A new technique has been leveraged by cyber criminals that tricks user to execute arbitrary codes on to their computer systems and download malware. The uniqueness about this method is that it involves mouseover events and PowerPoint Files.
Attackers have long used the method of delivering malware through specially crafted Microsoft office files. Such attacks have been tracked and studied upon and it has been seen that in most cases the target falls in the trap after enabling VBA macros embedded in the document.
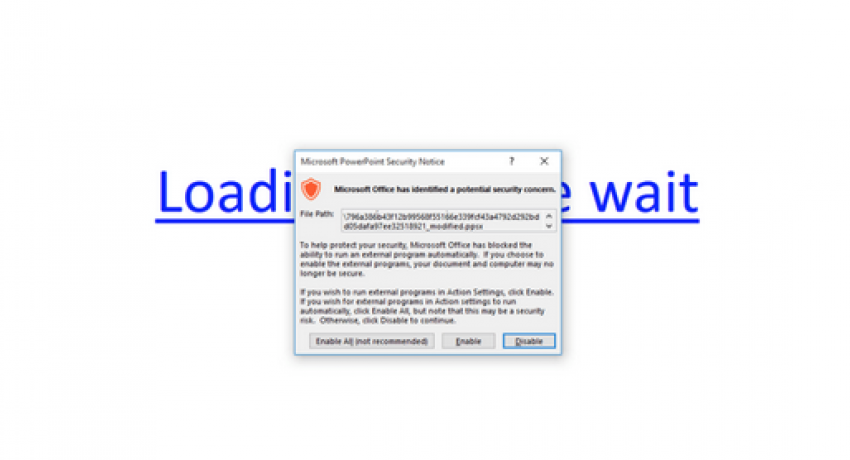
Nevertheless, the method demonstrated by security researcher Ruben Daniel Dodge does not involve VBA, Macros or JavaScript to execute the arbitrary codes. Here the target is tricked to open a malicious PowerPoint file (this is usually done with the help of social engineering). Once the PowerPoint file is opened, a message, “Loading…Please Wait” is displayed as a hyperlink. A PowerShell Code is executed when the targeted user hover’s cursor over the hyperlink (which is usually done to check whether it is actually hyperlink).
After the PowerShell code is successfully executed a domain named “cccn.nl” is contacted which triggers a download from this site. These steps further result to the deployment of malware downloader.
Security researcher, Ruben Daniel Dodge has given a detailed description of how the attack is executed in his blog.
Click here to view the details with screenshots
In real life scenario, if the malicious PowerPoint document is opened MS office will pop-up a warning message giving the user the option to enable or disable the content before the arbitrary codes are executed. However, the codes will only be enabled if the user ignores the pop up message and hits the enable button. Usually such a blunder is done by the user when he/she is in a hurry.
