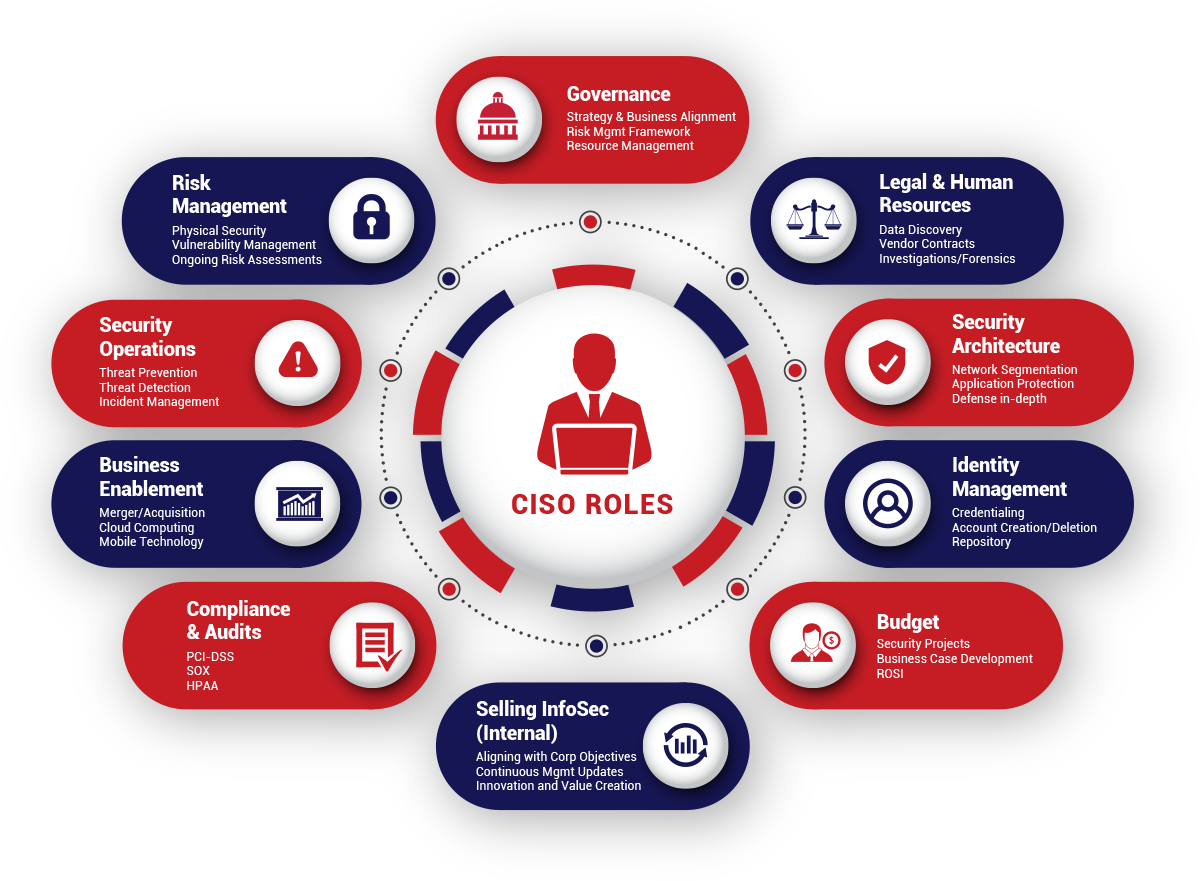
CISO Services
Red Piranha's eCISO and vCISO program is a combination of people, processes and technology that delivers a range of security outcomes to protect your business and achieve compliance at a fraction of cost.
With an eCISO™ or vCISO shouldering your security planning and reporting responsibilities, you and your team are free to focus on more strategic activities instead of putting out fires.
A dedicated CISO with cutting-edge technology, complemented by remote consulting, seamlessly integrated with our
Crystal Eye-Consolidated Security Platform, helps develop a detailed information security program and produce in-depth compliance reports.
Chief Information Security Officer (CISO) Services
Red Piranha offers flexible CISO Advisory packages delivered through our ISO/IEC 27001 certified security operations centres tailored to meet your organisation’s needs:
 eCISO™ (Remote)
eCISO™ (Remote)
Remote consulting services from our village of cybersecurity professionals to deliver a range of critical tasks and help businesses develop and maintain a comprehensive information security program.
 vCISO (On-site & Remote)
vCISO (On-site & Remote)
Our virtual CISO solution gives you on-site and remote access to our pool of highly experienced security experts to build and roll-out your security program and meet your reporting requirements.
 Compliance
Compliance
Businesses are under increasing pressure to meet a range of compliance requirements including ISO/IEC 27001, PCI and HIPAA. By establishing the right foundation with our CISO services, you can be better equipped to stay on top of your evolving compliance needs.
 Vulnerability Management Framework
Vulnerability Management Framework
 Human-Machine Teaming
Human-Machine Teaming
Automating critical processes, interrelated technologies, and human processes with the help of Crystal Eye platform. Gain access to the village of security analysts and experts to undertake on-demand threat hunting and other security related capabilities not usually available without significant investment.
 Cyber Security Awareness Training (CSAT)
Cyber Security Awareness Training (CSAT)
Delivered via the Red Piranha training platform, security training helps reduce liability through awareness of responsibilities to uphold policies designed to address cyber risks.
 Dedicated Qualified Risk Officer
Dedicated Qualified Risk Officer
Your Risk Advisor is appointed to work with your team and assist your organisation assess risks and deal with necessary improvements related to your Information Security Management Systems (ISMS). They provide access to and assistance with ISMS policy templates to drive security strategy and meet compliance frameworks.
 Continuous Threat Exposure Management (CTEM)
Continuous Threat Exposure Management (CTEM)
Our Continuous Threat Exposure Management (CTEM) program is a sustainable approach to a multiyear initiative with cross-team collaboration that helps organisations move beyond only tactical and technical remediation to reduce long-term impact. A repeatable cycle of a five steps process — scoping, discovery, prioritisation, validation and mobilisation for consistent and efficient security outcomes.
 Cyber Security Review (CSR)
Cyber Security Review (CSR)
This annual report gives a high-level review of your current technology stack and a cyber risk rating for your business. It will help you understand your security posture and prioritise resources, budgets and clear next steps to close cyber risk gaps, focusing on maturity and continual improvement.
 ISMS Incident Response System
ISMS Incident Response System
Crystal Eye’s embedded Digital Forensics & Incident Response (DFIR) technology allows out-of-the-box Incident Response ISMS policy and procedure and includes access to people, process and playbooks. Our Incident response and SecOps Analyst Escalation delivers immediate capability to the organisation to deal with initial indicators of compromise, reducing the potential of risk and loss in the event of a breach.
An eCISO™ or vCISO can also help set security strategies, procure solutions, remediate incidents, and put foundations in place for your compliance needs. They may also assist with bring-your-own-device (BYOD) policy and enforcement as well as managing your board-level responsibilities.