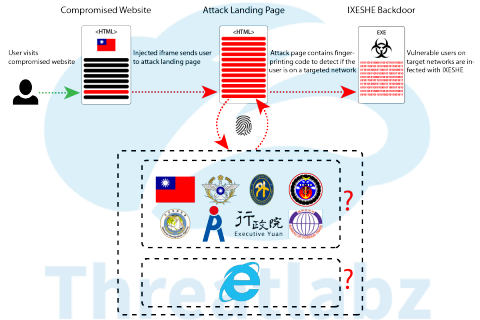
There have been reports that a malware campaign named as CNACOM campaign has been carried out against Taiwanese Government network infrastructure through a compromised public sector website. The compromised website contains an iframe injected to the footer of the page which sends the user to the attack landing page. The attack landing page contains a finger printing code that tracks the location, browser and IP address of the user. If the user is using any of the versions of internet explorer and has an IP address based out of one of the targeted Taiwanese Government networks then the target’s network is infected with IXESHE.
IXESHE pronounced as ‘i-shushi’ is a backdoor malware which has the capability to create a safe passage for attackers to peep into the data storage systems and computers of the targeted network. The attack group which is known to carryout IXESHE campaigns in the past were identified by various names including the IXESHE label, APT12, Numbered Panda, and DynCalc.
Experts say that this group is a prominent hacker group that has been working for the Chinese government for a while now. The APT12 (advanced persistent threat) group was the same group that was accused of illegally accessing the New York Times networks to spy on the activities of the news publishers.
According to what researchers from Zscaler have to say, the recent cyber attacks on the Taiwan government network infrastructure looks quite similar to the exploit that was originally planted and initiated by APT12 back in August 2015. The exploit CVE-2015-5122 featured a landing page that targeted various Taiwanese Government networks. There is no solid proof that the present malware campaign dubbed CNACOM is the brain child of Chinese group APT12.
However, comparing the attacks initiated by the Chinese hackers group in the past there seems to be a strong suspicion that there is some kind of similarity in the present attacks on the Taiwanese Government networks with the one APT12 carried out in 2015.
Don’t leave yourself exposed. Find your vulnerabilities before cybercriminals do. Contact us for Vulnerability Assessment and Penetration Testing.
