier targets for attackers to exploit.
- Limited Cybersecurity Investment: Traditionally, cybersecurity might not have been a top priority for some manufacturers compared to production efficiency. This lack of investment in security awareness training and robust security protocols leaves them exposed.
- Valuable Data: Manufacturing facilities often hold valuable intellectual property (IP) and trade secrets. Ransomware groups may not only disrupt operations but also threaten to leak this sensitive data if the ransom isn't paid.
- Success Breeds Success: The high payout potential from past attacks on manufacturers incentivises ransomware groups to continue targeting them.
The table below delineates the most recent ransomware victims, organised by industry, shedding light on the sectors grappling with the significant impact of these cyber threats.
|
Name of the affected Industry
|
Victims Count (%)
|
|
Business Services
|
15.38%
|
|
Construction
|
16.48%
|
|
Consumer Services
|
2.20%
|
|
Education
|
1.10%
|
|
Energy, Utilities & Waste Treatment
|
3.30%
|
|
Finance
|
6.59%
|
|
Government
|
1.10%
|
|
Healthcare
|
4.40%
|
|
Hospitality
|
2.20%
|
|
Insurance
|
3.30%
|
|
IT
|
3.30%
|
|
Legal Services
|
1.10%
|
|
Manufacturing
|
15.38%
|
|
Media & Internet
|
3.30%
|
|
Metals & Mining
|
1.10%
|
|
Organisations
|
2.20%
|
|
Real Estate
|
2.20%
|
|
Retail
|
10.99%
|
|
Telecom
|
2.20%
|
|
Transportation
|
2.20%
|