Remote Access Trojan C&C Servers Found
| Amadey |
2 |
8.208.90.28 , 91.203.192.199 |
| Anubis |
2 |
45.141.86.67 , 45.143.137.28 |
| Azorult |
2 |
103.83.81.17 , 88.98.24.67 |
| BlackNet |
3 |
185.239.236.74 , 40.87.40.177 , 64.225.31.236 |
| CobaltStrike |
1 |
8.208.12.69 |
| DiamondFox |
4 |
165.22.30.153 , 168.235.67.97 , 213.159.203.232 , 47.254.149.61 |
| Heodo |
11 |
125.0.215.60 , 152.170.79.100 , 173.70.61.180 , 186.147.237.3 , 190.247.139.101 , 201.143.224.27 , 5.2.136.90 , 59.21.235.119 , 66.57.108.14 , 82.48.39.246 , 90.160.138.175 |
| Loader |
1 |
45.141.84.187 |
| Lokibot |
1 |
213.159.212.148 |
| Nexus |
2 |
141.8.192.151 , 87.236.16.62 |
| Predator |
3 |
141.8.193.236 , 185.50.25.27 , 185.50.25.51 |
| SmokeLoader |
1 |
5.61.35.193 |
| Trickbot |
18 |
107.152.46.188 , 107.172.188.113 , 158.51.96.31 , 185.198.59.45 , 198.144.191.144 , 198.44.97.143 , 198.46.198.115 , 198.46.198.116 , 34.209.40.84 , 45.14.226.101 , 45.155.173.248 , 45.83.151.103 , 45.89.125.214 , 52.90.110.55 , 54.184.178.68 , 64.74.160.218 , 64.74.160.228 , 66.70.246.0 |
| Unknown |
2 |
8.208.24.255 , brdjbk4daam647jak4vf4ue7xtg5flympsujyup2xbci2npxrjxgujyd.onion |
| Zloader |
1 |
185.240.102.113 |
| zTDS |
1 |
45.150.206.246 |
|

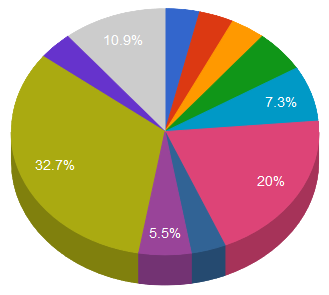

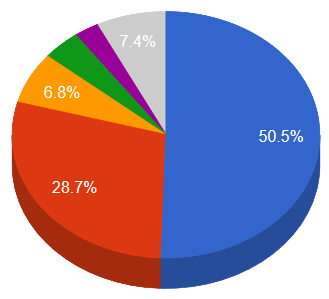
 China
China United States
United States Canada
Canada Russia
Russia Vietnam
Vietnam Other
Other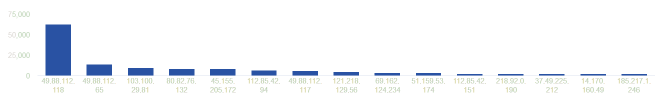
 DiamondFox
DiamondFox Heodo
Heodo Nexus
Nexus Predator
Predator TrickBot
TrickBot