
Managed Endpoint Detection and Response (EDR)
Eliminate threats before they spread across your IT infrastructure
Managed Endpoint Detection and Response
We offer multi-layered protection for endpoints, cloud applications, email, web control and more, with extended Security Incident and Response Management capabilities. Our Managed Endpoint Detection and Response enables you to offer comprehensive coverage for small and mobile office productivity at a fraction of the cost.
Detection & Response Layer Protection
24x7x365 Managed Detection & Response
Event Investigation (SOC as a service)
MSCS Qualified Security personnel monitor and correlate alerts to establish a business need to recommend opening a security incident to respond to potential breaches requiring containment.
Retainer Free Incident Response
Acceptance of a request to proceed with Digital Forensic procedures will seek to contain, eradicate, and help clients recover from a breach. Responders work with all stakeholders in preparation for a response and provide situation reports along with a final after-action report which seeks to attribute actions and provide an evidentiary basis with which to prosecute.
Device Layer Protection
Windows, MAC OS, Linux, Android & iOS
Endpoint Security
Stop suspicious system behaviour (HIPS) and network attacks and block exploits in browsers and readers. Lightweight AV scanning pre, post, and during program execution. Scan system UEFI and Memory. Block password guessing, known ransomware and fileless attacks.
Vulnerability Shield
Improve detection of Common Vulnerabilities and Exposures (CVEs) on widely used protocols. Protects against vulnerabilities for which a patch has not yet been released or deployed.
Endpoint ANTI-Malware (LiveGuard Advanced)
Block new and developing ransomware, prevent zero-day exploits through file behaviour analytics and protect devices from any location with proactive analysis and tailored policy enforcement.
Endpoint Full Disk Encryption
Deploy encryption centrally for both windows and macOS. Protect information assets from device theft.
Device Control
Block unauthorized devices (CDs/DVDs and USBs) from your system. Enables you to create rules for user groups to comply with your company policies. Soft blocking – notifies the end user that his device is blocked and gives him the option to access the device with activity logged.
Distributed Service Layer Protection
Windows, Linux, Domino, Office365
Endpoint File & File Server Security
Protect servers like any other endpoint. Ensure only signed code is executed, plus monitor for botnet and malicious remote call behaviour.
Cloud Office365 Security
Anti-spam (user management), Anti-phishing, Anti-malware and automatic protection for new users in Exchange Online, OneDrive, Teams and SharePoint. Provide users with reports on quarantined items and allows for the administration of email content filtering conditions.
Traditional Mail Security
Anti-spam (user management), Anti-phishing, and Anti-malware support hybrid exchange, clusters, and the administration of email content filtering conditions.
Web Control
Limits website access by category, e.g., gaming, social networking, shopping, and others. Enables you to create rules for user groups to comply with your company policies. Soft blocking–notifies the end user that the website is blocked giving him the option to access the website with activity logged.
Managed EDR Protect Complete Partner

With remote working being the 'new normal', the ever-expanding technology perimeter has become difficult to monitor and threats hard to detect. Endpoints are your organisation's first line of defence and must be secured to avoid a security incident. Deploying an effective Endpoint Detection and Response solution is crucial to protecting both the remote and enterprise workforce from cyberattacks.
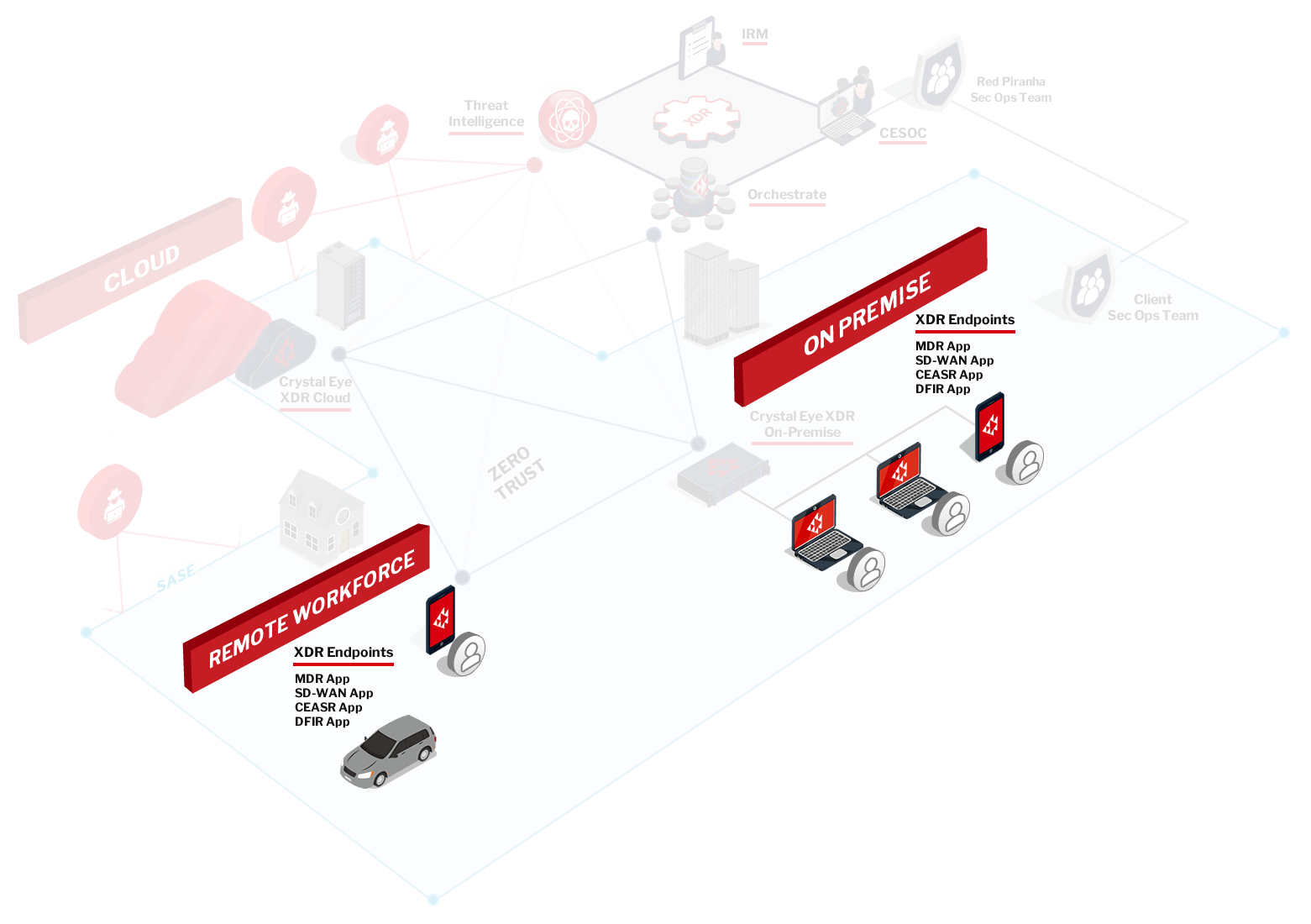
Crystal Eye EDR secure your endpoints across your corporate networks and your remote workforce.
Crystal Eye Endpoint Detection and Response is an integrated solution that delivers security protection,
threat detection and incident response capabilities. It includes the following components:
CEASR (Crystal Eye Attack Surface Reduction) App
The CEASR app reduces your attack surface with comprehensive endpoint protection. It locks down known weaknesses in your Windows working environment often exploited by malware, applying policies based on the Australian Government’s ASD Windows ISM Controls and allows organisations to meet Essential Eight guidelines.
SD-WAN (Software-Defined Wide Area Network) App
Provides remote users with a secure connection back to the corporate network to access cloud-based apps, corporate data and internet access. A key foundation of the Zero Trust Network Access (ZTNA) and Secure Access Service Edge (SASE) models allows you to securely extend your private networks for client-to-site and site-to-site communication over the public internet and to protect your cloud environments.
MDR (Managed Detection & Response)
Crystal Eye MDR captures events at the endpoints and sends the relevant data back to our SOC and centralised XDR data lake to correlate and report on relevant security activity and incidents. This forms the Endpoint Detection & Response (EDR) component of the overall XDR platform.
DFIR (Digital Forensics & Incident Response) App
DFIR offers host-based forensics by collecting and reporting on malicious activity across your devices and is complemented by our post-breach consulting to support rapid response during an outbreak. DFIR assists in understanding what has occurred during a breach, such as identifying the source and perpetrator of the attack. It delivers a cost-effective solution for responding to an outbreak at a fraction of the typical cost.














