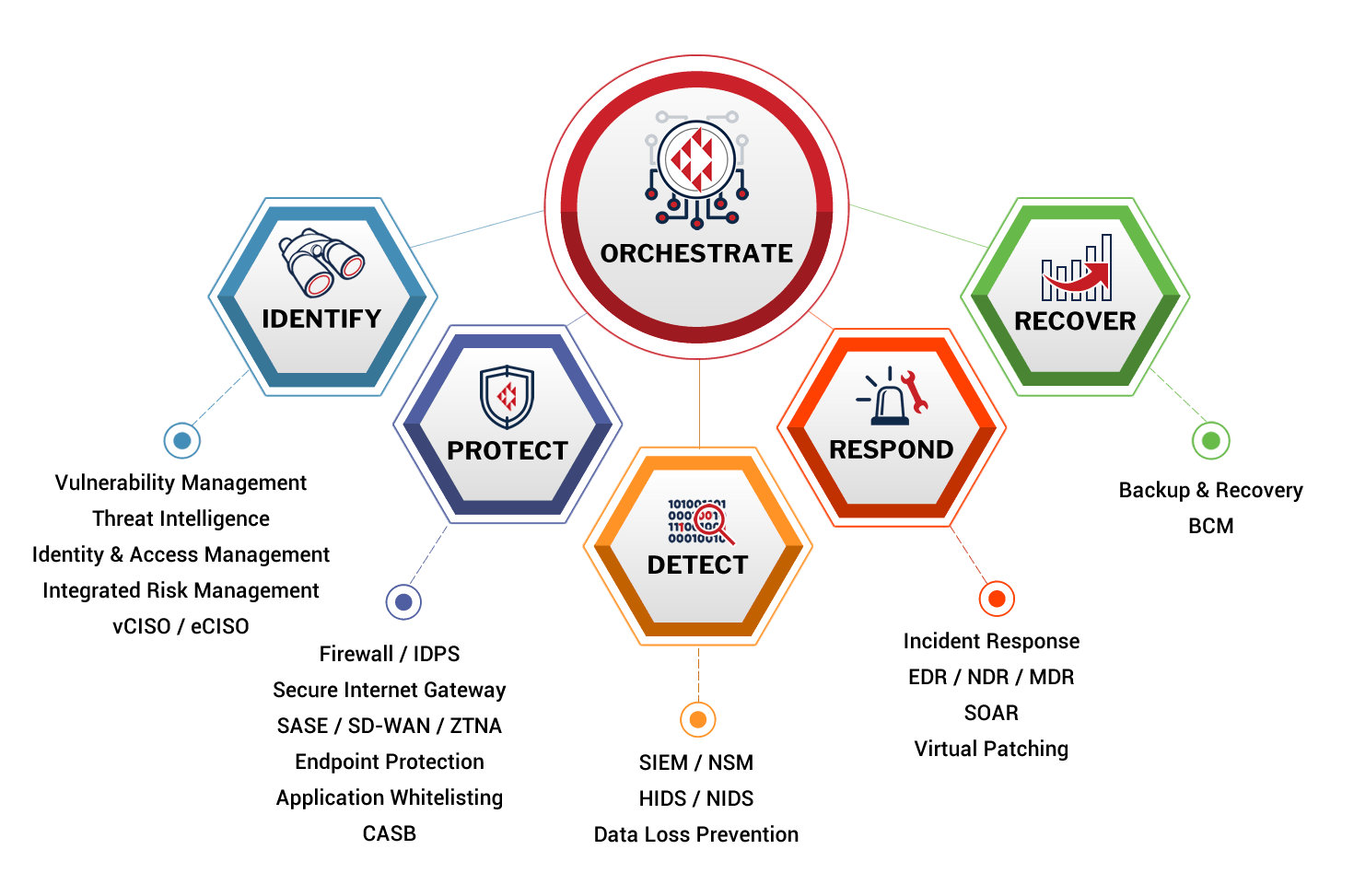
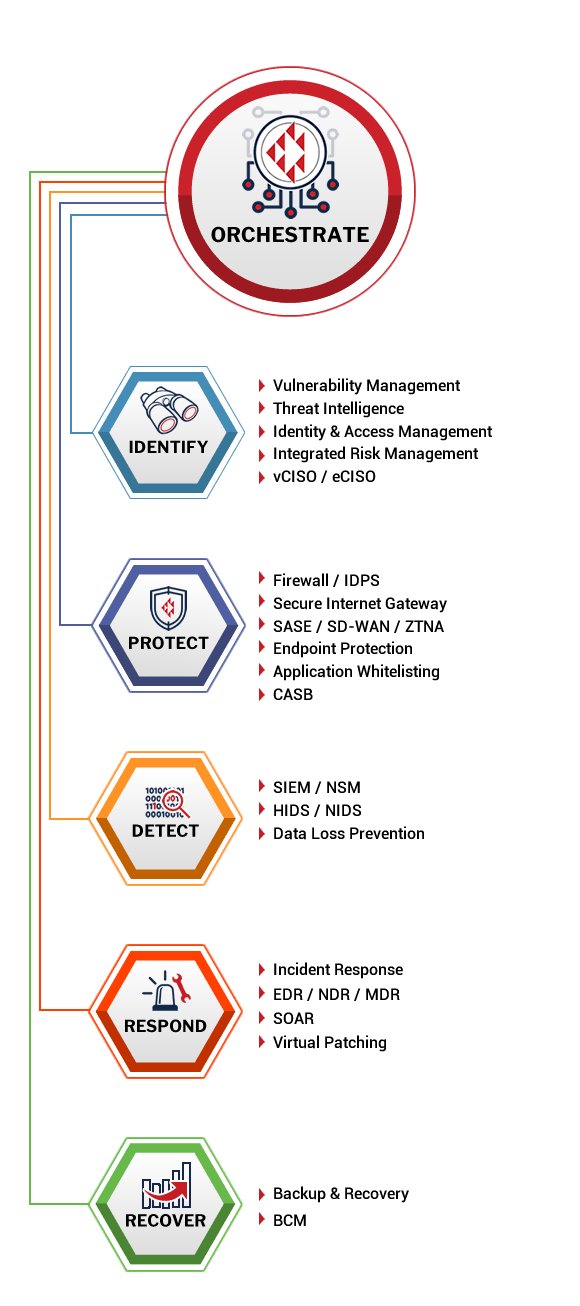
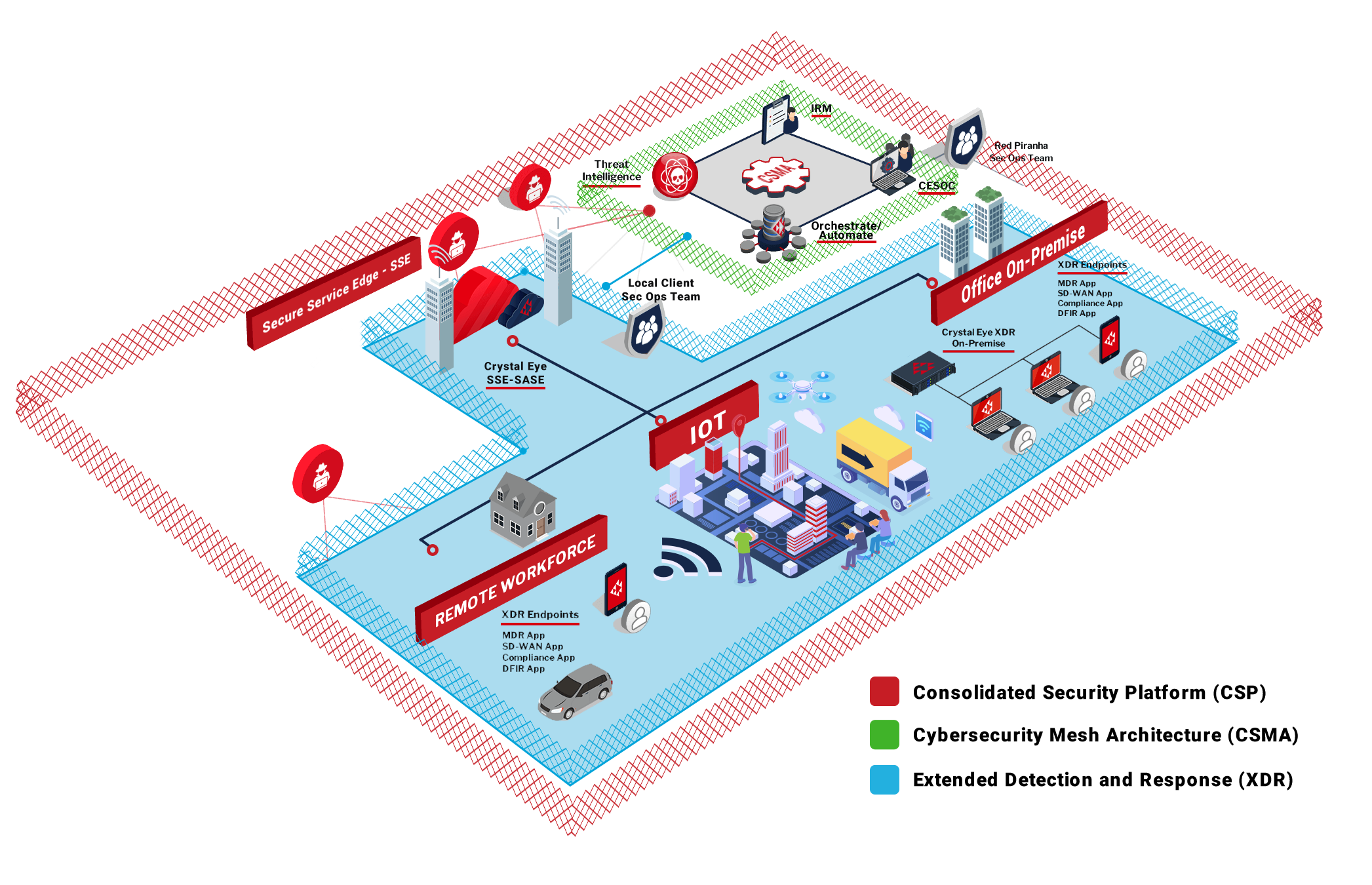
Crystal Eye XDR (Extended Detection & Response) is a new approach that provides end-to-end security
all from a single integrated platform.
Learn More:
SIMPLE. SECURE. COMPLIANT.
Crystal Eye secures your organisation from the cloud to the endpoint
with a range of advanced security technologies.
News and Events
In this report, we discuss three new threats - DoNot Group (APT-C-35), Colibri Loader Malware, and Gomorrah Stealer Malware. In the past week, our team uncovered new ransomware victims or updates on previous victims across 20…
In this report, we discuss three new threats - RomCom RAT, Erbium Stealer and Parallax RAT. In the past week, our team uncovered new ransomware victims or updates on previous victims across 21 industries spanning 20 countries. Also,…
In this report, we discuss three new threats - WarzoneRAT, Xehook Stealer and Lumma Stealer. In the past week, our team uncovered new ransomware victims or updates on previous victims across 16 industries spanning 18 countries. Also…









 Reduce risk
Reduce risk