
The online threat landscape is ever-changing.
Recently, a functional Microsoft Remote Desktop exploit was publicly released that allows an attacker to gain System access; furthermore, all versions of the popular email delivery software EXIM is reported to be remotely exploitable, enabling an attacker with superuser access to 57% of the worlds email delivery systems.
The integrity of your business operations relies on your security. Business owners and Board members have a legal responsibility to protect your business and ensure that customer information is secured.
IT professionals typically operate in a reactive manner rather than proactive; this often means more of a focus on assisting with Monday morning printer problems than ensuring security patches are up to date.
Due to the sheer number of existing and emerging threats, time and budget constraints, human error or neglect, systems remain exposed, not switched on or forgotten about until staff learn of the breach.
Early Detection
The best strategy to avoid an incident is early detection. Most organisations are unaware of a breach with no detection whatsoever, and the average response time for small businesses 800 days.
Therefore, Security Information Event Management (SIEM) and network visibility are essential.
But with millions of threats circulating every day, how do you protect your business, detect the level of risk, and respond 24 hours a day? Put simply; you can’t
So, what can you do? You need security that is both easy to use and affordable, which features proven security techniques and multiple layers of protection to ensure your data is safe 24/7. Ideally a multi-layered next-generation firewall that increases security awareness, reducing risk exposure from advanced cybercrime, malicious software and insider threats.
Adopting a unified security solution, such as Red Piranha’s Crystal Eye, means having a single vendor and a single product platform to achieve a complete defence-in-depth security strategy.
This creates a seamless security surface and leaves no gaps as often found when taking a multi-device/multi-vendor approach. With all compliance documentation built into the system, scheduling reports is simple with the additional option of producing on-demand reporting.
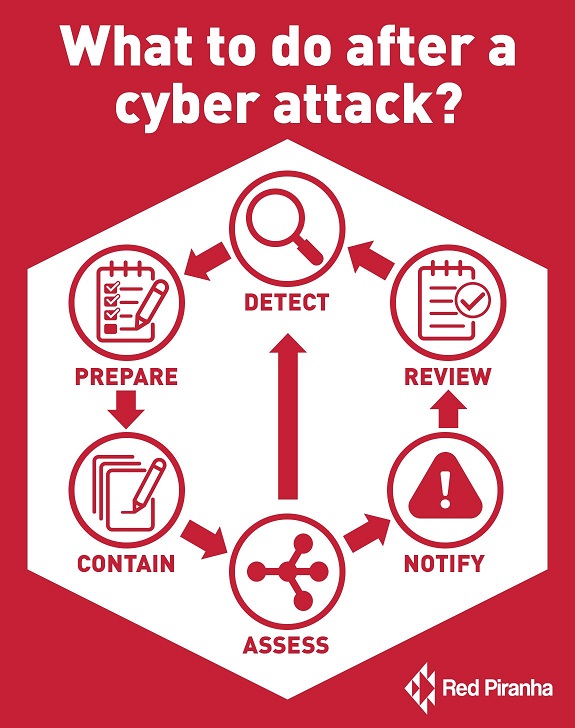
Preparation
An incident response plan is effective in securing and quickly mitigating or reducing the impact of a cyber-attack, enabling your staff to respond swiftly in a way that is systematic while also following best practice, this also significantly reduces the chance of human error due to panic.
A well thought out incident response plan is not only about isolating the breach; it’s also about retaining forensic information related to the breach ensuring your company meets the mandatory reporting criteria.
This gives your business the ability to analyse the events that took place and the response of your staff so the process for potential future events can be improved.
Containing and preserving the Infrastructure
An Information Security Management System (ISMS) plan or template is needed to get you through these situations and is a standard inclusion in our Virtual CISO package.
Our simple yet effective incident response SOAR service allows the organisation to respond to potential incidents immediately.
If your organisation doesn’t currently have an Incident Response Plan in place, the OAIC recommends taking the following steps:
- Identify where the data is hosted
- Identify what users or services have access to the compromised data
- Immediately isolate systems that have been affected
- Perform full backups, retaining the state of the devices that are potentially compromised
- Make sure you are not overwriting older backup drives/tapes (you may need them)
Assess the impact
- Identify the type of personal information involved in the data breach
- Identify the cause and extent of the data breach
- Identify how this could harm affected individuals; can this harm be removed through remedial action?
Notify
Consider the obligations of your business under the NBD scheme.
Businesses may also be required to:
1. Notify the Office of the Australian Information Commissioner
2. Notify Australian Cyber Security Centre
3. Notify all individuals whose personal information is involved in the eligible data breach
4. Publish your notification with the aim of bringing it to the attention of all individuals at likely risk of serious harm.
Review
- Perform a security review including a root cause analysis of the breach
- Mitigation plan to reduce the risk of similar future incidents
- Perform an audit to ensure prevention plan is implemented
- Review of policies and procedures and changes to reflect the lessons learned from the review
- Changes to employee selection and training practices
- Review of service delivery partners that were involved in the breach
Want to be notified when new threats are applicable to you? Sign up here
