Reports suggests that a surveillance malware called Pegasus, attributed to an Israeli cyber intelligence company, was used with an intent to steal data from human rights activists based out of Saudi. As revealed by Amnesty International (a human rights organization), its staff member received a WhatsApp message containing a malicious link that could have triggered the installation of the malicious spyware if clicked upon. Similar patterns to trick activists to install Pegasus spyware was detected in the wild.
Malicious Links Sent to Amnesty International Staff belongs to an Infrastructure Owned by an Israeli Cyber Intelligence Company, NSO Group
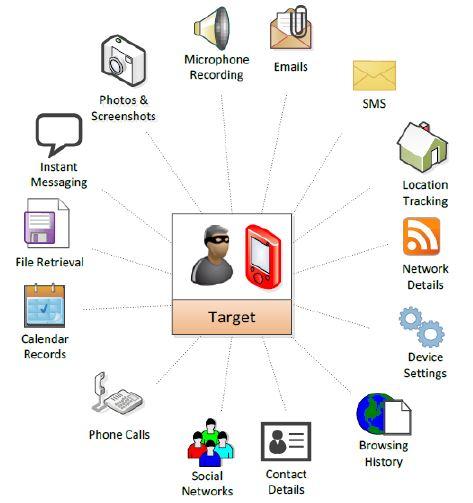
As per the claims of Amnesty International, the message that was sent to its employee contained a link which pointed to a domain name akhbar-arabia[.]com. According to 'The Citizens Lab', a research flank of the University of Toronto, the above-mentioned domain is a part of an elaborated infrastructure that belongs to NSO Group’s Pegasus spyware. The Pegasus spyware has the capabilities to collect intelligence from targeted smart phones and provides unlimited access to the mobile phone logs and data.
The following is the message sent to Amnesty International Staff
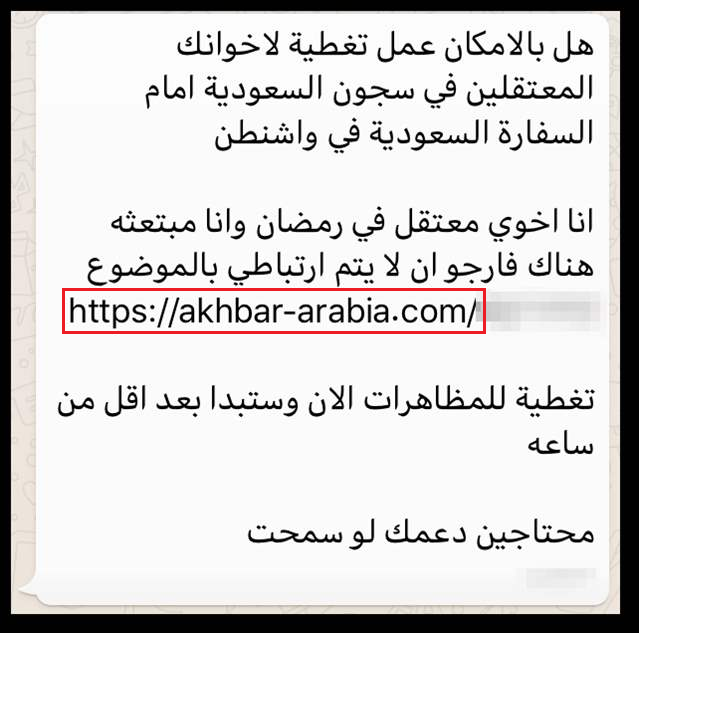 Identical Malicious Link Detected in a Message Received by a Human Rights Activists Based out of Saudi
Identical Malicious Link Detected in a Message Received by a Human Rights Activists Based out of Saudi
A human rights activist based out of Saudi was targeted and the message sent to the indivisuals phone contained a malicious link that pointed to a domain that belonged to NSO group's infrastructure. The findings of Citizen Labs point out to the fact that the domain that the malicious link was pointing to social-life[.]info. The research organization 'The Citizen Lab' also indicated that similar messaging campaign was targeted towards other individuals in the middle east.
The screenshot below shows the message and the malicious link sent to the human rights activist in Saudi.
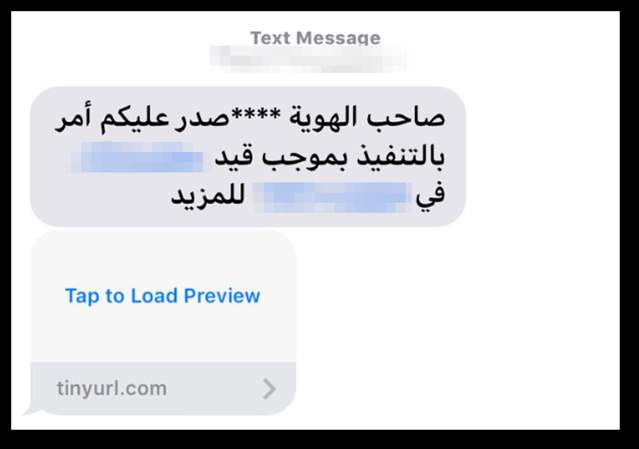
Clicking the Link Would Have Triggered Downloading & Installation of the Pegasus Malware to the Victims Phone
It is clear now that in both the above cases the threat actor wanted the targeted user to click the link. Prior research by The Citizens Lab suggests that both the domains that the links points to were a part of an elaborated infrastructure that belonged to the NSO group. Once the target would have clicked the above mentioned links their phones would have been infected with NSO group's Pegasus spyware.
Technical Overview of the Malicious Campaign Involving NSO's Pegasus Malware
NSO group provides a holistic product that allows remote installation of the Pegasus Malware. A technical document describing the specifications suggests that NSO's infrastructure supports 2 types of remote installation of the Pegasus Malware namely, Over-the-Air (OTA) and Enhanced Social Engineering Message (ESEM).
Don’t leave yourself exposed. Find your vulnerabilities before cybercriminals do. Contact us for Vulnerability Assessment and Penetration Testing.
