Trends
-
The top attacker country was China with 160695 unique attackers (57.05%).
-
The top phishing campaign detected was against Facebook accounts with 49 instances detected.
Microsoft Office Phishing Attack Hosted on Google Firebase
Security Researchers at Armour Blox have uncovered a phishing campaign designed to steal Microsoft login credentials via invoice-themed emails sent out to at least 20,000 recipients. The emails conveyed a realistic subject line of ‘Transfer of Payment Notice for Invoice” and contained a link to download the ‘invoice’ from the cloud.
Upon clicking the link, the target is lead through several re-directs, landing a Microsoft branded landing page was designed to collect Microsoft login credentials, secondary email addresses, phone numbers.
Google’s new Open-Source Vulnerability Database
Google has recently launched the OSV, an Open-Source Vulnerabilities website as their first step towards improving vulnerability triage for developers and consumers of open-source software.
OSV has been developed to provide precise data on how the vulnerability was introduced and where it was fixed—enabling consumers of open-source software to determine if they were impacted and make the required security adjustments to their systems and software.
Google has stated that it has two primary goals for OSV:
-
"Reduce the work required by maintainers to publish vulnerabilities.
-
Improve the accuracy of vulnerability queries for downstream consumers by providing precise vulnerability metadata in an easy-to-query database (complementing existing vulnerability databases)."
Commonwealth Ombudsman finds instances of telco data accessed without authority at all agencies inspected.
Last week the Federal Government tabled the Commonwealth Ombudsman's report on agency access to stored communications and telecommunications data for 2018-2019. While the Ombudsman was overall upbeat concerning the overall improvement of most agencies data compliance requirements, all agencies reviewed failed to follow the legal authorisation requirements.
Agencies included within the Ombudsman's report include:
- Australian Federal Police
- Australian Criminal Intelligence Commission,
- Department of Home Affairs advice
- New South Wales Police
- Queensland Police Force
- Tasmanian Police Force
- Victorian Police Force and
- The Western Australian Police Force
"We identified instances at all inspections in 2018-19, where agencies had accessed telecommunications data without proper authority. As such, the disclosure of the data was unauthorised," the report [PDF] said in the section dedicated to telco data inspections".
|
|
|
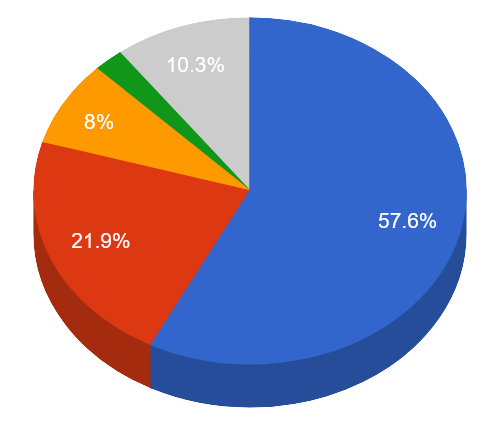
Top Attackers By Country
| China |
160695 |
57.05% |
| United States |
61257 |
21.75% |
| Poland |
22282 |
7.91% |
| Japan |
6265 |
2.22% |
| Vietnam |
4587 |
1.62% |
| Brazil |
4050 |
1.43% |
| France |
3748 |
1.33% |
| South Korea |
3683 |
1.30% |
| India |
3354 |
1.19% |
| Indonesia |
2741 |
0.97% |
| Canada |
2314 |
0.82% |
| Pakistan |
1006 |
0.35% |
| Dominican Republic |
995 |
0.35% |
| Argentina |
883 |
0.31% |
| Mexico |
874 |
0.31% |
| Thailand |
475 |
0.16% |
|
|
|
Top Attackers By Country
|
 |
 China China United States United States Poland Poland Japan Japan Others Others
|
|
|
|
|
|
|
|
Top Attacking Hosts
| 61.177.173.25 |
40468 |
| 185.16.38.95 |
22282 |
| 218.92.0.200 |
13932 |
| 61.177.173.19 |
8070 |
| 121.218.35.122 |
6969 |
| 150.95.173.242 |
6265 |
| 61.177.173.12 |
5545 |
| 27.54.253.241 |
5056 |
| 111.85.53.58 |
4244 |
| 58.53.128.82 |
4219 |
| 218.92.0.201 |
3788 |
| 69.162.124.234 |
3297 |
| 149.167.140.234 |
3012 |
| 111.33.65.38 |
2994 |
| 101.99.23.65 |
2343 |
| 159.75.50.105 |
2086 |
| 152.136.133.145 |
1561 |
| 172.20.29.251 |
1489 |
|
Top Attackers
 |
|
|
|
Top Network Attackers
| 4134 |
China |
CHINANET-BACKBONE No.31,Jin-rong Street, CN |
| 201814 |
Poland |
PL-SKYTECH-AS, PL |
| 7506 |
Japan |
INTERQ GMO Internet,Inc, JP |
| 4837 |
China |
CHINA169-BACKBONE CHINA UNICOM China169 Backbone, CN |
| 46475 |
United States |
LIMESTONENETWORKS, US |
| 38019 |
China |
CMNET-V4TIANJIN-AS-AP tianjin Mobile Communication Company Limited, CN |
| 45903 |
Vietnam |
CMCTELECOM-AS-VN CMC Telecom Infrastructure Company, VN |
| 45090 |
China |
CNNIC-TENCENT-NET-AP Shenzhen Tencent Computer Systems Company Limited, CN |
|
|
|
|
Common Malware
| 9a4b7b0849a274f6f7ac13c7577daad8 |
https://www.virustotal.com/gui/file/c1d5a585fce188423d31df3ea806272f3daa5eb989e18e9ecf3d94b97b965f8e/details |
ww31.exe |
N/A |
W32.GenericKD:Attribute.24ch.1201 |
| 176e303bd1072273689db542a7379ea9 |
https://www.virustotal.com/gui/file/8cb8e8c9fafa230ecf2f9513117f7679409e6fd5a94de383a8bc49fb9cdd1ba4/details |
FlashHelperService.exe |
FlashHelperService |
W32.Variant.24cl.1201 |
| 6a7401614945f66f1c64c6c845a60325 |
https://www.virustotal.com/gui/file/b76fbd5ff8186d43364d4532243db1f16f3cca3138c1fab391f7000a73de2ea6/details |
pmropn.exe |
PremierOpinion |
PUA.Win.Adware.Relevantknowledge::231753.in02 |
| 8c80dd97c37525927c1e549cb59bcbf3 |
https://www.virustotal.com/gui/file/85b936960fbe5100c170b777e1647ce9f0f01e3ab9742dfc23f37cb0825b30b5/detection |
Eternalblue-2.2.0.exe |
N/A |
Win.Exploit.Shadowbrokers::5A5226262.auto.talos |
| 34560233e751b7e95f155b6f61e7419a |
https://www.virustotal.com/gui/file/8b4216a7c50599b11241876ada8ae6f07b48f1abe6590c2440004ea4db5becc9/details |
SAntivirusService.exe |
AntivirusService |
PUA.Win.Dropper.Segurazo::tpd |
|
|
|
|
Top Phishing Campaigns
| Other |
1232 |
| Facebook |
49 |
| Amazon.com |
14 |
| Google |
13 |
| AOL |
1 |
| Instagram |
18 |
| Caixa |
12 |
| PayPal |
8 |
| Allegro |
14 |
| WeTransfer |
2 |
| Virustotal |
1 |
| Adobe |
6 |
| Special |
2 |
| DHL |
1 |
| Microsoft |
4 |
| Giffgaff |
1 |
| Itau |
1 |
| Apple |
3 |
| EE |
2 |
|
|
|
|
CVEs with Recently Discovered Exploits
This is a list of recent vulnerabilities for which exploits are available.
CVE-2021-1144
Cisco Connected Mobile Experiences Privilege Escalation Vulnerability
Cisco
|
A vulnerability in Cisco Connected Mobile Experiences (CMX) could allow a remote, authenticated attacker without administrative privileges to alter the password of any user on an affected system. The vulnerability is due to incorrect handling of authorization checks for changing a password. An authenticated attacker without administrative privileges could exploit this vulnerability by sending a modified HTTP request to an affected device. A successful exploit could allow the attacker to alter the passwords of any user on the system, including an administrative user, and then impersonate that user. |
CVSSv3BaseScore:9.8(AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H) |
01/13/2021 |
01/20/2021 |
CVE-2021-25311
HTCondor Directory Traversal Vulnerability
HTcondor
|
condor_credd in HTCondor before 8.9.11 allows Directory Traversal outside the SEC_CREDENTIAL_DIRECTORY_OAUTH directory, as demonstrated by creating a file under /etc that will later be executed by root. |
9.9(AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H) |
01/27/2021 |
02/01/2021 |
CVE-2021-1647
Microsoft Defender Remote Code Execution Vulnerability
Microsoft
|
This vulnerability exists in Microsoft's Defender antivirus software. Attackers can write specially crafted files that can be run immediately when Microsoft Defender initiates the scans. Attackers can use this vulnerability not only to bypass Microsoft anti-virus software but also to use Microsoft anti-virus software to run malicious software to launch an attack. This means that an attacker can launch an on-interactive attack, such as sending a specially crafted file as an email attachment, and the email client will trigger a scan after receiving it. |
3.1(AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H) |
01/12/2021 |
01/14/2021 |
CVE-2020-4888
IBM QRadar SIEM Deserialization of Untrusted Data
IBM
|
IBM QRadar SIEM 7.4.0 to 7.4.2 Patch 1 and 7.3.0 to 7.3.3 Patch 7 could allow a remote attacker to execute arbitrary commands on the system, caused by insecure deserialization of user-supplied content by the Java deserialization function. By sending a malicious serialized Java object, an attacker could exploit this vulnerability to execute arbitrary commands on the system. |
8.8(AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H) |
01/28/2021 |
02/02/2021 |
|
|
|

