
MikroTik routers have yet again made headlines after researchers have revealed that a major hack leveraged against these routers have compromised more than 7500 of them. Apparently, the reports suggest that these MicroTik routers have been configured by malicious threat actors to reveal the network traffic details and leak it to some selective IP address.
This is the second time in nearly two months that attackers have targeted MicroTik routers. In July this year there were reports of attackers to have affected a whooping 200,000 devices with a cryptojacking campaign. On setting up a honeypot system it was found that the CVE-2018-14847 vulnerability is being exploited.
The CVE-2018-14847 vulnerability is said to have affected two components of MicroTik routers namely, ‘’Winbox’’ & ‘’Webfig’’ where, winbox is a windows GUI application and the later is web based.
Compromised MikroTik Routers Leaking Network Traffic
The attacker has supposedly compromised more than 7500 MicroTik routers and has its TaZmen Sniffer Protocol traffic to IPs controlled by the adversaries. On having a closer look at the compromised MicroTik RouterOS it is certain that the IP of the top attacker is 37.1.207.114 and most of the network traffic is directed to it.
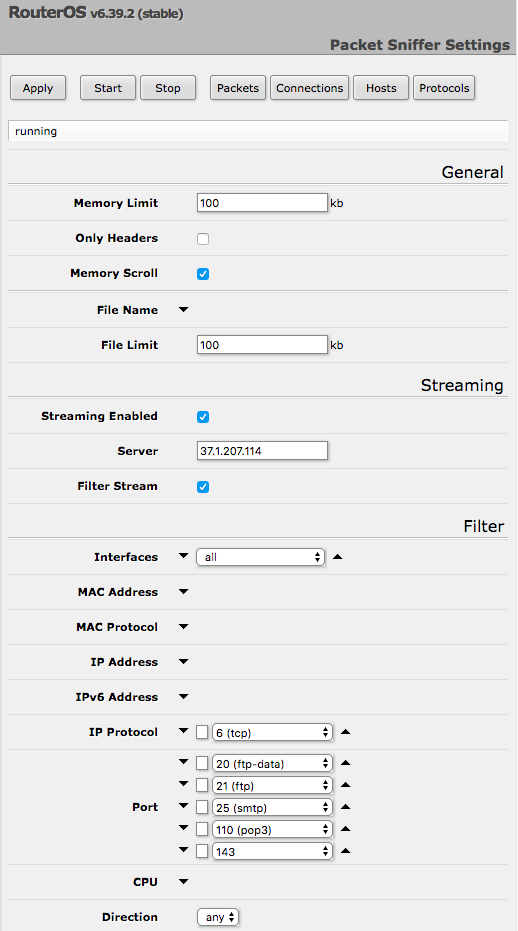
According to the researchers at Netlab 360, “Attackers are mainly interested in port 20, 21, 25, 110, and 143, corresponding to FTP-data, FTP, SMTP, POP3, and IMAP traffic. We also noticed the snmp port 161 and 162 are also top on the list’.
The stats show that Brazil and Russia are said to be the most affected nations. It is also confirmed that the 31% of the MicroTik devices exposed to the internet are vulnerable to such attacks (CVE-2018-14847) constituting approximately 370,000 endpoints.
Red Piranha strongly recommends all users of MicroTik Routers upgrade to MikroTik RouterOS 6.40.8 [bugfix] or 6.42.1 [current] - Click Here to Patch Up!
