Endpoint Detection and Response (EDR)
Eliminate threats before they spread across your IT infrastructure
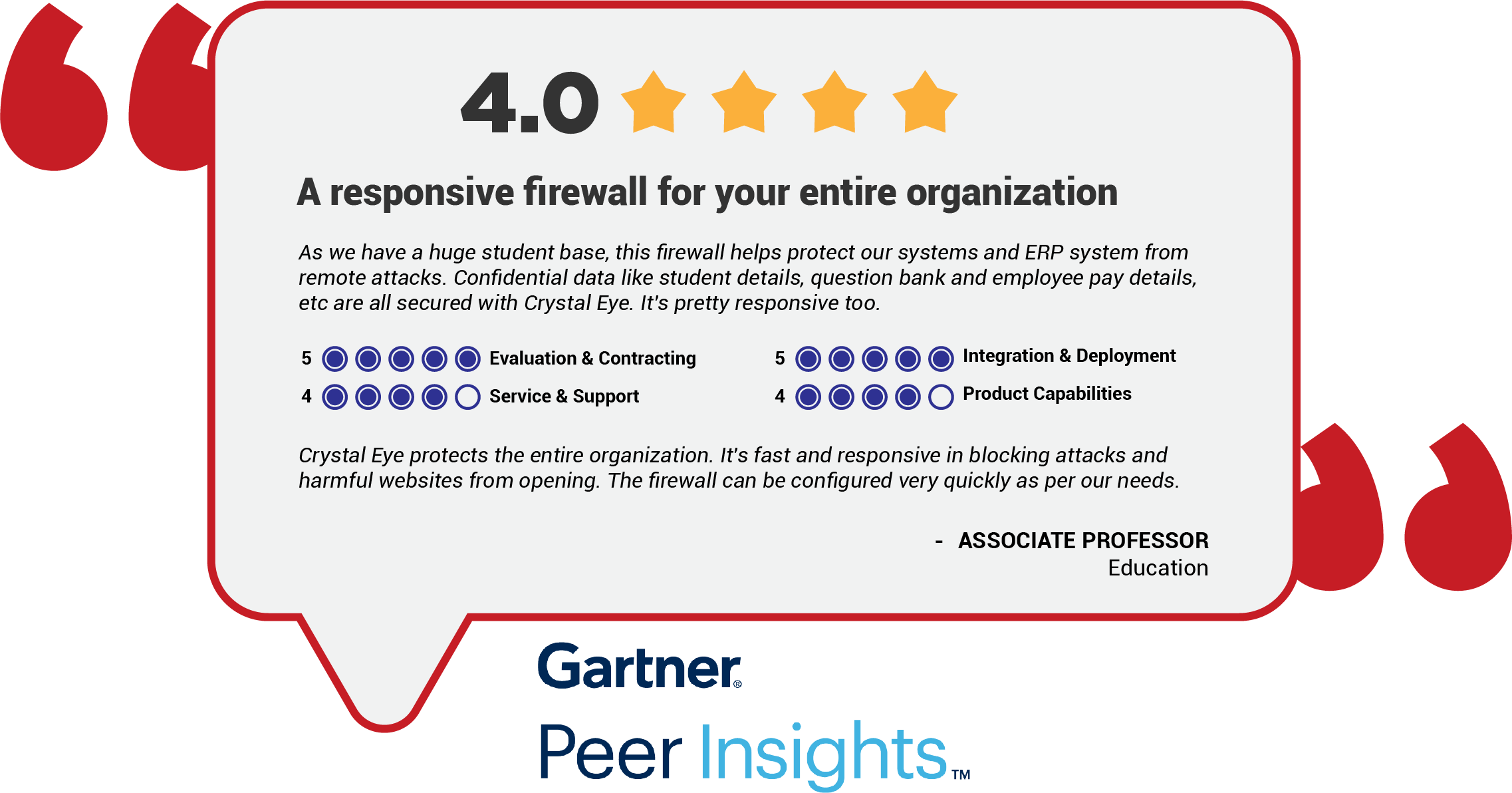
Managed Endpoint Detection and Response Protect Complete
We offer multi-layered protection for endpoints, cloud applications, email, web control and more, with extended Security Incident and Response Management capabilities. Our Managed Endpoint Detection and Response Protect Complete enables you to offer comprehensive coverage for small and mobile office productivity at a fraction of the cost.
Detection & Response Layer Protection
24x7x365 Managed Detection & Response
Device Layer Protection
Windows, MAC OS, Linux, Android & iOS
Distributed Service Layer Protection
Windows, Linux, Domino, Office365
Managed Endpoint Detection and Response Protect Complete Partner

With remote working being the 'new normal', the ever-expanding technology perimeter has become difficult to monitor and threats hard to detect. Endpoints are your organisation's first line of defence and must be secured to avoid a security incident. Deploying an effective Endpoint Detection and Response solution is crucial to protecting both the remote and enterprise workforce from cyberattacks.
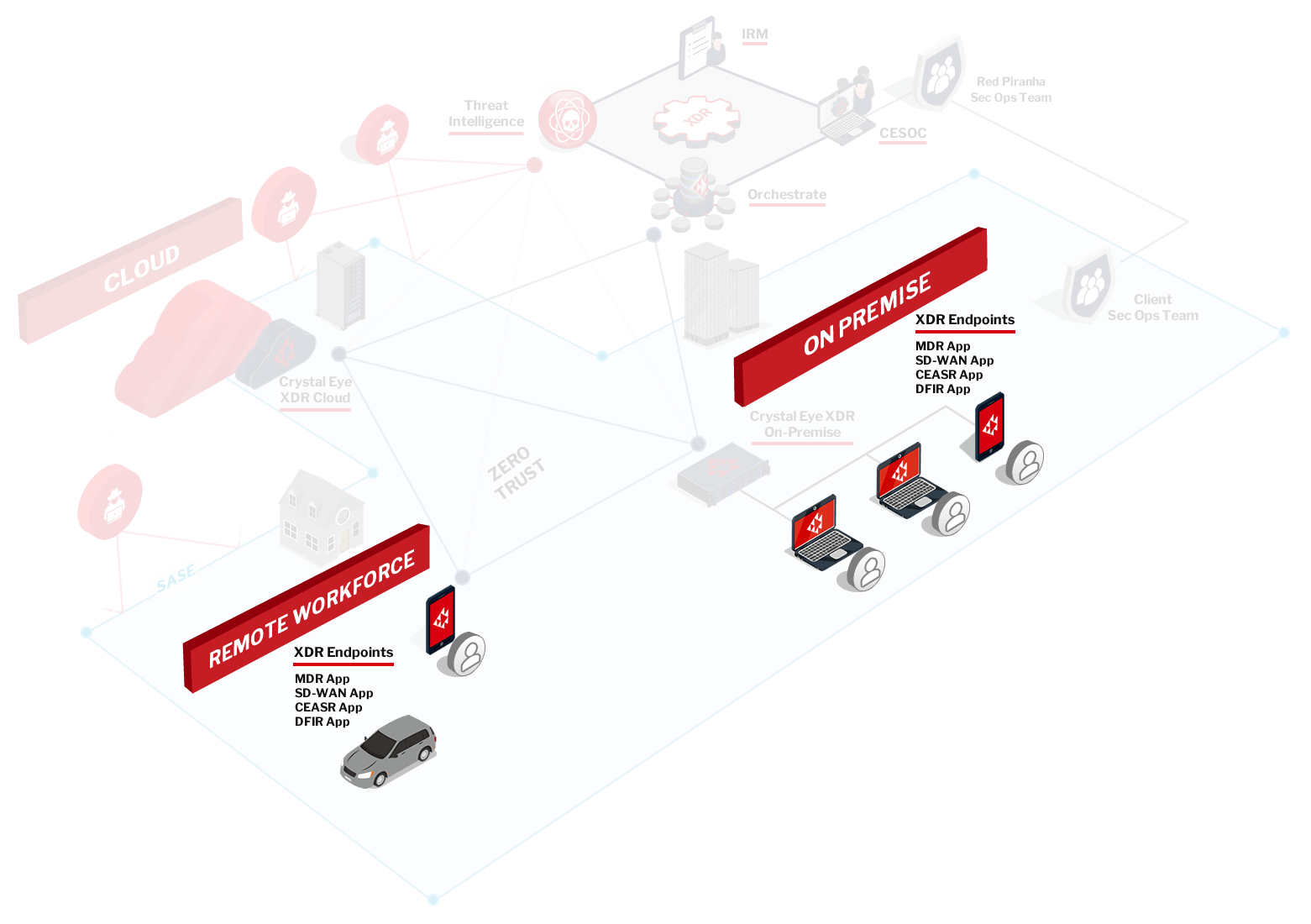
Crystal Eye EDR secure your endpoints across your corporate networks and your remote workforce.