
What is RansomHub?
RansomHub, a ransomware group that surfaced in late 2020, sets itself apart from other similar entities by offering more favourable terms to its affiliates and implementing stricter operational controls. They have also pledged not to target non-profit organisations. However, there are indications that RansomHub may have connections with ALPHV, a prior ransomware group. As RansomHub is still relatively new, its modus operandi and potential attack vectors are still under investigation. Red Piranha has been tracking the RansomHub ransomware group.
RansomHub maintains a leak site on the dark web where they threaten to publish stolen data if the ransom is not paid. The screenshot of the Leak site maintained by RansomHub ransomware Group is given below:
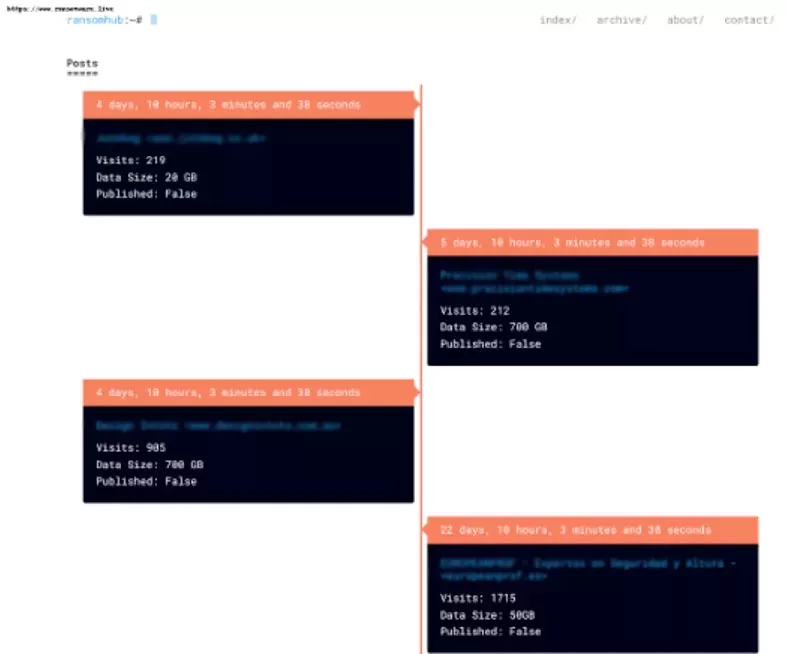
Figure 1: RansomHub Ransomware Leak Site
What are Tactics, Techniques, and Procedures (TTPs) of RansomHub?
RansomHub is a ransomware group that uses a variety of methods to gain access to a victim’s network:
- Phishing Attacks: RansomHub initiates attacks by sending deceptive phishing emails, designed to trick recipients into downloading malicious attachments or clicking harmful links.
- Exploitation of Vulnerabilities: Once inside the network, they exploit both old and newly discovered vulnerabilities like EternalBlue and PetitPotam to gain remote access and escalate privileges.
- Brute-Force Attacks: They target weak passwords on systems such as Remote Desktop Protocol (RDP) and Virtual Private Networks (VPN) through brute-force attacks to expand control within the network.
- Lateral Movement: After gaining access, RansomHub moves laterally through the network, seeking out critical systems to further exploit.
- Data Theft: They steal sensitive information, including financial records, personal data, and intellectual property, which can be used for extortion or sold on illicit markets.
- File Encryption: Once control is established, RansomHub encrypts files on the compromised devices, rendering them inaccessible.
- Ransom Demand: Finally, they demand a ransom payment in exchange for the decryption keys, effectively holding the victim's data hostage.
What are the Additional Exploits by RansomHub?
Brute-Force Attacks
RansomHub often tries to guess weak passwords through brute-force attacks. They target services like Remote Desktop Protocol (RDP) or Virtual Private Network (VPN). They keep testing different password combinations until they find the correct one. They can get into the network by taking advantage of weak security in operating systems or software.
RDP Brute-Force Attacks
RansomHub focuses on RDP to break weak passwords. When they succeed, they can control the computer from afar. This allows them to spread their attack more within the network.
Lateral Movement & Privilege Escalation
After RansomHub gets initial access, they move through the network. They look for ways to get higher-level access to key systems. They use tools to steal login details and take advantage of weak security settings. This helps them move from one machine to another. Their goal is to reach sensitive data and important systems.
Data Exfiltration
RansomHub takes valuable info from systems they have broken into, like money records, personal details. They use this stolen info to push victims to pay up a ransom or make money by selling it in shady online markets.
Encryption
As shown in the below screenshot, after successfully executing on a victim's computer, the RansomHub ransomware group typically leaves behind a .txt file containing information about the group, instructions for contacting them, and details on the tools required to initiate ransom negotiations.
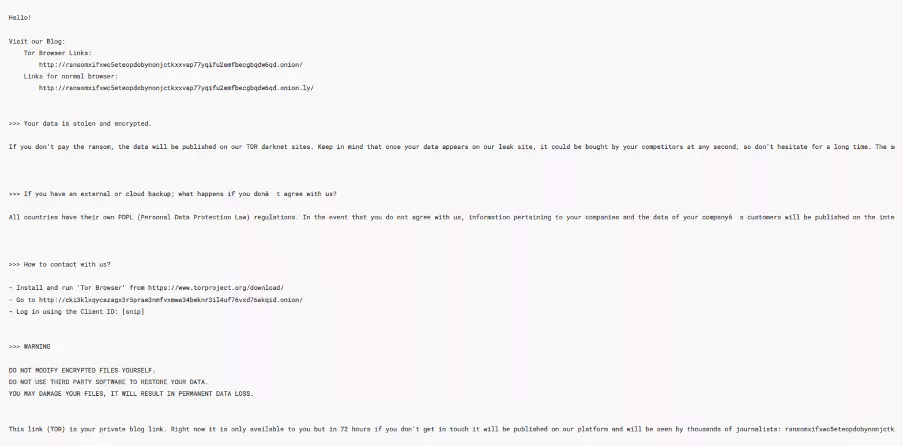
Figure 2: RansomHub Ransomware Encryption Message
RansomHub's most damaging strategy involves making files on compromised devices unusable by encrypting them. They follow this up by asking for a ransom to hand over the decryption keys. This approach has an impact on business activities and leaves victims with a tough choice: pay up or risk losing a lot of data.
What is the Kill Chain of RansomHub Ransomware Group?
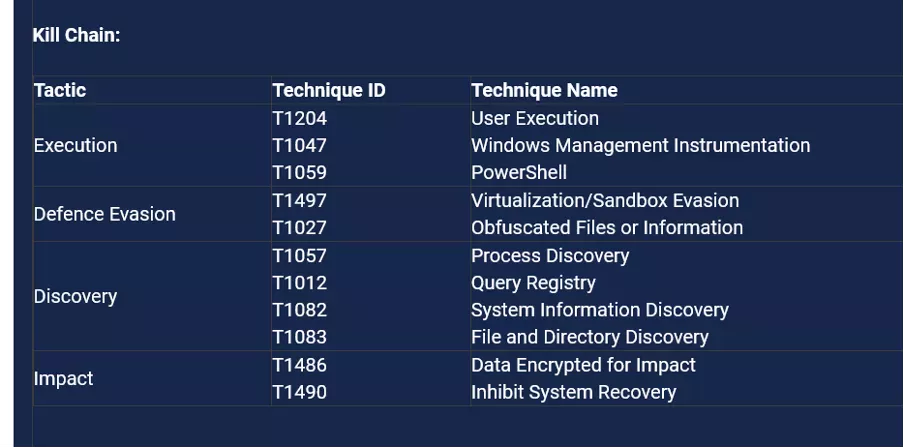
Figure 3: RansomHub Ransomware Kill Chain
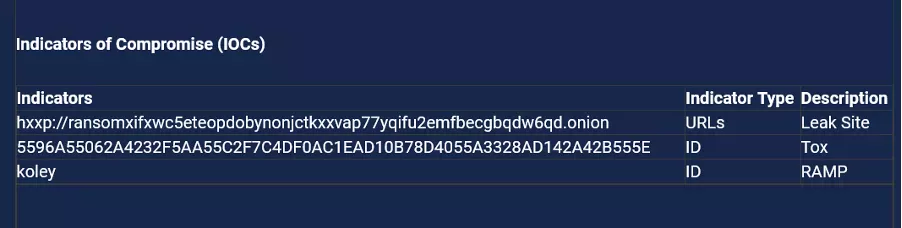
Figure 4: RansomHub Ransomware: Indicators of Compromise (IOCs)
The method via which cybercriminals execute cyberattacks is known as the "cyber kill chain." The figure 3 shows how the RansomHub ransomware group carries out their attacks. Indicators of Compromise (IOCs) are forensic data points that signal potential malicious activity within a network or system.
These can include file hashes, IP addresses, domain names, URLs, email addresses, registry keys, file names, and unusual behavioural patterns. The figure 4 shows the Indicators of Compromise (IOCs) of the RansomHub Ransomware group.
Here is a breakdown of each section:
The RansomHub ransomware group applies various techniques and strategies to attack and help them get away scot-free. They utilise methods such as User Execution, T1204, directly implying that the ransomware group requires a user to open a malicious file or click on a dangerous link. They also utilise Windows Management Instrumentation, T1047, for performing harmful actions and PowerShell, T1059, for running commands and scripts.
RansomHub uses methods like Virtualisation/Sandbox Evasion (T1497), which enables the ransomware group to recognise and avoid operating in sandboxes or virtual environments, to avoid detection. Additionally, they hide their code or data using Obfuscated Files or Information (T1027), which makes it harder for security tools to detect the ransomware.
In the context of discovery, RansomHub uses a variety of methods to compile details about the victim's network and system. They utilise Query Registry (T1012) to access the system registry, Process Discovery (T1057) to look at processes that are currently executing, and System Information Discovery (T1082) to gather hardware and operating system specifics. To find files and directories that could hold important information, File and Directory Discovery (T1083) is also utilised.
The group's main goal in terms of impact is to interfere with and harm the victim's systems and data. The method used in Data Encrypted for Impact (T1486) encrypts the victim's data, making it inaccessible until a ransom is paid.
Moreover, recovery options are disabled or removed using Inhibit System Recovery (T1490), which makes it challenging for victims to repair their computers without paying the ransom demands. These strategies demonstrate RansomHub's all-encompassing method of infiltrating targets and implementing its requests.
How Red Piranha Can Detect and Prevent RansomHub?
Red Piranha’s Crystal Eye, best-in-class Threat Detection, Investigation and Response (TDIR) provides robust protection against sophisticated threats like RansomHub by leveraging its advanced cybersecurity capabilities. With a visibility across networks, endpoints, and the cloud, Crystal Eye detects the initial stages of a RansomHub attack, such as phishing attempts and user execution of malicious files.
The platform's integrated email security identifies and quarantines malicious attachments, while its continuous monitoring and behavioural analytics swiftly detect and block suspicious activities, such as unauthorised PowerShell commands or WMI manipulations, preventing RansomHub from establishing a foothold within the network.
When RansomHub attempts to exploit known vulnerabilities like EternalBlue or PetitPotam, Crystal Eye’s integrated vulnerability management system steps in, proactively identifying and patching these vulnerabilities to close off key attack vectors.
If RansomHub tries lateral movement or privilege escalation, Crystal Eye’s continuous monitoring and automated response capabilities detect these unauthorised actions. The platform’s Intrusion Detection and Prevention System (IDPS) adds another layer of security, processing over 50,000 threats, identifying abnormal behaviour such as brute-force attempts on RDP or VPN services, and immediately locking down targeted accounts, effectively halting the attacker’s progress and containing the threat.
In the event RansomHub initiates data exfiltration or encryption processes, the automated threat intelligence and threat hunting capabilities come into play. The system's data loss prevention (DLP) policies stop unauthorised data transfers, while its ransomware detection algorithms halt encryption attempts.
Additionally, Crystal Eye ensures system recovery options remain intact, thwarting RansomHub’s efforts to disable them. Through continuous monitoring, integrated threat intelligence, IDPS, and a unified control plane, Crystal Eye offers a comprehensive defence against the full range of tactics employed by RansomHub, ensuring organisations can detect, prevent, and respond to these attacks effectively.
Does detecting malicious activity pose a significant challenge for your organisation?
From reconnaissance to the ultimate objectives, Crystal Eye provides comprehensive protection at every stage, detecting and blocking malicious payloads, preventing unauthorised installations, disrupting command and control communications, and stopping ransomware from achieving its devastating goals, ensuring that systems and data remain secure and operational.
Crystal Eye, best-in-class Threat Detection, Investigation and Response (TDIR), allows you to catch what the other products in its class missed by detecting all known malware and C2 callouts.
Improve your organisation's security posture and minimise risk to your organisation with our Network Detection and Response program alongside our Endpoint Detection and Response.
Red Piranha is a world leader when it comes to CTI. We are a member of the highly regarded Cyber Threat Alliance, and this appointment is a testament to our increased technical capabilities in this area and our commitment to quality with CTI. As one of its top contributors, we offer contextualised CTI feeds to its members and the wider security industry.
