INTEGRATED RISK MANAGEMENT
Integrated Risk Management (IRM) is a critical part of an effective Cybersecurity Program
Cyber risk is an unacceptable risk to business, with the average total cost of data breach reaching US$4.45 million in 2023. An Integrated Risk Management program is essential to avoiding major disruption to business operations.
 Comprehensive Security
Comprehensive Security
Crystal Eye's Integrated Risk Management capabilities provide a holistic view of enterprise risk from a single pane of glass.
 Reduce Resource Costs
Reduce Resource Costs
Utilise Red Piranha's village of security specialists to keep your business secure and compliant without investing in large internal teams.
 Cost-Effective Compliance
Cost-Effective Compliance
Our eCISO™ service delivers the benefits of having a Chief Information Security Officer for a fraction of the cost.
Problems
- Security incidents are becoming more complex and more commonplace. Many organisations struggle to implement effective security controls and don't understand how to measure and manage enterprise risk.
- Running a complete security program currently requires a mix from multiple products with significant integration effort. This leaves most organisations needing to compromise on their security or being left with poorly-configured systems that aren’t providing effective protection.
Solution
- A more progressive approach to security is required to overcome these issues with a simple, unified platform that can effectively protect, detect and respond to risks across your whole organisation.
- This approach delivers a unified solution with risk management capabilities integrated directly into the platform.
Integrated Risk Management (IRM)
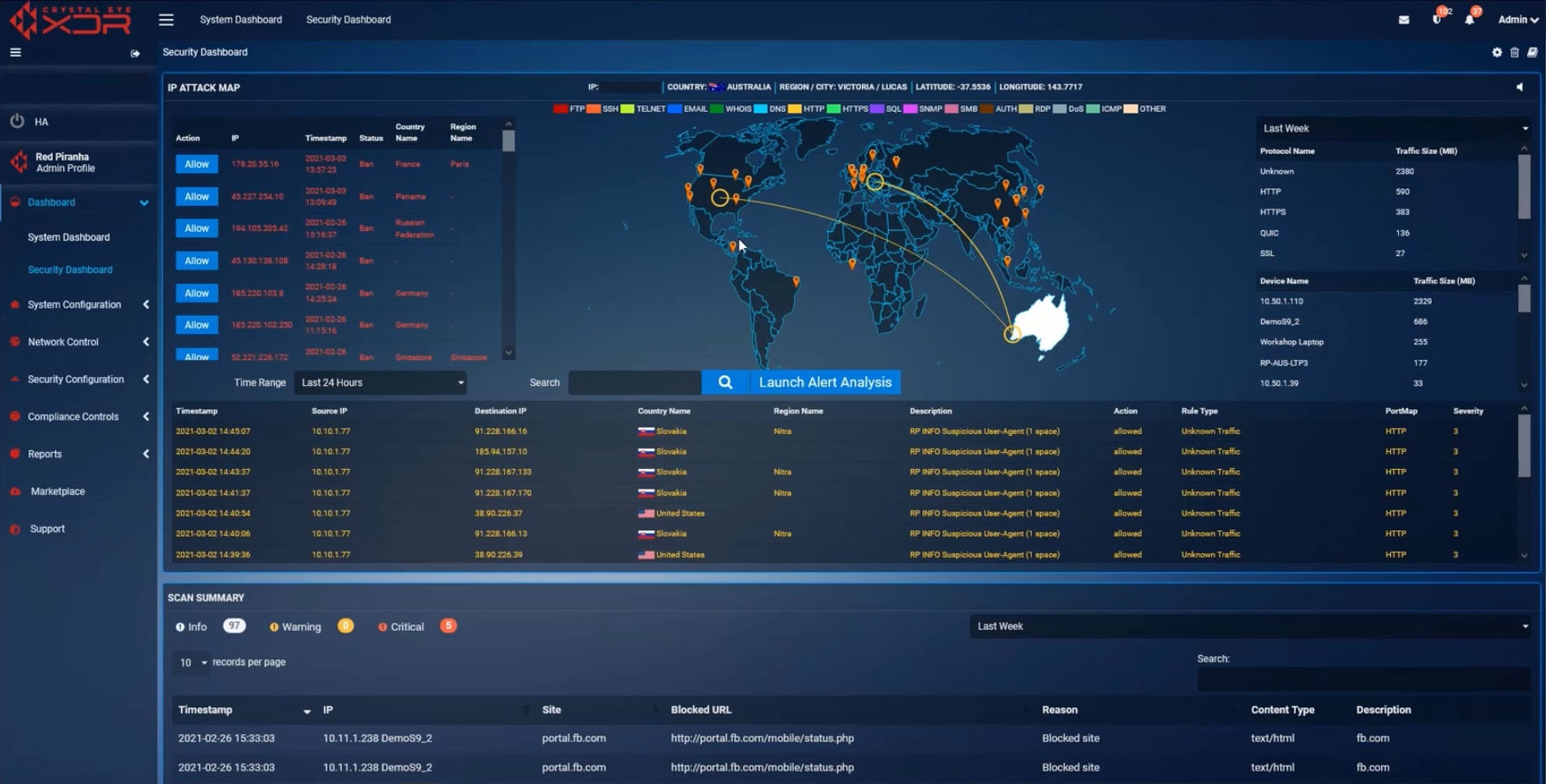
The Crystal Eye Integrated Risk Management solution provides an automated and integrated approach to meeting your compliance obligations. It pulls together relevant compliance information and controls from multiple points across your network into a central dashboard that allows you to manage and report on that information to ensure you're compliant to a range of standards and provides a snapshot of your compliance posture at a point in time. The key compliance areas it addresses include:
- Security Policy Management
- Security Awareness Training
- Identity & Access Management
- Vulnerability Management
- Security Monitoring
- Incident Response
- BCM / DR
The compliance journey can be a pain-staking process that requires a log of investment in time and resources. Our IRM capability automates the majority of the work required to achieve and maintain compliance, thereby significantly reducing the cost for your business to gain a competitive edge in the market.
We also offer our eCISO (electronic Chief Information Security Officer) solution which integrates into the Crystal Eye platform as well as our vCISO (virtual Chief Information Security Officer) service which is a standalone service to deliver a comprehensive approach to Integrated Risk Management.
Compliance Controls
- Integrated Risk Management
gives you better control of your risk profile in real-time, by providing visibility of your entire organisation from on-premise staff to your remote workforce. - Data Loss Prevention (DLP)
allows you to tag documents within your environment and track if they are being copied or removed from your network as well as VOIP monitoring to minimise the likelihood of data being exfiltrated out of your organisation. - Vulnerability Management
covers vulnerability scanning and reporting as well as pro-active protection measures such as virtual patching to provide zero-day protection and reduce the operational burden on IT staff. - Incident Response
services seamlessly integrate alerts into Red Piranha’s managed services and professional services to provide rapid response to security incidents that occur across your network in real-time.
Integrated Vulnerability Management
Crystal Eye offers vulnerability tuning within the IDPS engine to provide virtual patching against known vulnerabilities identified in your environment, which is further supported by multi-function deployment options such as the Web Application Firewall.
The minute you install Crystal Eye, it shows you the number of vulnerabilities that have been detected in your specific environment, then it shows you how many have exploits which was leaving you at risk and how many are now being protected by Crystal Eye.
The objective here is to focus on the small number of vulnerabilities, not just the large number of malware that exploit those vulnerabilities.
Security Controls
- Encrypted traffic metadata detection
running on our multi-threaded, high-throughput engine delivers unrivalled network protection against both clear and encrypted threats without decrypting traffic. - Integrated functions
work together intelligently, such as the IPS dynamically creating a firewall rule when it detects multiple attacks from the same IP address, to automatically block that address to shut down the attack source and reduce the load on the IPS engine. - Zero Trust Network Access (ZTNA)
is a security architecture that ensures only traffic from authenticated users and devices are granted access to applications. It reduces the risk of a data breach via a comprehensive approach which includes identity verification, user access control and network segmentation. - Cloud Access Security Broker (CASB)
delivers network-based and cloud-based security policy enforcement between users and cloud services via network segmentation to provide protection of SaaS applications. - Identity & Access Management (IAM)
provides greater control of users on your network and forms a critical part of ZTNA and CASB protection. Crystal Eye offers a standalone Active Directory (AD) instance or can be integrated with an existing AD using LDAP or OAuth. - Agentless Application Whitelisting (AWL)
blocks unwanted apps at the gateway to prevent them running on devices within the network. - DNS.Insure
provides DNS sink-holing and managed DNS to deliver advanced DNS protection across the network and bringing DNS back under enterprise control, increasing network visibility and control. - ForceField
identifies authentication failures across the network and blocks the source IP addresses of the failed login attempts to prevent brute force attacks and unauthorised access to systems. - Zero-day Protection
is delivered via our IPS engine which supports both vulnerability-facing signatures and threat-facing signatures to provide a more comprehensive level of protection. - BYOD & IoT devices are protected with application filtering and protocol filtering at the gateway and network segments. On-premise protection is critical to cater for the expansion of IoT & BYOD across the enterprise. Our extensive security configuration capabilities deliver contextualised data across multiple security features dealing with encrypted traffic, including application-layer controls to manage IoT and BYOD to provide total visibility of the threats on your network.
- VoIP monitoring
allows you to take control of voice traffic and Machine Learning will generate alerts when anomalies are detected. As the popularity of VoIP systems increases, they are being subjected to different kinds of intrusions, some of which are specific to such systems and some of which follow a general pattern of attacks against IP infrastructure. This app will monitor all VoIP traffic on your system. - Deception
capabilities allow you to create traps within your infrastructure by tagging decoys to trick attackers within your network for detection and notifications from internal attack vectors. - Machine Learning (ML)
delivers a range of automated defence features using defined playbooks to get you secure and compliant with little or no human intervention. - User & Entity Behaviour Analytics (UEBA)
uses ML to define behaviour profiles across network authentication (Kerberos), server connections (SSH) and file management (SMB) then alert when anomalies are detected to prevent attack pivoting. - Threat Analysis & Threat Hunting
is achieved by integrating various detection methods across the Crystal Eye platform to allow your security team, or ours, to pro-actively search security breaches, as well as being able to automate the threat hunting process via the platform. - PCAP
provides full packet capture (PCAP) support which allows for greater control and easy analysis. - Security Plan Wizard
guides novice users through the configuration of the Cystal Eye platform to simplify the setup and configuration process and can be used in conjunction with the risk audit functionality. - Backup PC
allows single nodes to use the Crystal Eye appliance for a local backup solution to simplify the backup and restore process.
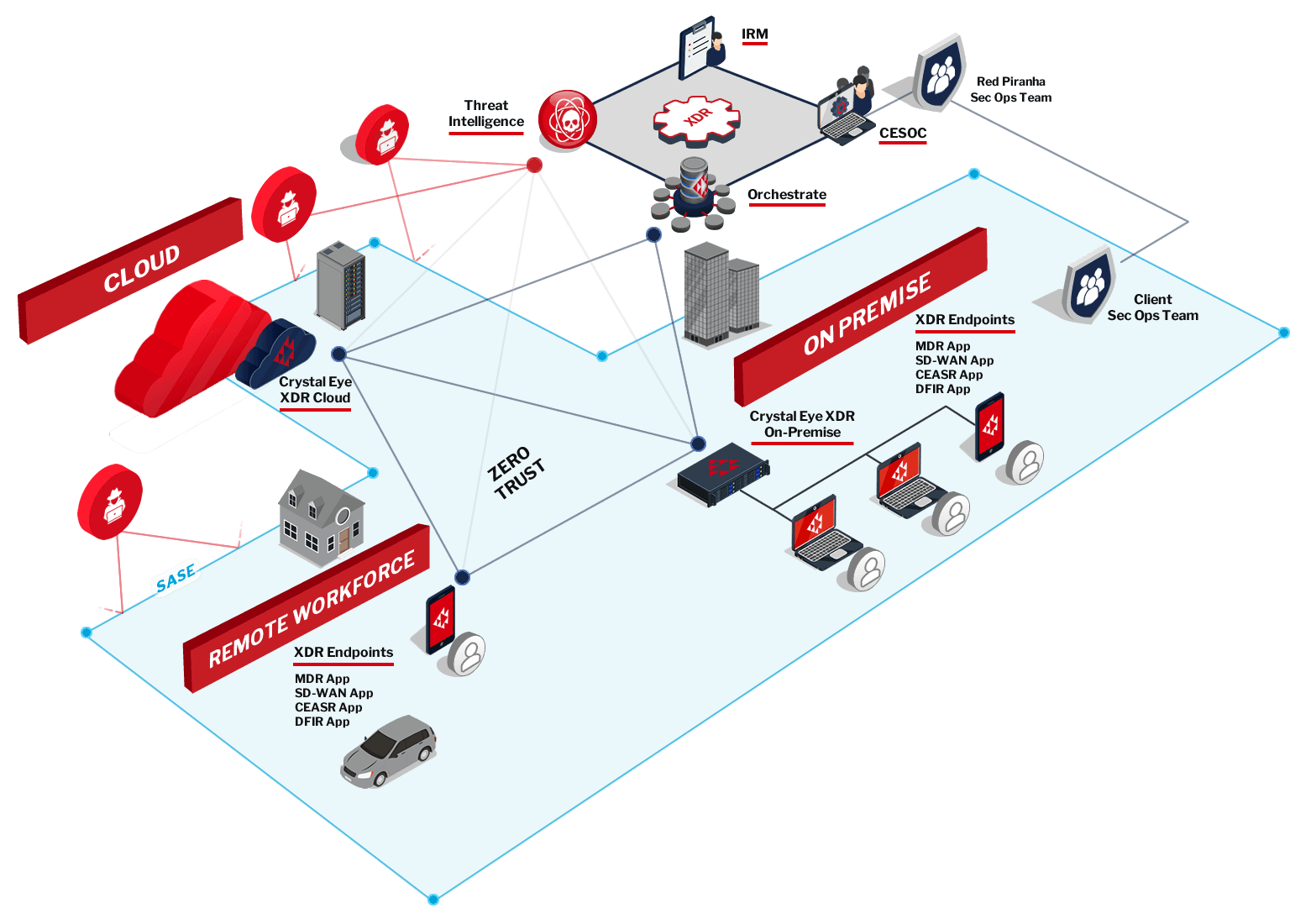
eXtended Detection & Response (XDR)
Integrated Risk Management is part of our overall Crystal Eye XDR platform, which is an integrated security protection, threat detection and incident response solution. It involves the collection and correlation of event data from multiple security technologies that automatically trigger a coordinated response to secure your network. This all-in-one platform is pre-configured to be ready to go out-of-the-box, so it delivers a consistent level of security across your whole environment without the complexity of integrating products from multiple vendors. The key areas of an XDR solution are:
- Automated security protection
- Centralised data collection and correlation
- Coordinated and automated incident response
Crystal Eye XDR Features:
Passive Encryption Control
Our Advanced Passive Encryption Control technology protects networks with application-specific fingerprinting to establish traffic baselines allowing you to secure your network even with IoT devices present.
Azure AD
Use your Crystal Eye XDR appliance to capture extended Microsoft 365 signals useful in threat detection with all Microsoft subscription levels, usually reserved for corporate subscribers only.
Wireguard
Crystal Eye XDR appliances also support the faster and more secure WireGuard protocol as well as traditional VPN technologies like SSL and IPSec.
Threat Hunting
Gain visibility and in-depth information and signals around your network to efficiently detect and locate threats or potential threats in your network with our comprehensive Threat Hunting Dashboard.
The Crystal Eye Difference
Crystal Eye delivers a range of unique benefits across our entire platform. Traditional firewalls focus on security protection, while Crystal Eye’s range of solutions offer automated protection, automated detection and automated response to security threats across your organisation:
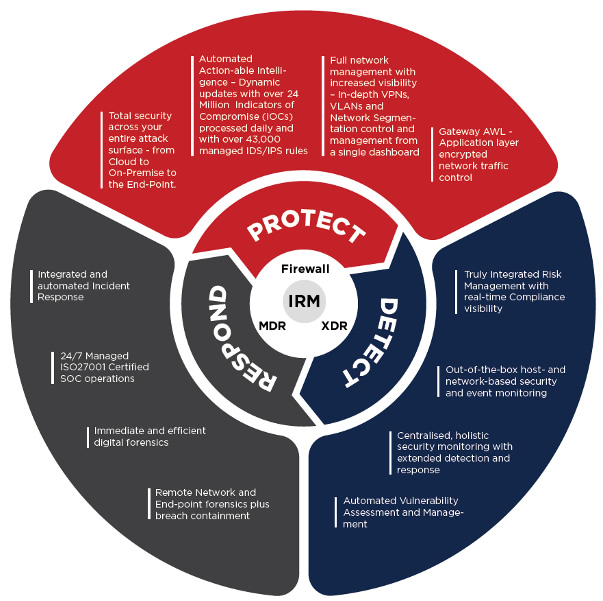
XDR
MDR
IRM
Crystal Eye Orchestrate
CE Orchestrate is the central management console that allows for monitoring and tuning of the Crystal Eye platform from a single interface for single and multi-tenanted scenarios at scale. Much more than just a dashboard – it’s the central component in delivering Security Orchestration, Automation & Response (SOAR) across your environment which enables you to protect the confidentiality, integrity and availability of your data.
SOAR
SASE
ZTNA
The multi-tenanted capability also allows MSPs to manage multiple clients from a single view to browse, filter and view clients by various metrics and track scheduled tasks. The dashboard also integrates into the IRM module to manage critical security and compliance reporting.
CE Orchestrate provides a single view of all of your Crystal Eye devices and endpoints with a holistic view of all your security events and alerts. You can drill into any alert or alarm to see more detailed alert analysis, alert escalation and reports for further investigation. You can also edit the rule action directly from the alert allowing for more granular tuning of the system.
SASE – Secure Access Service Edge
With more applications and data in the cloud and more staff working remotely, there is an increased need for simple and secure access for users in any location to access services in any environment. SASE is an architecture which aims to solve this problem by extending the bounds of the traditional security perimeter by deploying networking and security functionality at the business operational edge. It integrates multiple network security technologies such as SD-WAN, application-level access control and security policy enforcement. Crystal Eye integrates our network protection with our endpoints apps to provide strong protection both on-premise and out to remote devices.
SASE is the convergence of network and security as a service into a single stack that allows organizations to secure users and devices accessing any service in any location. Bi-directional, single pass security inspection of traffic allows organisations to decrypt once and apply security controls such as advanced threat protection, DLP and application control to the connection.
Crystal Eye SASE can be deployed in localised regions to create local points of presence (POPs) to establish a SASE environment. Crystal Eye offers multiple options in Australia and globally to achieve this. Crystal Eye is cloud agnostic, supporting AWS, Azure and other cloud environments to give you flexibility.
Crystal Eye XDR Endpoints
SD-WAN App
- Provides remote users with a secure connection back to the corporate network to access cloud-based apps, corporate data and internet access.
- A key foundation of the Zero Trust Network Access (ZTNA) and Secure Access Service Edge (SASE) models allows you to securely extend your private networks for client-to-site and site-to-site communication over the public internet and to protect your cloud environments.
- Captures events at the endpoints and sends the relevant data back to our Security Operations Centre (SOC) and centralised XDR data lake to correlate and report on relevant security activity and incidents.
- This forms the Endpoint Detection and Response (EDR) component of the overall XDR security platform.
- Ensures devices on your network conform to security policies based on standard security frameworks such as the Australian Signals Directorate's Information Security Manual (ISM) and the Essential Eight guidelines.
- Apply operating system policies across a range of devices and provide ongoing device monitoring to keep track of your compliance baseline in real-time.
- Offers host-based forensics by collecting and reporting on malicious activity across your devices and is complemented by our post-breach consulting to support rapid response during an outbreak.
- Assists in the efforts of understanding what has occurred during a breach, such as identifying the source and perpetrator of the attack.
- Delivers a very cost-effective solution for responding to an outbreak, at a fraction of the typical cost.
An Integrated Approach
The Crystal Eye platform delivers a comprehensive solution across a range of security areas, with the whole platform working together to protect, detect and respond to threats in your environment. Together, this all works to provide a new level of threat protection, all integrated into a single defence-in-depth platform.
Our modular approach can be catered to meet the needs of each company, so you can pick and choose what matters most to you without implementing the whole solution. At the end of the day, it's not just about the technology – it's about managing risks specific to your needs. No matter what your budget or your capacity is, we have a solution to address your needs from SMBs to enterprises.
This is a conversation about managing security risks, not just deploying technology for technology's sake. We recommend starting with defining your required level of assurance, then looking at the most relevant solutions to achieve that.
Pricing
Crystal Eye solutions are available in a range of options to suit every budget.