Trends
- The top attacker country was China with 218118 unique attackers (58.08%).
- The top Trojan C&C server detected was Lokibot with 13 instances detected.
- The top phishing campaign detected was against Facebook accounts with 49 instances detected.
Fake Zoom Invite Warning: The meeting request that cost $8.7 millionA fraudulent Zoom invite has forced Australian based hedge fund Levitas Capital to collapse after one of its founders clicked on a link within a fake meeting request. The fake invite then planted malicious software within the organisation's network, allowing them full access to their email systems. Cybercriminals were then able to distribute counterfeit invoices to the tune of $8.7 million. The Australian Competition and Consumer Commission (ACCC) has seen a steep increase in cybercriminals targeting businesses with email compromised scams. In 2019 Australian companies lost over $132 million. Additionally, the ACCC noted that the most financially damaging business email scams involved invoices between suppliers, or other businesses being intercepted and updated with fake banking details.
|
|
| Top Attackers By Country| China | 218118 | 58.08% | | United States | 76974 | 20.50% | | Canada | 27055 | 7.20%% | | Brazil | 25675 | 6.84% | | Netherlands | 5192 | 1.38% | | Russia | 4131 | 1.10% | | India | 4084 | 1.09% | | France | 3948 | 1.05% | | Hong Kong | 1980 | 0.53% | | Colombia | 1765 | 0.47% | | Thailand | 1718 | 0.46% | | Malaysia | 1254 | 0.33% | | Italy | 1057 | 0.28% | | Philippines | 1034 | 0.28% | | Iran | 783 | 0.21% | | Seychelles | 778 | 0.21% |
|
|
| Top Attackers By Country | 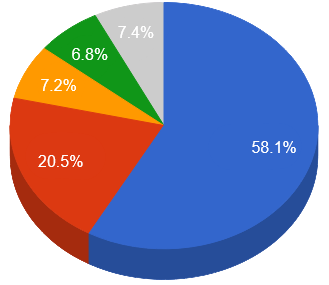 |  China China United States United States Canada Canada
|  Brazil Brazil Other Other
|
|
|
|
| |
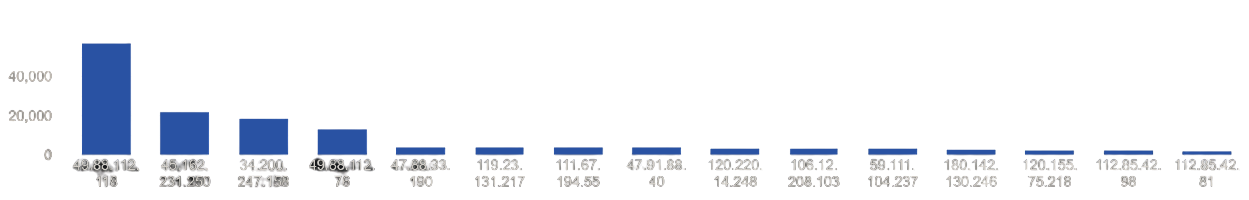
| Top Attacking Hosts| 49.88.112.118 | 57065 | | 45.162.231.250 | 22025 | | 34.200.247.158 | 18511 | | 49.88.112.76 | 13194 | | 118.137.212.54 | 9998 | | 47.88.33.190 | 3878 | | 119.23.131.217 | 3865 | | 111.67.194.55 | 3853 | | 47.91.88.40 | 3824 | | 120.220.14.248 | 3604 | | 106.12.208.103 | 3283 | | 59.111.104.237 | 3252 | | 180.142.130.246 | 2877 | | 120.155.75.218 | 2525 | | 112.85.42.98 | 2292 | | 1.129.109.100 | 2023 | | 112.85.42.81 | 1966 |
|
Top Attackers
 |
|
|
| Top Network Attackers| 4134 | China | CHINANET-BACKBONE No.31,Jin-rong Street, CN | | 268581 | Brazil | QNAX LTDA, BR | | 14618 | United States | AMAZON-AES, US | | 45102 | United States | CNNIC-ALIBABA-US-NET-AP Alibaba (US) Technology Co., Ltd., CN | | 37963 | China | CNNIC-ALIBABA-CN-NET-AP Hangzhou Alibaba Advertising Co.,Ltd., CN | | 4808 | China | CHINA169-BJ China Unicom Beijing Province Network, CN | | 24444 | China | CMNET-V4SHANDONG-AS-AP Shandong Mobile Communication Company Limited, CN | | 38365 | China | BAIDU Beijing Baidu Netcom Science and Technology Co., Ltd., CN | | 45062 | China | NETEASE-AS Guangzhou NetEase Computer System Co., Ltd., CN | | 134419 | China | CHINATELECOM-GUANGXI-BEIHAI-MAN Beihai, CN | | 4837 | China | CHINA169-BACKBONE CHINA UNICOM China169 Backbone, CN |
|
|
|
| Remote Access Trojan C&C Servers Found| AgentTesla | 3 | 103.207.39.131 , 192.210.214.146 , 45.137.202.22 | | ATSEngine | 1 | 8.208.97.57 | | BlackNet | 2 | 141.8.193.236 , 185.239.242.117 | | CryptBot | 1 | 47.254.173.45 | | Heodo | 6 | 103.229.72.197 , 161.0.153.60 , 190.18.184.113 , 201.102.218.101 , 24.101.229.82 , 24.69.65.8 | | Kpot | 2 | 199.192.29.90 , 80.78.22.80 | | LoaderJS | 1 | 93.115.21.62 | | Lokibot | 13 | 104.18.47.150 , 104.18.54.93 , 104.24.96.103 , 104.28.5.218 , 172.67.202.227 , 185.209.1.109 , 185.209.1.129 , 193.106.175.41 , 195.22.153.143 , 209.59.188.68 , 70.32.23.26 , 92.242.40.195 , 92.242.40.224 | | Nexus | 1 | 78.138.96.3 | | Oski | 1 | 80.89.230.198 | | ParasiteHTTP | 1 | 185.139.69.193 | | Pony | 1 | 185.139.69.193 | | Predator | 2 | 141.8.192.151 , 195.161.114.130 | | Qudox | 1 | 83.220.168.237 | | Redirected | 1 | 104.248.93.101 | | TrickBot | 5 | 141.136.0.4 , 156.96.119.28 , 162.212.158.135 , 199.189.108.71 , 51.75.222.163 | | UAdmin | 6 | 103.155.92.222 , 23.94.245.10 , 45.140.147.8 , 45.9.148.116 , 47.88.11.25 , 95.217.248.42 | | VKeyLogger | 3 | 170.106.35.220 , 185.136.169.200 , 45.15.143.167 | | Zloader | 1 | 8.208.97.57 |
|
Trojan C&C Servers Detected
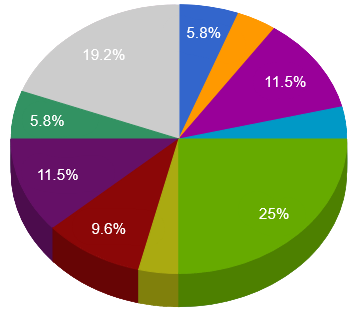 |  AgentTesla AgentTesla Trickbot Trickbot BlackNet BlackNet VKeyLogger VKeyLogger UAdmin/li> UAdmin/li>
|  Kpot Kpot Heodo Heodo Lokibot Lokibot Predator Predator Other Other
|
|
|
|
|
| Common Malware| dd726d5e223ca762dc2772f40cb921d3 | https://www.virustotal.com/gui/file/432fc2e3580e818fd315583527ae43a729586af5ee37f99f04b562d1eff2a1fd/detection | ww24.exe | N/A | W32.TR:Attribute.23ln.1201 | | ce4395edbbf9869a5e276781af2e0fb5 | https://www.virustotal.com/gui/file/f059a5358c24cc362c2f74b362c75e02035fdf82f9ffae8d553afee1a271afd0/details | wupxarch635.exe | N/A | W32.Auto:f059a5358c.in03.Talos | | 8c80dd97c37525927c1e549cb59bcbf3 | https://www.virustotal.com/gui/file/85b936960fbe5100c170b777e1647ce9f0f01e3ab9742dfc23f37cb0825b30b5/detection | Eternalblue-2.2.0.exe | N/A | Win.Exploit.Shadowbrokers::5A5226262.auto.talos | | 920823d1c5cb5ce57a7c69c42b60959c | https://www.virustotal.com/gui/file/100318042c011363a98f82516b48c09bbcdd016aec557b009c3dd9c17eed0584/details | FlashHelperService.exe | FlashHelperService | W32.Variant.23mj.1201 | | e2ea315d9a83e7577053f52c974f6a5a | https://www.virustotal.com/gui/file/c3e530cc005583b47322b6649ddc0dab1b64bcf22b124a492606763c52fb048f/detection | c3e530cc005583b47322b6649ddc0dab1b64bcf22b124a492606763c52fb048f.bin | N/A | Win.Dropper.Agentwdcr::1201 |
|
|
| Top Phishing Campaigns| Other | 1683 | | Facebook | 49 | | DHL | 3 | | PayPal | 5 | | Virustotal | 4 | | Amazon.com | 11 | | Steam | 1 | | Sparkasse | 1 | | Google | 6 | | Special | 1 | | Adobe | 3 | | Apple | 2 | | Microsoft | 4 | | Vodafone | 4 | | Halifax | 22 | | Caixa | 1 |
|
|
|
|
CVEs with Recently Discovered Exploits This is a list of recent vulnerabilities for which exploits are available. CVE-2020-16898Microsoft Windows TCP/IP Stack Remote Code Execution VulnerabilityMicrosoft | A remote code execution vulnerability exists when the Windows TCP/IP stack improperly handles ICMPv6 Router Advertisement packets. An attacker who successfully exploited this vulnerability could gain the ability to execute code on the target server or client. To exploit this vulnerability, an attacker would have to send specially crafted ICMPv6 Router Advertisement packets to a remote Windows computer. | CVSSv3BaseScore:9.8(AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H) | 10/16/2020 | 10/23/2020 | CVE-2020-15647Mozilla Firefox Arbitrary Local File Access VulnerabilityMozilla | A Content Provider in Firefox for Android allowed local files accessible by the browser to be read by a remote webpage, leading to sensitive data disclosure, including cookies for other origins. | CVSSv3BaseScore:7.8(AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:N/A:N) | 08/10/2020 | 08/12/2020 | CVE-2020-14815Oracle Business Intelligence Unauthorized Access VulnerabilityOracle | A vulnerability exists in the Oracle Business Intelligence Enterprise Edition product of Oracle Fusion Middleware. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise Oracle Business Intelligence Enterprise Edition. Successful attacks require human interaction from a person other than the attacker and while the vulnerability is in Oracle Business Intelligence Enterprise Edition, attacks may significantly impact additional products. Successful attacks of this vulnerability can result in unauthorized access to critical data or complete access to all Oracle Business Intelligence Enterprise Edition accessible data as well as unauthorized update, insert or delete access to some of Oracle Business Intelligence Enterprise Edition accessible data. | CVSSv3BaseScore:8.2(AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:L/A:N) | 10/21/2020 | 10/23/2020 | CVE-2020-26217XStream Remote Code Execution VulnerabilityMulti-vendor | XStream is vulnerable to Remote Code Execution vulnerability that may allow a remote attacker to run arbitrary shell commands only by manipulating the processed input stream. Only users who rely on blocklists are affected. | CVSSv3BaseScore:8.0(AV:N/AC:H/PR:L/UI:R/S:C/C:H/I:H/A:H) | 11/16/2020 | 11/17/2020 | CVE-2020-14882Oracle WebLogic Server Remote Code Execution VulnerabilityOracle | Oracle WebLogic Server (formerly known as BEA WebLogic Server) is an application server for building and deploying enterprise applications and services. A remote code execution vulnerability exists in the Oracle WebLogic Server product of Oracle Fusion Middleware | CVSSv3BaseScore:9.8(AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H) | 10/21/2020 | 11/19/2020 | CVE-2020-1472Microsoft Netlogon Elevation of Privilege VulnerabilityMicrosoft | An elevation of privilege vulnerability exists when an attacker establishes a vulnerable Netlogon secure channel connection to a domain controller, using the Netlogon Remote Protocol (MS-NRPC). An attacker who successfully exploited the vulnerability could run a specially crafted application on a device on the network. To exploit the vulnerability, an unauthenticated attacker would be required to use MS-NRPC to connect to a domain controller to obtain domain administrator access. | CVSSv3BaseScore:10.0(AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H) | 08/17/2020 | 11/23/2020 | CVE-2020-8271Citrix SD-WAN Center Remote Code Execution VulnerabilityCitrix | Multiple vulnerabilities have been discovered in Citrix SD-WAN Center that, if exploited, could allow an unauthenticated attacker with network access to SD-WAN Center to perform arbitrary code execution as root. A successful exploit could allow the attacker to perform arbitrary code execution as root. | CVSSv3BaseScore:9.9(AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H) | 11/15/2020 | 11/16/2020 | CVE-2020-3471Cisco Webex Meetings Server Unauthorized Audio Information Exposure VulnerabilityCisco | A vulnerability in Cisco Webex Meetings and Cisco Webex Meetings Server could allow an unauthenticated, remote attacker to maintain bidirectional audio despite being expelled from an active Webex session. The vulnerability is due to a synchronization issue between meeting and media services on a vulnerable Webex site. A successful exploit could allow the attacker to maintain the audio connection of a Webex session despite being expelled. | CVSSv3BaseScore:6.5(AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:N/A:N) | 11/18/2020 | 11/19/2020 |
| |
|
|
|
|

