Vulnerability Assessment & Penetration Testing
Fix vulnerabilities in your network and achieve compliance goals with Red Piranha’s comprehensive Vulnerability Assessment and Penetration Testing.
Red Piranha is one of the few security organisations with ISO/IEC 27001 and CREST Certifications to demonstrate that our processes, tools
and systems adhere to a recognised framework. Learn why choose Red Piranha's VAPT services.
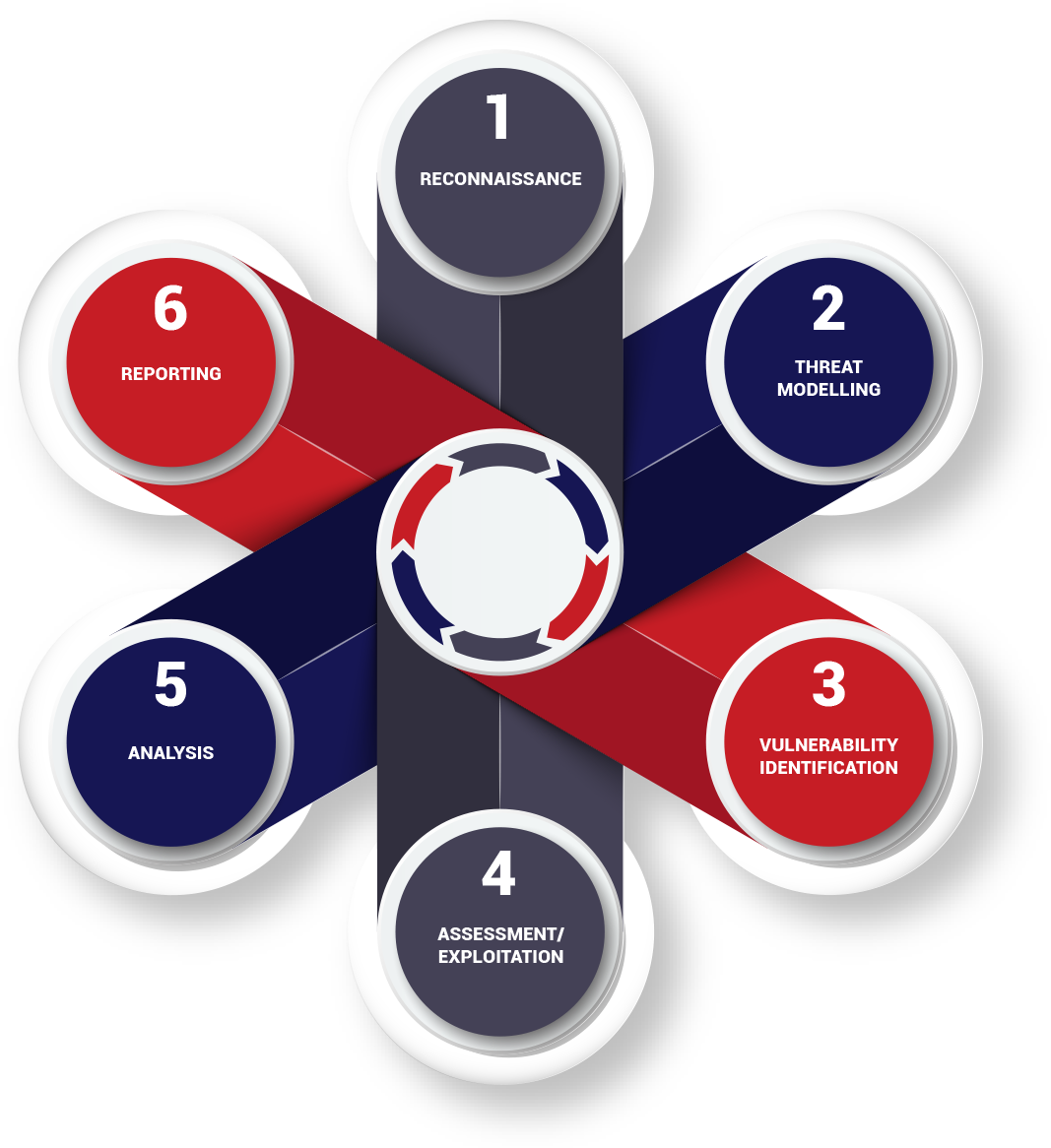
Our experienced security experts with intimate knowledge of the latest vulnerabilities and attack methods makes sure you get the most out of the security testing.
Our team of certified and accredited security professionals deliver a full range of security testing services customisable to meet specific testing needs.
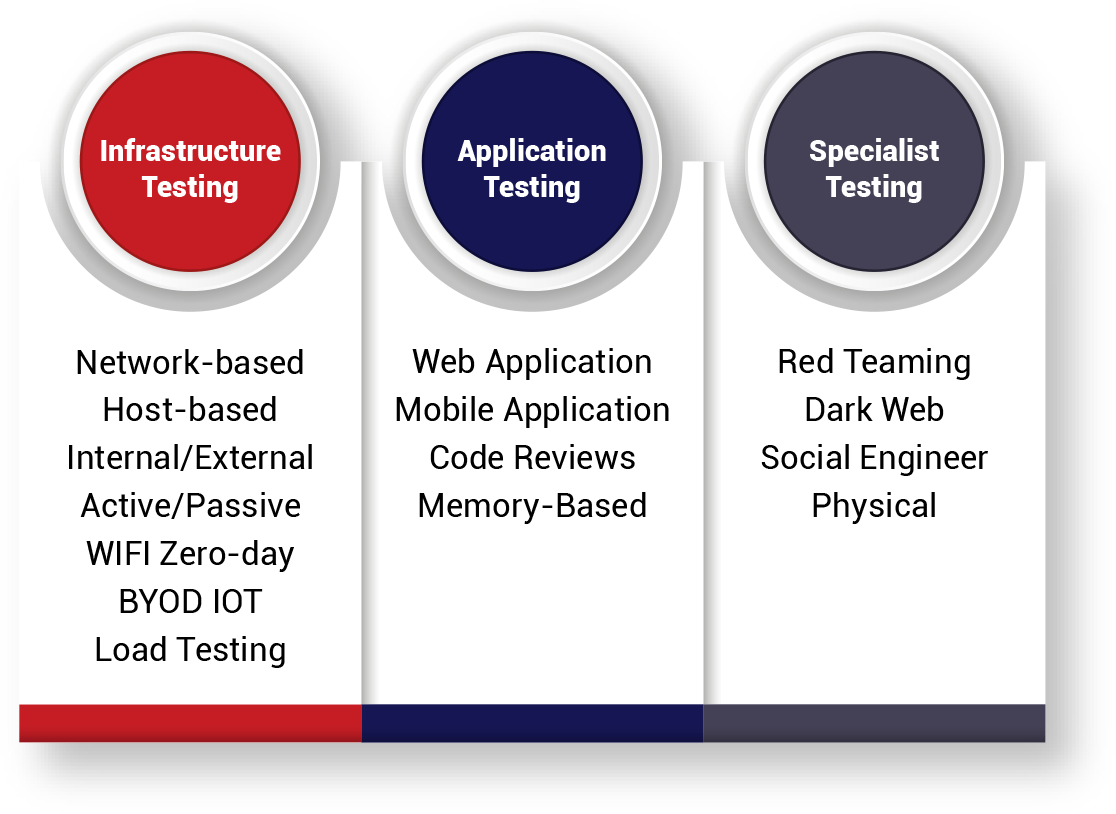
Security Testing Services
Our team of certified and accredited security professionals delivers a full range of security testing services which you can choose and customise to meet your specific testing needs.
Don’t leave yourself exposed. Find your weaknesses before cybercriminals do.