Earlier this year "The Shadow Brokers" -- an entity claiming to have stolen hacking tools from the NSA then offering them for sale slipped into the darkness with little fanfare after the auction of the information failed to get any one excited. Today in the new post the information was released about tools and malware used by the NSA, the information includes everything from XP to Windows 8 working exploits. It is unclear at this stage if Windows 10 is effected as most of the data dates back to 2014.
The old debate has once again bubbled to the surface as once the release was offered for sale earlier this year what stopped the NSA from informing Microsoft of the potential for harm to it’s customers? It is nothing short of a dereliction of duty and irresponsible to say the least. Last night Red Piranha security researchers began pouring over the data to find out just how much risk the world has been exposed to from this leak. Releasing this information ahead of a holiday weekend can also make it harder for Microsoft and It workers to respond, and anyone with bad intentions can now download a simple toolkit to hack into Microsoft systems around the globe. A look at the data has shown the NSA can force you or anyone’s DNS server to transfer any zone file to them. ERRATICGOPHER is a remote RRAS exloit for Windows XP and Windows 2003 SP2. EWOKFRENZY and Emphasismine are exploits for IBM Lotus Domino and Eternalblue from Fuzzbunch is an 0day exploit that successfully gets a RCE on Windows 2008 SP1, the list goes on and we have way to many to mention here.
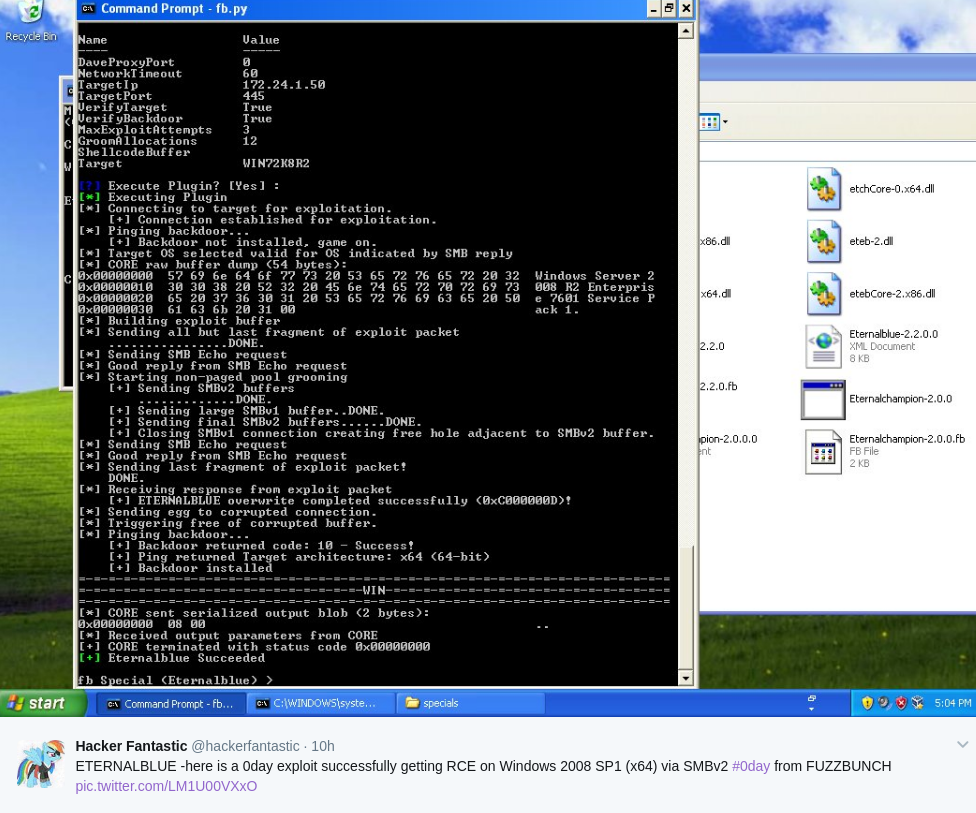
At this time, the response from a Microsoft spokesmen is that “We are reviewing the report and will take the necessary actions to protect our customers. But this is just not good enough, now that these 0days are public customers are at risk. Some mitigation exist you might want to try and not to run SMB, remove remote desktop and make sure all software is currently up to date. Microsoft will need to release fixes for several of the ETERNAL exploits and customers should ensure they apply them as soon as available.
So after the Snowden leaks and the Vault7 debacle does the NSA have a new scandal on its hands, Yes! The irresponsible nature of this non disclosure is near criminal. Once known of the breach all parties should have been notified and mitigation should have been made to limit the risk to enterprise around the world. If we as a society are going to allow our intelligence agencies to act with this sort of reach, we also need to make sure basic responsible measures are taken to mitigate risk. In this case this has not happened and shows a fundamental flaw with the mindset behind running operations like this from within our intelligence agencies.
Find the loopholes in your security. Contact us for Vulnerability Assessment and Penetration Testing.
