Crystal Eye XDR
eXtended Detection and Response
Address cybersecurity challenges with our Consolidated Security Platform

Protect your entire IT and
OT infrastructure
Detect, Investigate and Respond to
Threats with Best-in-Breed Technology
Integrated approach with better
Total Cost of Ownership (TCO)
Improve Security Team
Productivity
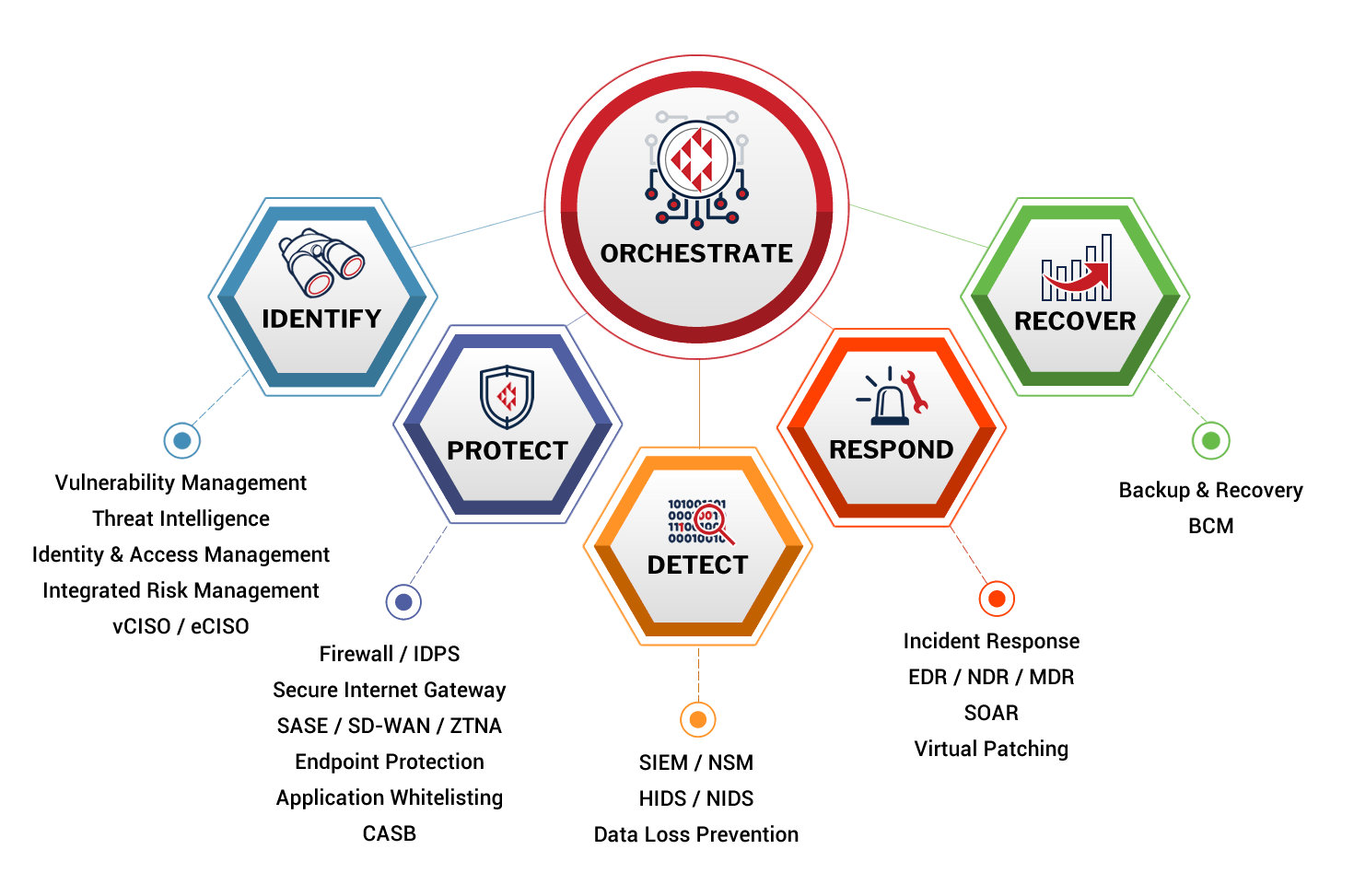
Protect, Detect, Investigate and Respond to cyberattacks in real-time with best-in-breed technology.
Why Crystal Eye XDR?
Multi-Award Winning and Recognised







Crystal Eye XDR is Australian Made

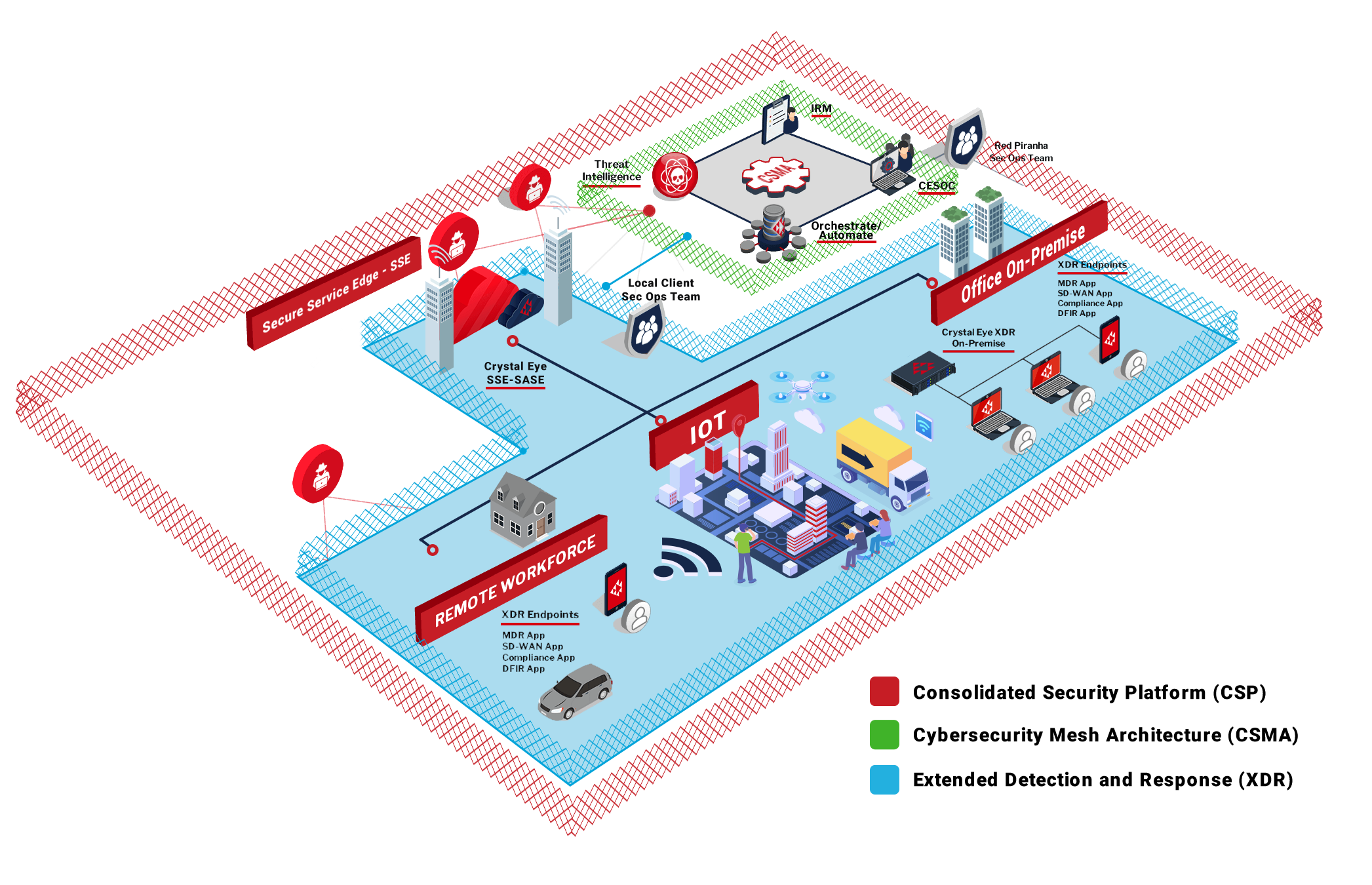
DEPLOYMENT OPTIONS:
Crystal Eye XDR offers flexibility with deployment:
More than just XDR
- Unlike most security products which are often siloed and require manual intervention without providing end-to-end protection, Crystal Eye Consolidated Security Platform (CSP) converges multiple security functions and integrated services into a unified platform to protect your organisation from the network, cloud to endpoints with tangible ROI.
- Our network-based and cloud-based sensors (Crystal Eye XDR) deliver Network Detection & Response (NDR) in combination with our host-based sensors (Crystal Eye EDR) to deliver Endpoint Detection and Response (EDR), which all works together to deliver eXtended Detection and Response (XDR).
- Our consolidated security platform offers full detection and integrated threat intelligence capabilities offering plug-and-play holistic security without the engineering overhead.
- Crystal Eye Orchestrate is our centralised management console which takes care of the service delivery and acts as a data lake to collect all the data for correlation and response coordination. Our flexible deployment option makes things significantly simpler and as all Crystal Eye products use standard data format and shared data storage - this avoids the labourious task of normalising and correlating data from different technologies.
Managed SIEM
- XDR avoids the complex integration required with Security Information & Event Management (SIEM) and breaks down the silos between different systems by having a single data store for all events.
- Where SIEM focuses on pulling the data together into events, XDR has the added benefit of pro-active and automated rapid response to stop threats in their tracks before real damage occurs. XDR goes a step further to provide advanced threat detection with research analysis labs to support defensive efforts.
Integrated SOAR
- Our XDR solution has integrated Security Orchestration, Automation & Response (SOAR) processes, like response playbooks and integrated human-machine teaming, allowing you to automate responses to low-risk threats and coordinate responses to high-risk threats with the relevant resources.
- These capabilities are typically not utilised by most organisations due to resourcing issues, but our integrated SOAR approach provides automated incident response.
- Our automated incident response process gets executed immediately when a breach occurs. Our integrated CTI and security operations team working in the backend instantly start working on identifying the potential incident breach and gathering crucial intelligence leading to efficiency - saving time, money and reducing risk.
Crystal Eye XDR Features
- Crystal Eye CSP delivers a comprehensive solution across a range of security areas, with the whole platform working together to protect, detect and respond to threats in your environment.
- This all works together to provide a single defence-in-depth platform to mitigate risks to your organisation.
- Our modular approach can be catered to meet the needs of each company, so you can pick and choose what matters most to you without implementing the whole solution.
- It's about business outcomes and managing risks specific to your needs, not just about technology for the sake of it.
- Delivers effective cybersecurity outcomes for your clients without the overhead of developing, staffing, auditing and maintaining your security teams. Red Piranha offers fully compliant security outcomes on your behalf to your client without the risk.
- Out-of-the-box ability to detect threats, offering a consistent level of security without the complexity of integrating products from multiple vendors.
- Automatically collects and correlates information across the entire IT architecture to identify real threats anywhere in your client’s IT environment and automatically triggers the coordinated response.
- Lowers the cost of integration and allows for the deployment of critical security controls such as monitoring and incident response seamlessly.
- MSP-specific integrations and multi-tenant console, a scalable solution.
- 24/7/365 rapid Response for peace of mind.
- Crystal Eye CSP addresses security holistically, offering more visibility and context into potential cyber threats before they become an event.
- Groups related threats across the MITRE ATT&CK framework and address them according to your risk appetite.
- Offers automated detection and response capabilities, allowing your security teams to streamline the processing of the large volume of security data.
- Direct on-demand human-machine teaming allows you to escalate and call on our team of experts for push-button security outcomes.
- Cost-effective data storage and analytics to process large volumes of data.
- On-demand threat hunting to proactively detect security breaches.
- Integrated PCAP analysis to reduce attacker dwell time.
- On-demand Digital Forensics for effective rapid response.