
We have all seen Microsoft products topping the vulnerability charts back in 2017. This year doesn’t look any different with major vulnerabilities making headlines frequently. A researcher published a Zero-day vulnerability on Twitter raising the eyebrows of security experts across the world since the vulnerability was made public before informing Microsoft.
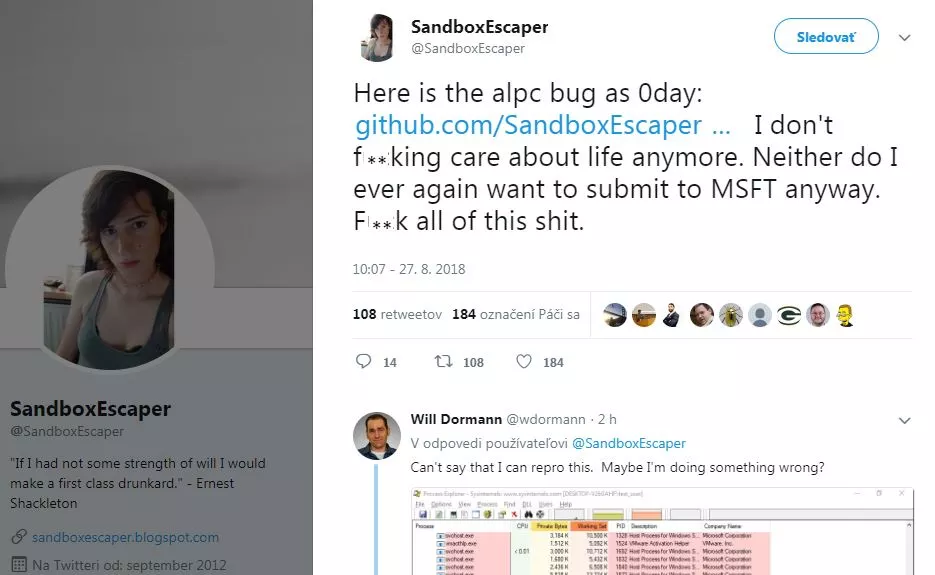
Apparently, the flaw was found in the Advanced Local Procedure Call (ALPC) systems of windows, which was later described as a local privilege escalation security flaw.
The researcher with a twitter handle by the name ‘SandboxEscaper’ published the GitHub link on Monday. The GitHub page supposedly displayed the proof of concept (PoC) until it was either taken down or was deleted by the researcher.
Vulnerability analyst at the CERT/CC, Will Dormann revealed in a tweet that he had verified the Zero-day vulnerability in a fully patched 64-bit windows 10 system. The flaw was found in the Microsoft windows task scheduler and after close observations it was concluded that the flaw was found in the handling process of the ALPC. The vulnerability if successfully exploited can result to local privilege escalation that can be used as a base to launch further attacks.
Will Dorman mentioned in the comments section of his tweet that, he was unaware of any workarounds for this vulnerability. Microsoft had rolled out its August patches recently were it issued fixes for about 60 flaws. However, according to experts it is expected to release patches for the ALPC bug next on September 11.
Don’t leave yourself exposed. Find your vulnerabilities before cybercriminals do. Contact us for Vulnerability Assessment and Penetration Testing.
