
The recent revelations regarding a malware campaign designed to target software supply chain is proving the fact that threat actors are evolving their tactics to fulfill their malicious intents. A PDF Editor App's font package was compromised recently and was used to deploy malicious Crypto-Currency Mining Malware. The multi-tier case was deemed unusual by Microsoft who detected the compromise that lasted between January to March 2018
The Supply Chain Within the Supply Chain Was the Target
The cyber criminals where able to sneak in the malware to the package developed by the partner vendors. The partner vendor developed font packages (Asian Fonts Packages) for the PDF Editor. The plot was skillfully executed by the malicious actors who went undetected while they replaced the font package with a malicious MSI file. One of the MSI file contained the code of a crypto-currency mining malware. It is now clear that there were multiple MSI files which contained digitally signed certificates of the same legitimate company. However, one of the MSI files lost the authenticity of the digitally signed certificates when the malicious crypto-mining code was injected to it. This was the file that threat hunters were able to identify without much difficulty and label it malicious.
How did the Attackers Manage to Get Full Elevated Privileges on the Affected Systems?
The malicious crypto-currency malware was injected to the font package used by the PDF App. The PDF App installer has elevated privileges (SYSTEM). The malware being a part of the package gained crucial system privilege that is required to copy files to the system folder and execute the malicious coin mining code. Infact the elevated system privileges also allowed adding unauthorized services.
The Attackers Created Identical Cloud Servers & Exploited an Unknown Weakness
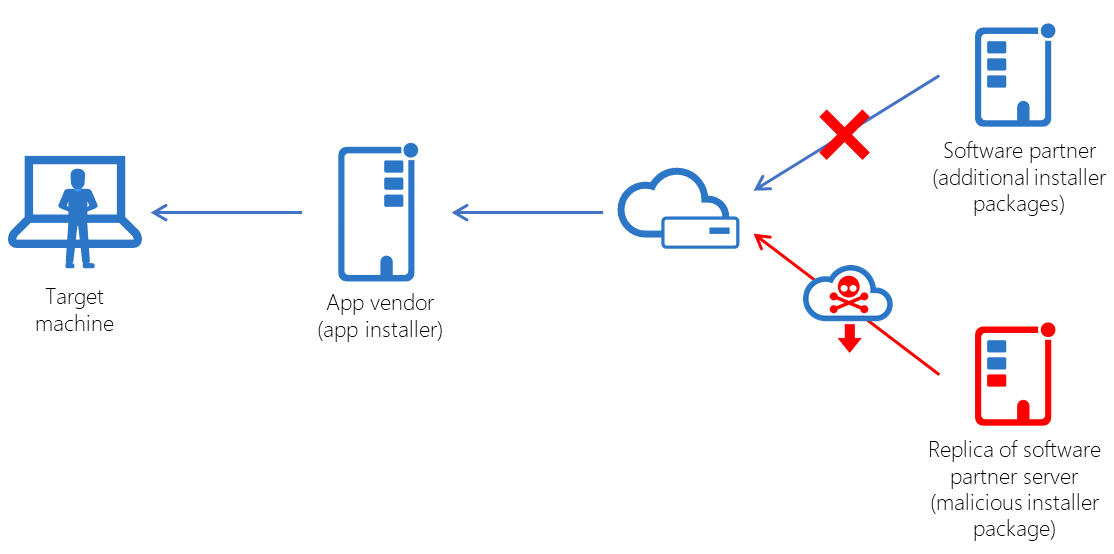
After elaborated investigations it is now known that the hackers exploited an unknown weakness in the interaction of the PDF App vendor and the vendor that provided the font package. The attackers successfully created an identical server like the one used by the partner vendor and hosted the MSI files and the font package in this server. The download parameters used by the PDF App was manipulated so that the target downloaded the malicious mining codes while installing the font packages.
Targeting Software Supply Chain Proving to be an Emerging Trend Among Threat Actors
Cyber criminals are constantly looking for the weakest point that can be exploited. Software supply chain seems to be the most unexpected attack vector and thus is now considered as the emerging attack vector in the cyber security community. Recent reports also suggest that such attacks are growing ever since malicious actors have realized that finding Zero-Day exploits involves greater levels of expertise, time and are also proving to be expensive. Another reason that accounts to threat actors using software supply chain as an attack vector is due to the prevalence of a huge user base that can be targeted through such attacks. Software vendors must work on securing loopholes in the supply chain and must co-ordinate with partner vendors to enhance their cyber security capabilities. The recent rise on software supply chain attacks has highlighted certain security lessons which must be taken seriously to minimize recurrence of such attacks in the future.
