SECURITY COMPLIANCE
Governance, Risk & Compliance (GRC)
Red Piranha’s Governance, Risk & Compliance GRC services provide you with expert knowledge across relevant standards and frameworks, supported by our range of products to ensure you achieve compliance and raise your assurance levels.
Increasing Pressure
Organisations are under increasing pressure to meet a range of information security compliance requirements such as ISO/IEC 27001, ISM, NIST, Essential Eight, GDPR, PCI and HIPAA to continue doing business in today’s climate. Chief Information Security Officers (CISOs) who typically look after these compliance requirements are becoming highly sought after, and with that demand comes increasing cost – making them unattainable for many businesses.
How are you going to find someone with all the skills and knowledge, without the liability and expense of additional head count?
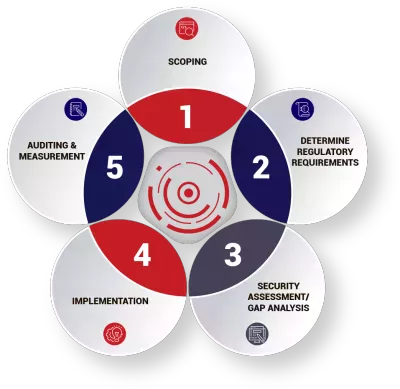
The Compliance Journey
Achieving compliance against various standards is a long and demanding process. There is no quick fix - it takes time and requires ongoing support from senior management. It’s important you find a trusted partner to help you along this journey because you’ll need the right people around you to get to the destination. We’re here to help.
Governance, Risk & Compliance (GRC) - The Red Piranha Advantage
Red Piranha’s global team of highly qualified and certified security and compliance experts deliver our extensive range of security services. Coupled with our ISO/IEC 27001 certified security operations for the Crystal Eye Platform, you can obtain a solid foundation to meet your compliance requirements and automatically protect, detect, and respond to evolving threats.
Crystal Eye’s machine learning capabilities provide automation of routine tasks such as traffic monitoring and network analysis which allows time to focus on priority tasks that require human intervention such as meeting compliance requirements. Red Piranha is one of only a few security organisations with a fully ISO/IEC 27001 certified process to ensure delivery of the highest quality of service, giving you the confidence and peace of mind, you’re partnering with the right team.
We have one of the fastest growing security teams in Australia and Asia-Pacific to ensure we continue developing our world-class technology platform and continue delivering our best-in-class security consulting services. In addition to our global presence, the majority of our security team reside in Australia to be able to provide hands-on capabilities to our Australian customers as well as customers in other regions.
Security Maturity Model - Governance, Risk & Compliance (GRC)
Maturity Modelling is a pragmatic method of evaluating the current state of your cybersecurity posture as measured across the various security aspects that your business needs to address. Governance, Risk & Compliance allows you to clearly communicate your status to various stakeholders and prioritise high risk areas as well as mapping out the next steps in your organisation’s security journey.
| Security Aspect | Initial | Developing | Defined | Managed | Optimised |
|---|---|---|---|---|---|
| Patch Management and Antivirus | Inconsistent Automatic updates, No Reporting | Some automation and reporting | Documented & consistently applied | Measured and Reported. Enforced by endpoint mgmt tools | Continuous improvement and innovation |
| Firewall & Network Segmentation | Simple perimeter firewall, ad-hoc desktop firewalls | Dedicated firewall appliance and/or DMZ | Multiple firewalls and network segmentation | Centralised firewall configuration management | Continuous improvement and innovation |
| Identity & Access Management | Ad-hoc with no process | Domain users & computers, some access restrictions/structure | Documented change control processes and JML processes | Analysis, visualisation and reporting tools | Continuous improvement and innovation |
| Asset and Configuration Management | None | Register of assets and deployment documentation | Asset discovery and reporting | Configuration change mgmt & license mgmt tools | Continuous improvement and innovation |
| Information Classification and Protection | None | Ad-hoc file/disk encryption, inconsistent visual | Structured & unstructured data classification, defined meta-data / templates | Discovery, Data Loss Prevention / Rights Management | Continuous improvement and innovation |
| Monitor, Alert and Incident Response | None | Some logging, inconsistent monitoring | Basic SIEM deployed, embryonic continuity plans | SIEM tools integrated with most areas. Regular reviews, response and recovery tests | Continuous improvement and innovation |
| Risk Management and Governance | None | Ad hoc risk assessments, developing security policies | Regular risk assessments and migitation planning, ad hoc awareness training | Regular policy reviews. Training and compliance tracking | Continuous improvement and innovation |
Benefits of Governance, Risk & Compliance (GRC)
On the other side of the equation, try to calculate how much business you could pursue (and win) if you achieve certification with various standards. This benefit will have a significant impact on what type of projects your sales team can go after. For many organisations, while the upfront cost of compliance can be high, it is well worth the opportunities it opens for your sales teams.
Standards & Frameworks for achieving Governance, Risk & Compliance (GRC)
The Governance, Risk & Compliance can be a bit of minefield and it’s hard to know which standards and frameworks apply to your organisation. It’s important to map out a compliance journey that’s relevant to your business. As with any significant commercial undertaking, thinking long-term is key to ensure you futureproof your compliance strategy and make the most of your investment.
ISO/IEC 27001 is often a good framework for many organisations to start with to lay the foundations for a long-term compliance journey and other standards and frameworks can then apply to specific industries from there.
Achieving compliance opens new business opportunities for your company such as launching into new regions and expanding into new verticals. Organisations that plan to operate in Europe almost certainly need to be GDPR compliant to enable this business growth. Similarly, organisations planning to launch a new product in the fast-growing fintech and healthtech spaces will most likely need to be PCI or HIPAA compliant. Importantly, even those companies who may not currently have mandated certification requirements should be starting their compliance journey by applying proper security practices to not only reduce their risk, but also ensure they are prepared for their future compliance needs. It’s a very costly and resource-hungry problem to have to rush a compliance process if the foundations aren’t already in place.
Not implementing a suitable security framework can have devastating effects for any business, even where mandatory regulations don’t apply.
LandMark White was a publicly-listed property valuation company which experienced two major data breaches in 2019 due to a lack of security process. This led to the company being temporary suspended from the ASX and forcing them to change their name to Acumentis to minimise reputational damage. The direct costs relating to the breach were estimated at over $7M plus all the indirect costs associated with the fallout.
Given the significant impact to the bottom line, shareholders are holding Directors accountable if proper security controls aren’t being put in place that could avoid a data breach or security incident. This has led to a trend where shareholder class actions are one of the fastest growing sectors within the legal profession to handle such cases.
Although industries such as critical infrastructure, fintech, manufacturing, technology and managed services are high on the radar for compliance obligations, it is becoming increasingly important for all business to follow a robust information security framework.
Standard | Region | Industry | Type |
|---|---|---|---|
| ISO/IEC 27001 | Global | General | Standard |
| ISM | Australia | Government | Standard |
| Essential Eight | Australia | General | Guidelines |
| GDPR | Europe | General | Regulation |
| NIST | USA | Critical Infrastructure | Framework |
| HIPAA | USA | Healthcare | Regulation |
| PCI | Global | Payment processing | Standard |
| COBIT | Global | General | Framework |
| IRAP | Australia | General | Standard |

ISO/IEC
ISO/IEC 27001:2022 is an international standard published by the International Organisation for Standardisation (ISO) and the International Electrotechnical Commission (IEC) to define information security management systems. It is part of the ISO/IEC 27000 family of standards and is often considered the bible of information security standards. ISO certification is becoming more of a requirement to do business with companies who choose to set standards for their partners and suppliers. Certification against ISO/IEC 27001 is a demanding process and requires an authorised external auditor. The standard includes the following key steps:
- Organisational context and stakeholders
- Information security leadership and high-level support for policy
- Planning an information security management system; risk assessment; risk treatment
- Supporting an information security management system
- Making an information security management system operational
- Reviewing the system’s performance
- Corrective action
Red Piranha is one of the few IT security organisations to achieve ISO/IEC 27001 certification and our exposure to the process enables us to take you through the process with an intimate understanding of what’s required. Would you trust your ISO certification with someone who isn’t ISO certified themselves?
 ISM
ISM
The Australian Government Information Security Manual (ISM) is published by The Australian Cyber Security Centre, which is part of the Australian Signals Directorate. This standard outlines a cyber security framework for Australian Government departments and can also be applied to private enterprises looking for a risk management framework. It includes a comprehensive set of 22 guidelines covering topics such as security incidents, physical security, personnel security, enterprise mobility and system hardening to name a few.
 Essential Eight
Essential Eight
The Essential Eight is a prioritised list of 8 strategies put together by the Australian Cyber Security Centre to mitigate cyber security incidents to assist organisations in protecting their systems against a range of cyber threats. The strategies can be tailored based on an organisation’s risk profile and the types of threats of greatest concern.
- Application control
- Patch applications
- Configure Microsoft Office macro settings
- User application hardening
- Restrict administrative privileges
- Patch operating systems
- Multi-factor authentication
- Daily backups
IRAP
The Information Security Registered Assessors Program (IRAP) is an Australian Signals Directorate (ASD) initiative to provide high-quality information and communications technology (ICT) security assessment services to government. ASD endorses suitably-qualified ICT professionals to provide relevant security services which aim to secure broader industry and Australian Government information (and associated) systems. IRAP Assessors assist in securing your ICT networks by assessing your security compliance and highlighting the information security risks facing your organisation.
Red Piranha is an IRAP-aligned organisation and we’re undertaking the process for our products to go through the certification process. We also have a strategic partnership with the Australian CyberSecurity Centre based on our share ideals and we share threat intelligence data.
NIST
The NIST Cybersecurity Framework provides information security guidance for private sector organisations in the US to prevent, detect, and respond to cyberattacks. It was developed by the National Institute of Standards and Technology, which is an agency of the United States Department of Commerce. It includes a Framework Core, Framework Implementation Tiers and a Framework Profile. The Framework Core defines 5 key functions of information security:
- Identify
- Protect
- Detect
- Respond
- Recover
GDPR
General Data Protection Regulation (EU) 2016/679 (GDPR) is a mandatory regulation enforced under EU law for data protection and privacy in the European Union (EU) and the European Economic Area (EEA). It also covers the transfer of personal data in and out of the EU and EEA areas which can impact companies outside of Europe who have customers or partners inside Europe. GDPR was put in place to give indivduals (defined as data subjects) control of their personal data and has led to sweeping changes for orgnaisations (data controllers and data processors) across the industry. It covers the following topics:
- Transparency and modalities
- Information and access
- Rectification and erasure
- Right to object and automated decisions
- Pseudonymisation
- Records of processing activities
- Security of personal data
- Data protection officer
HIPAA
The Health Insurance Portability and Accountability Act (HIPAA) was enacted in 1996 to regulate the flow of healthcare information in the US and define how Personally Identifiable Information (PII) maintained by the healthcare and healthcare insurance industries should be protected from fraud and theft. Although it mostly applies to organisations in the US, it can also apply companies dealing with healthcare data with customers and partners in the US. The Act is broken into 5 Titles:
- Privacy Rule
- Transactions and Code Sets Rule
- Security Rule
- Unique Identifiers Rule (National Provider Identifier)
- Enforcement Rule
PCI 
The Payment Card Industry Data Security Standard (PCI DSS) is an information security standard for organisations that handle branded credit cards from the major card schemes.
The PCI Standard is mandated by the card brands but administered by the Payment Card Industry Security Standards Council. The standard was created to increase controls around cardholder data to reduce credit card fraud.
Validation of compliance is performed annually or quarterly, by a method suited to the volume of transactions being handled. PCI typically doesn’t apply to companies accepting credit card payments through a 3rd party payment gateway, but would usually apply if you are handling the credit card details yourself.
COBIT 
Control Objectives for Information and Related Technologies (COBIT) is a framework created by Information Systems Audit and Control Association (ISACA) in the US for IT management and IT governance. It defines a set of generic processes for the management of IT and is broken into 5 key components as follows:
- Framework
- Process descriptions
- Control objectives
- Management guidelines
- Maturity models
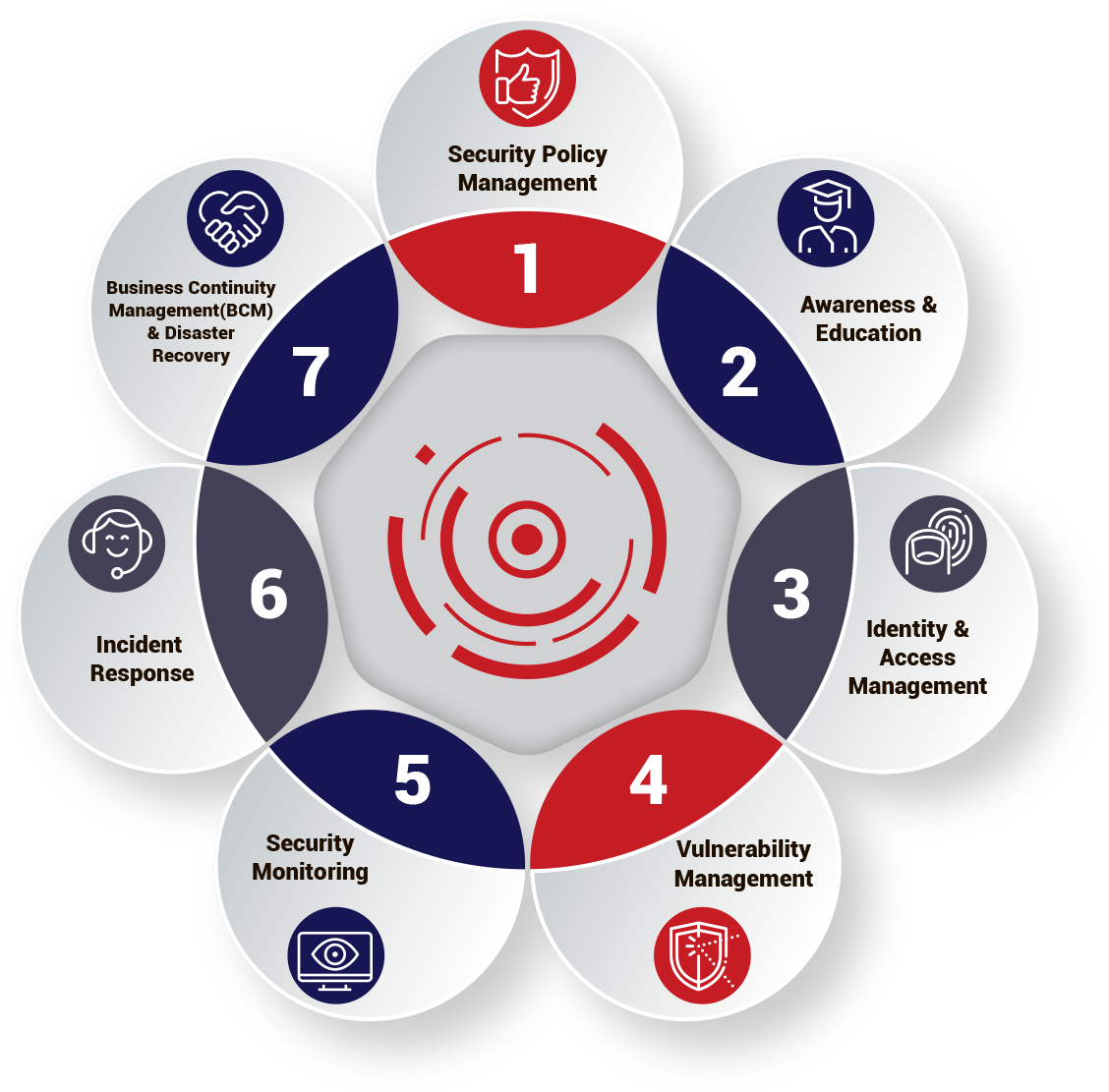
Governance, Risk & Compliance (GRC) - Key Areas of Compliance
Technologies
Compliance isn’t about creating policies that sit on a shelf to collect dust. A major part of the process is implementing hard and fast security controls and implementing relevant security procedures to prevent incidents occurring. Compliance drives a process of continuous improvement and measurement to ensure your organisation is getting more secure over time.
Compliance Mapping
It’s important to understand how various security services map against the requirements of various standards. Our eCISO™ service delivers the following compliance outputs, as they relate to the corresponding standards shown below. Our tailored security services can also deliver compliance requirements you may have beyond this.
| Process and/or Security Service | ISO/ICE 27001 | NIST CSF | COBIT 5 |
|---|---|---|---|
| Security Policy Management | A.5.1.1 | ID.GV-1 | APO02* |
| Awareness and Education | A.7.2.2 | PR.AT | APO07 |
| Identity and Access Management | A9.1.1 | PR.AC | DSS05, DSS06* |
| Vulnerability Management | A.12.6.1 | PR.IP-12 | BAI10, DSS03 |
| Security Monitoring | A.12.4.1 | DE.CM | DSS01.03, DSS05.07 |
| Incident Response | A.16 | RS | DSS02 |
| BCM and DR (Note 3) | A.17 | PR.IP-9*, PR.IP-10* | DSS04* |
| Normal font indicates an explicit reference to the process. Red font with an asterisk indicates a tangential reference. See discussion below | |||
Compliance mapping to our products and services
Compliance isn’t about creating policies that sit on a shelf to collect dust. A major part of the process is implementing hard and fast security controls and implementing relevant security procedures to prevent incidents occurring. The compliance process drives a process of continuous improvement and measurement to ensure your organisation is getting more secure over time.
| Compliance Area | Products | Services |
|---|---|---|
| Security Policy Management | CE XDR, CE Endpoints | Security Compliance, Security Assessment, eCISO, vCISO |
| Awareness & Education | Security Training, Security Assessment, eCISO, vCISO | |
| Identity & Access Management | CE XDR | Security Assessment, eCISO |
| Vulnerability Management | CE XDR, CE IRM, CE Endpoints | Security Testing, Security Assessment |
| Security Monitoring | CE XDR, CE SOC, CE Endpoints, CE Orchestrate | Security Management, Security Assessment |
| Incident Response | CE XDR, CE SOC, CE Endpoints, DFIR App | Security Investigation, Security Assessment |
| BCM / DR | CE XDR, CESOC, CE Orchestrate | Security Investigation, Security Assessment |
RED PIRANHA SERVICES
We can help you achieve compliance through our extensive range of services:
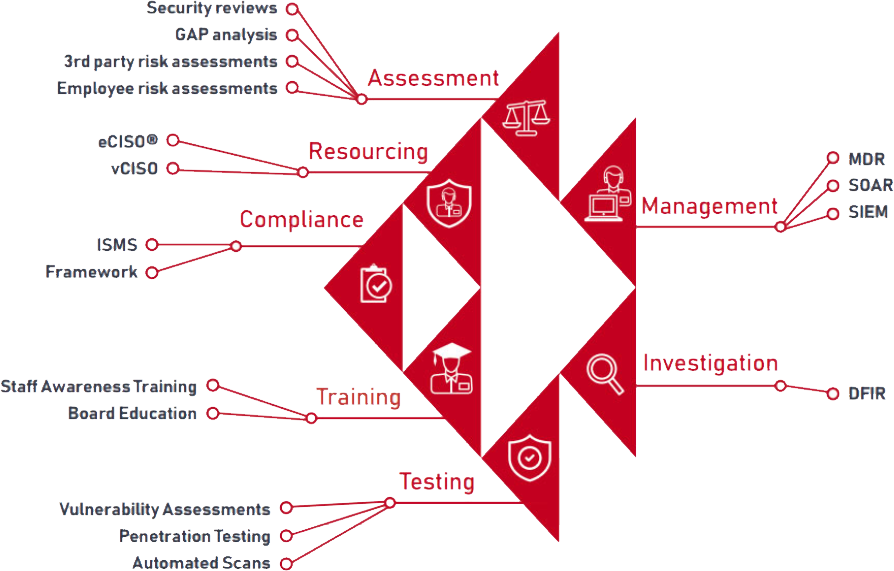
 Security Compliance - Governance, Risk & Compliance
Security Compliance - Governance, Risk & Compliance
You need to start your compliance journey with an overarching framework from which to build a solid foundation to establish your security posture. We can help you get started on the right foot along this journey with our Governance, Risk & Compliance services.
 Security Resourcing
Security Resourcing
Red Piranha’s cost-effective CISO services give you the benefits of having access to a pool of industry-leading security specialists to help you achieve compliance, without the expensive overhead of a full-time CISO. Our eCISO™ service provides automated compliance features to get the job done as efficiently as possible.
 Cyber Security Awareness Training
Cyber Security Awareness Training
Staff awareness of security issues and threats is one of the greatest risks to an organisation. We offer standard and tailored online cybersecurity awareness training programs to help your staff and your Board understand risks as well as your policies and procedures to better protect your organisation.
 Security Assessments
Security Assessments
Security risk assessments and audits help you understand your organisation’s security maturity model, identify potential gaps in your security controls and recommend changes to meet your compliance requirements.
 Security Testing
Security Testing
Security testing is a hands-on technical engagement which gives you a view of the known and unknown vulnerabilities that exist in your IT environment, as well as providing a plan to mitigate and manage those risks. Red Piranha offers a full service capability across Vulnerability Assessments and Penetration Testing (VAPT).
 Security Management
Security Management
Our Managed Detection and Response service applies machine learning to automatically detect and block security threats using the Crystal Eye Platform. We also offer managed SOAR and managed SIEM capabilities to provide an even greater level of assurance.
 Security Investigation
Security Investigation
Digital Forensic services can help you get to the bottom of what happened in relation to a security breach in your network, coupled with a comprehensive Incident Response plan to help you recover from the breach and get back to business as quickly as possible with minimal impact.
** Cost of a Data Breach Report, Ponemon Institute, 2023