
SIEM as a Central Logging System
Security Information Events Management (SIEM) refers to a central logging, viewing, monitoring and management system for security-related events and log data from across an enterprise.
Powerful due to its ability to correlate data from multiple sources, SIEM enables security analysts to identify and analyse suspicious behaviour and identify patterns much quicker than looking at data from individual systems.
Logged data represents all activity that occurs across a network, by collecting data from infrastructure such as “UTM”, “Endpoint”, and “cloud services” (Hybrid Infrastructure).
Collected logs are then analysed by a correlation engine which will trigger the appropriate alarms based on preconfigured rules and directives. Alerts include security detection, operations and regulatory compliance events.
SIEM requires continuous system maintenance to ensure it remains stable and functions efficiently.
To stay effective and relevant to new threats, systems need continual updates to rules and directives to ensure the system is up to date against the latest threats.
What is Next Generation SIEM?
A modern SIEM or next-generation SIEM should be capable of logging data and generating information. IT teams can then use this data as threat intelligence to detect and block malicious activity on their network and systems before any damage may occur.
Next-generation SIEM has all the capabilities of the traditional SIEM like automated log management, pattern recognition and alerting, as well as additional features like emerging and agile technologies such as cloud-based analytics and SOAR.
Modern SIEM also includes user and entity behaviour analytics (UEBA). UEBA is cybersecurity process that takes note of user activity and behaviour patterns to detect any anomalies or deviations from “normal” patterns.
Furthermore, modern SIEM is super-charged with “machine learning” (Playbooks) that provide extra capabilities for the security team to respond to any potential incidents in a better triage of alarms. The Playbooks or advanced analytic capabilities are crucial to identifying hidden threats and reducing “dwell time”. They include both sophisticated scenario detection and behavioural modelling to identify and prioritise risks.
The Next-Generation SIEM services sit at the core of our security solutions at Red Piranha. Red Piranha is the only vendor offering Managed SIEM services as standard with Crystal Eye UTM solutions. We believe the only way to ensure an effective cybersecurity system is by taking a proactive approach. Red Piranha's managed SIEM is proactive in monitoring and reporting using advanced detection to identify any anomalies or threats on enterprise networks.
Red Piranha’s team of security analysts will detect and identify any suspicious activity. Combined with our anomaly-based detection systems, Red Piranha’s team works tirelessly to detect threats 24/7 minimising dwell time and potential risks on the entire infrastructure.
Red Piranha Managed SIEM Solution Includes the following features
- Data aggregation: Red Piranha SIEM agents and API aggregates data network devices, servers, databases and other security systems such as firewalls, anti-virus and Intrusion Detection Systems (IDS) and many other compatible systems.
- Red Piranha SIEM gathers more than 20,000 events per second. All data is encrypted on the Crystal Eye UTM and pushed out to our SIEM Data Lake for processing and analysis.
- World leading Threat intelligence feeds: Combines internal data with threat intelligence feeds from our member sources like the OISF containing the most up to date data on vulnerabilities, threats and attacks globally.
- Correlation: By linking the events and related data into meaningful bundles, Next Generation SIEM will present the security incident threats and how they are relevant to the discovered Indication of Compromise.
- Analytics: Using statistical data and machine learning to uncover anomaly trends which may post as security threats and alerts.
- Alerting: Analysing logs and incidents to send out to notify our internal security experts and customer security team for action and response.
- Dashboard: Provides an easy to read interface to assist with event data trend analysis and abnormal activity detection allowing clients to access incident and event reports. This also allows clients to schedule vulnerability scans, manage incident response and forensics.
- Security Hardening and GRC: By integrating Governance, Risk and Compliance GRC and Red Piranha SIEM Frameworks, we provide clients with full security hardening features. These can be used to enforce security policies for compliance and greater security controls across endpoints.
- Digital Forensics: Red Piranha Crystal Eye also offers complete digital forensics capabilities.
These forensics services can be ordered and scheduled via the client dashboard. The ability to run forensic investigations remotely means quicker turn around times for security incident response as well as SIEM data that provides in-depth visibility during any incident investigations.
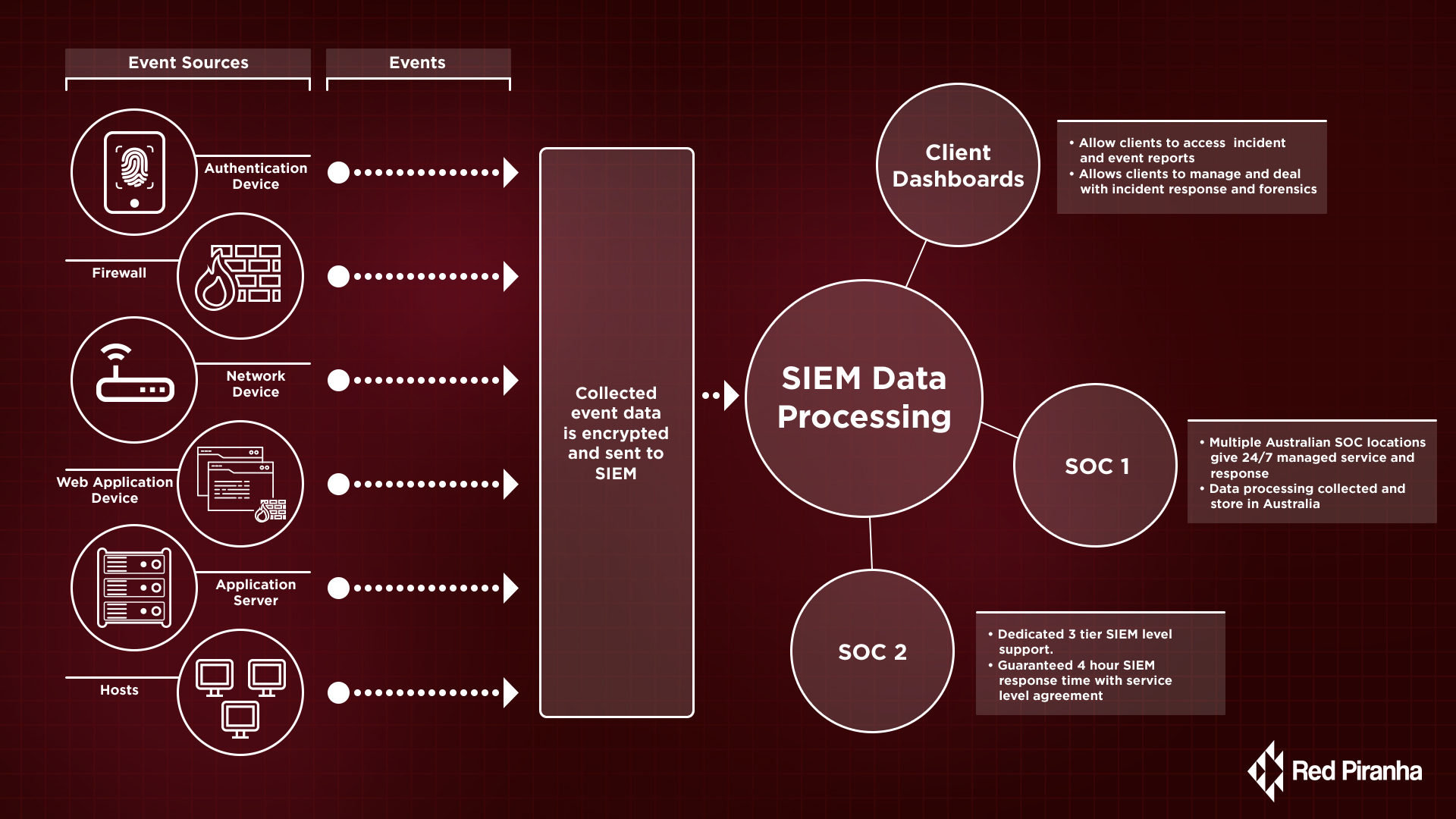
Thus, providing a complete end-to-end SIEM solution that increases the visibility, awareness and effectiveness of your security systems without the complexities of self-managing the millions of alarms and alerts.
