VULNERABILITY ASSESSMENT AND
PENETRATION TESTING (VAPT)
Vulnerability Assessment and Penetration Testing Services
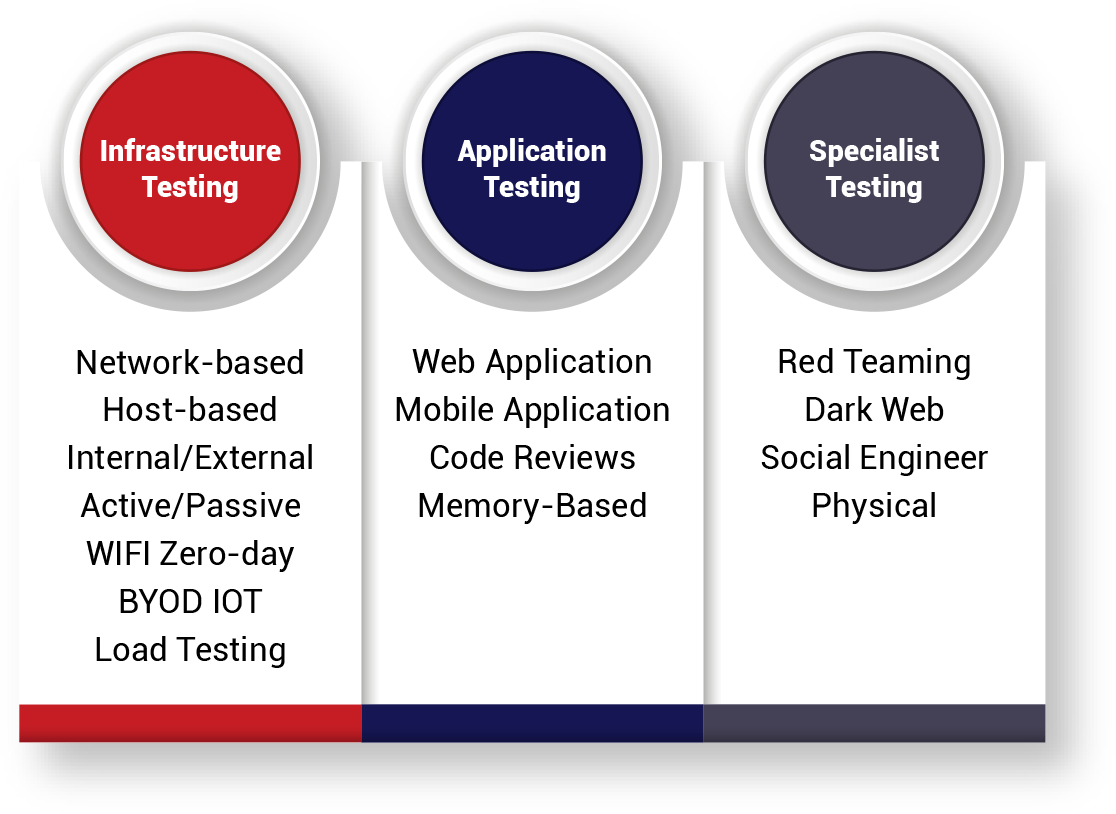
Our team of certified and accredited security professionals delivers a full range of security testing services which you can choose and customise to meet your specific testing needs.
Red Piranha offers a full service capability across Vulnerability Assessments and Penetration Testing (VAPT). Fix vulnerabilities in your network and achieve compliance goals with Red Piranha’s security testing services. Our Crystal Eye platform also automates the technical aspects of a Vulnerability Assessment to ensure you get compliant and stay compliant with regular scans.
FIND YOUR WEAKNESSES BEFORE THE BAD GUYS DO.
- It’s time to properly test your IT environment with Red Piranha’s comprehensive Vulnerability Assessment and
Penetration Testing Services.
DON’T LEAVE YOURSELF EXPOSED
Too many organisations struggle to meet their compliance requirements;
- It’s time to get serious about security testing.
GET AUTOMATED
Security testing is typically manual and reactive;
- It’s time to automate the process.

Vulnerability Assessment

Breach & Attack Simulation

Penetration Testing

Automated Vulnerability Assessment
Red Piranha is one of the few security organisations with ISO/IEC 27001 and CREST Certifications to demonstrate that our processes, tools, and systems adhere to a recognised framework.
We only hire the most experienced security experts with intimate knowledge of the latest vulnerabilities and attack methods to make sure you get the most out of the security testing. Our team of certified and accredited security professionals deliver a full range of security testing services customisable to meet specific testing needs.
To learn what makes Red Piranha’s Vulnerability Assessment and Penetration Testing Services stand among the best in the industry, click here.


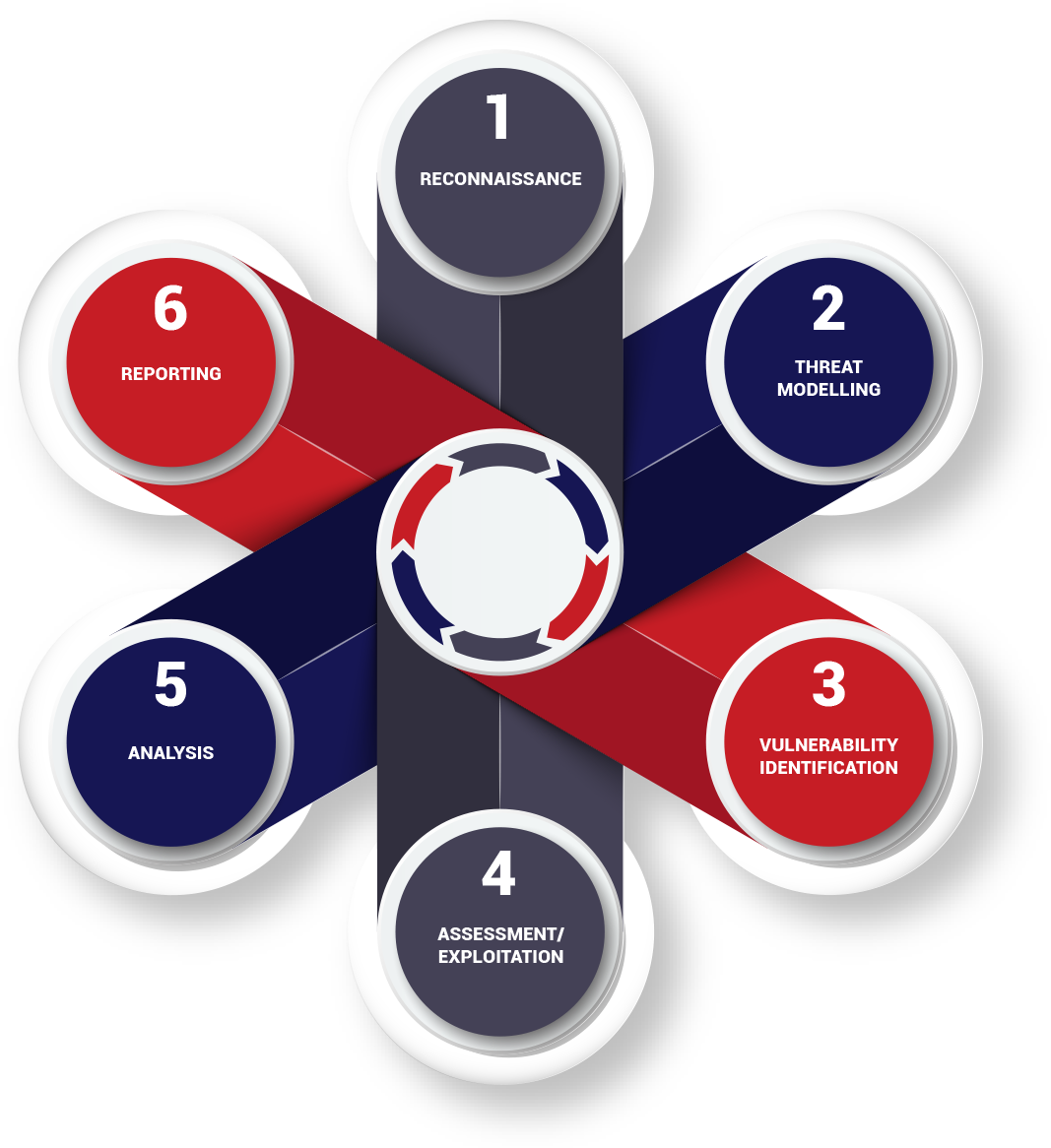
Vulnerability Assessment and Penetration Testing Process
![]() Vulnerability Assessment
Vulnerability Assessment
A Vulnerability Assessment is a hands-on technical engagement that provides a view of the known vulnerabilities that exist in your network. We identify, quantify, and prioritise vulnerabilities in your IT environment, then help you put a plan in place to mitigate and manage those risks.
![]() Penetration Testing
Penetration Testing
Penetration Testing takes the next step, testing both known and unknown weaknesses in your environment. Instead of only identifying potential vulnerabilities, the aim is to push things further to uncover whether those vulnerabilities can lead to an actual breach. These results allow us to provide a set of detailed recommendations on how to fix the issues and avoid a security incident.
![]() Breach & Attack Simulation
Breach & Attack Simulation
For a deeper understanding of how secure your network is, we can conduct a series of simulated attacks on your systems in a more orchestrated manner, in what is known as ‘breach and attack simulation’. This approach takes the testing to a new level by mimicking an actual multi-pronged attack scenario to gain a clearer understanding of your true security posture in a real-world situation.
Know more how Breach and Attack Simulation brings a needed dimension to Penetration testing through Red Teaming and Purple Teaming Exercises.
![]() Automated Vulnerability Assessment
Automated Vulnerability Assessment
Crystal Eye platform has direct access to the infrastructure within the network so that you can run automated Vulnerability Assessment scans monthly or even weekly to ensure you stay on top of the new vulnerabilities in your environment. Manual security assessments are typically performed once or twice a year; which is a good start; however, new vulnerabilities open up, and new threats are appearing almost daily, leaving you exposed between checks.
![]() Phishing Assessment Service
Phishing Assessment Service
Our experts have developed a range of carefully tailored phishing campaigns that simulate real-case scenarios to effectively target an organisation's employees, contractors, or management personnel.
Red Piranha’s Phishing Assessment Service is led by people and processes to assess your organisation’s end-to-end security posture, including the efficacy of countermeasures against the most likely impacts of phishing, such as fraudulent money transfers, ransomware infections and lateral movements, command-and-control communications, and data exfiltration. An end-to-end framework to enhance security outcomes.
Compliance
Businesses are under increasing pressure to meet a range of compliance requirements, including ISO/IEC 27001, which requires regular security assessments. Cybersecurity is an accepted part of today’s business climate, and consistent security testing is critical.
We identify a range of potential vulnerabilities in target systems, then exploit the vulnerabilities identified and penetrate the target system in a controlled manner.
Red Piranha uses robust network protection mechanisms on the attack infrastructure to prevent network compromise.