CEASR App
Crystal Eye Attack Surface Reduction
 Protect your endpoints from evolving threats with the CEASR App
Protect your endpoints from evolving threats with the CEASR App
Remote work has significantly accelerated the adoption of cloud solutions and increased the reliance on effective endpoint protection.
As the threat landscape is evolving so rapidly, antivirus software is becoming less effective, and it’s critically important to be analysing malicious behaviours on the endpoints – not just looking at signatures. Fileless attacks are now a common component of most malware types, making behavioral protection at the endpoint a critical capability; however, Endpoint Detection & Response (EDR) is deployed to only 40% of endpoints in the market.
Red Piranha’s CEASR App reduces your attack surface with comprehensive endpoint protection, all integrated into our XDR platform. It achieves this by locking down known vulnerabilities on your endpoints and applying policies based on the Australian Government’s ISM and Essential 8 guidelines.
Your attack surface includes all the places where an attacker could compromise your network. With so many staff working from home, the endpoint is an increasingly exposed part of the attack surface for many organisations, with around 80% of attacks coming through the endpoint.
CEASR monitors and blocks suspicious software behaviors on endpoints via a range of methods.
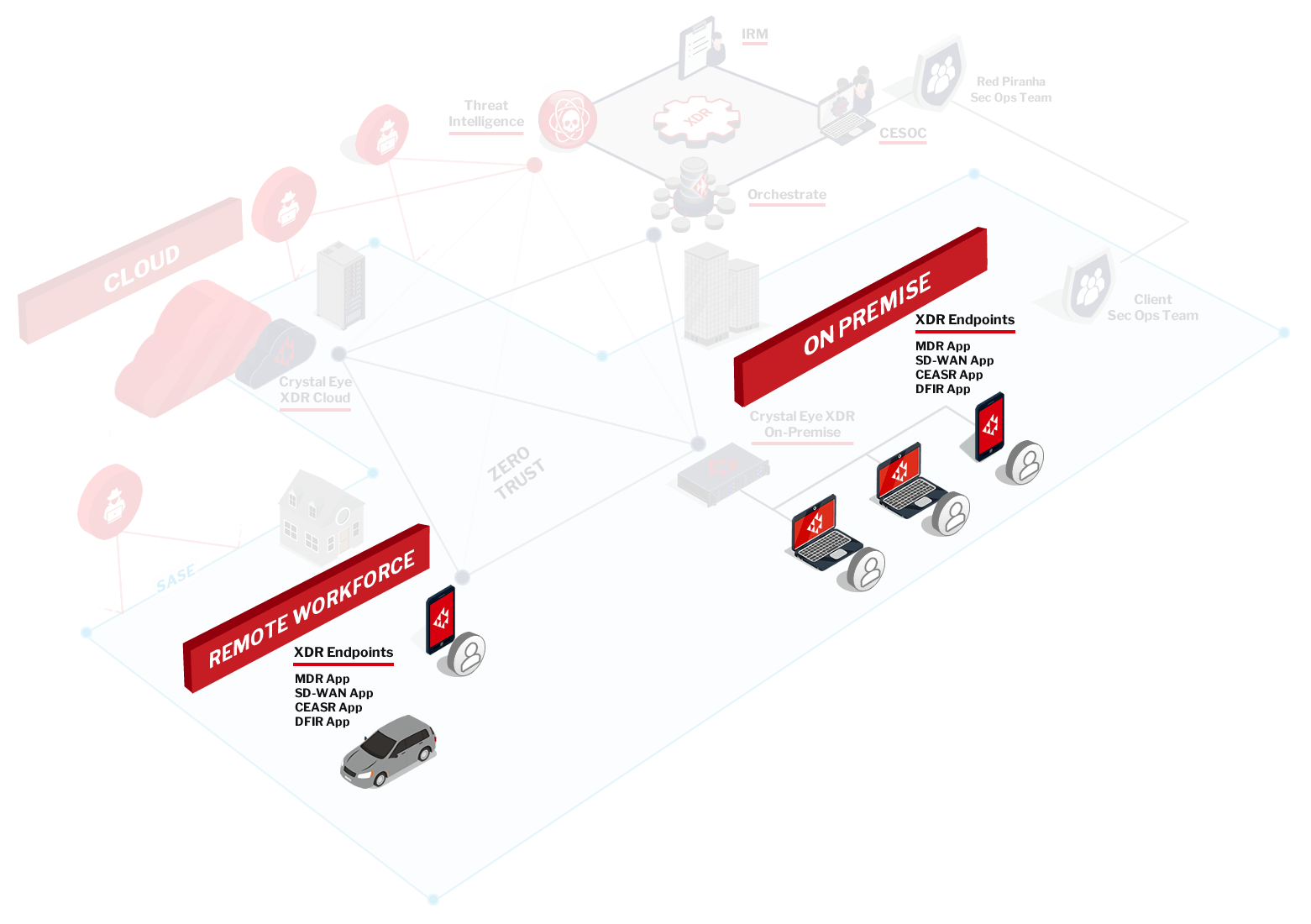
Crystal Eye Attack Surface Reduction (CEASR) App Features
- Prevent suspicious applications, files and scripts that attempt to download or run unknown or malicious files
- Apply behavioural analysis to detect and prevent threats at the endpoint
- Block third-party applications like Microsoft Office or Adobe Reader from creating and running child processes
- Prevent file-based and file-less malware from abusing WMI to attain persistence on a device
- Control removable media like USB by blocking unsigned processes
- Protect against web-based threats by blocking outbound processes on the device from untrusted sources
- Protect confidential data from ransomware activities by blocking untrusted processes from accessing protected folders
- Detect changes across your network and alerting any new subdomains and domains attaching to your attack surface
- Gain visibility over your entire attack surface, including activity, open ports, SSL certificates and more
- Device application whitelisting to prevent unwanted applications from running
- Integration into our DFIR App to provide advanced, on-demand incident response capabilities
CEASR integrates into the Integrated Risk Management (IRM) component of our XDR platform, so policies can be centrally-managed, which provides you with visibility on your compliance status across your attack surface at any time. CEASR provides greater visibility of security events occurring out at your endpoints, enabling you to detect and respond to malicious threats more rapidly.
By applying policies to lock down endpoints and gaining real-time visibility of the current status of those endpoints, you significantly reduce your attack surface exposed to threat actors and thereby reduce your overall business risk profile.

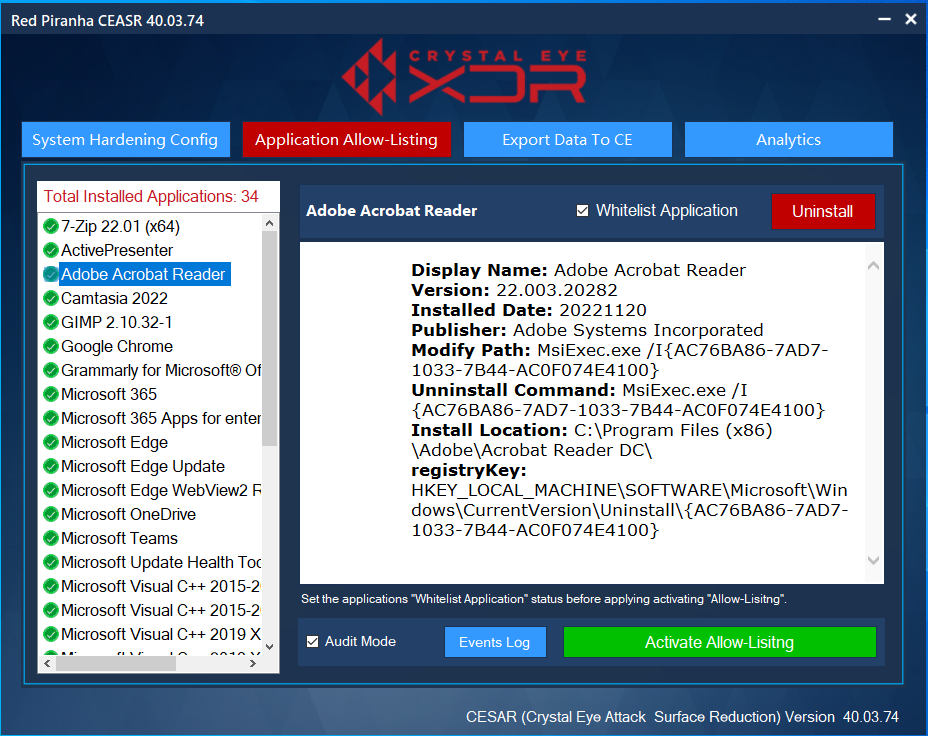
Application Allow-Listing
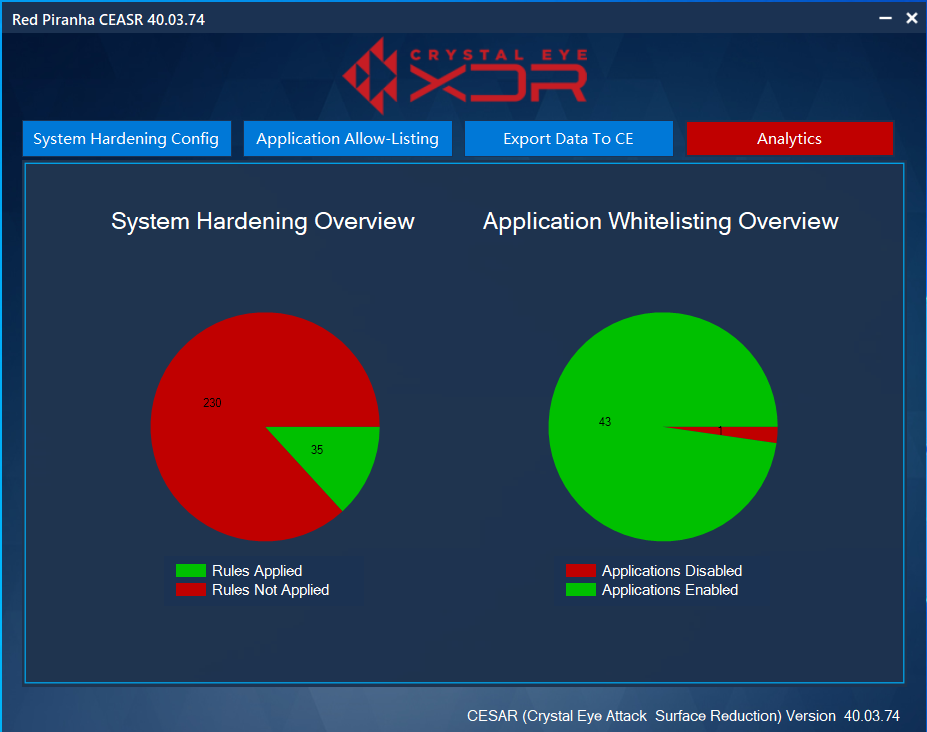
Device Reporting
Learn how a Crystal Eye deployment in conjunction with the Crystal Eye Attack Surface Reduction (CEASR) application installed on endpoints facilitates application control and ensures compliance with several cyber security frameworks including some of the more challenging application allow listing requirements of Essential 8 Maturity Level 3.
Watch our YouTube webinar:
Talk to our experts and know how Crystal Eye Attack Surface Reduction CEASR App can secure your organisation from the cloud to the endpoint, today.
