Remote Access Trojan C&C Servers Found
| AgentTesla |
1 |
72.9.135.10 |
| Amadey |
7 |
176.123.8.254 , 217.8.117.168 , 217.8.117.177 , 217.8.117.62 , 217.8.117.81 , ixlosa.com , vintrsi.com |
| ATSEngine |
2 |
170.106.35.220 , 94.100.28.209 |
| BlackNet |
1 |
51.254.73.16 |
| BlueBotNet |
1 |
158.247.208.239 |
| CryptBot |
2 |
185.209.1.123 , 185.252.146.49 |
| DT-Stealer |
1 |
45.13.252.21 |
| Heodo |
8 |
108.21.72.56 , 175.145.248.25 , 190.251.216.100 , 191.223.36.170 , 202.79.24.136 , 45.184.103.73 , 45.4.32.50 , 54.36.185.60 |
| KeitaroTDS |
2 |
213.226.100.238 , 87.236.16.241 |
| Lokibot |
12 |
103.83.81.68 , 104.31.64.98 , 137.59.52.154 , 172.67.188.73 , 172.67.201.179 , 185.243.215.88 , 193.106.175.41 , 209.59.188.68 , 209.59.188.68 , 45.144.2.145 , 45.144.2.145 , 46.17.98.105 |
| Oski |
1 |
45.137.67.174 |
| Pony |
1 |
103.20.212.86 |
| Qudox |
1 |
188.120.228.107 |
| Redirected |
2 |
209.250.255.176 , 209.97.175.120 |
| RedLine |
25 |
104.31.68.21 , 138.124.180.187 , 168.119.175.149 , 172.67.192.79 , 176.119.158.210 , 185.250.148.63 , 188.119.113.157 , 195.93.173.94 , 206.166.251.156 , 2.56.214.31 , 45.142.215.39 , 45.144.29.87 , 45.150.67.48 , 45.67.228.55 , 45.67.231.94 , 5.252.194.139 , 84.38.183.201 , 86.105.252.12 , 86.106.181.103 , 93.115.18.189 , 93.115.20.250 , 94.103.95.7 , 94.140.115.81 , 94.23.199.195 , 95.181.155.62 |
| Rurat |
1 |
46.17.98.47 |
| Taurus |
2 |
172.67.171.50 , 172.67.220.64 |
| TrickBot |
17 |
156.96.156.165 , 185.14.29.119 , 185.163.45.140 , 185.234.72.75 , 185.244.151.107 , 187.62.208.234 , 192.119.171.218 , 194.5.249.29 , 195.123.240.108 , 195.123.242.176 , 212.8.251.21 , 23.237.137.66 , 45.12.110.179 , 86.104.194.16 , 94.140.114.99 , 94.140.115.150 , 94.140.115.189 |
| TriumphLoader |
3 |
1193.106.175.51 , 45.129.2.130 , 78.155.205.58 |
| Zloader |
1 |
185.240.102.113 |
|

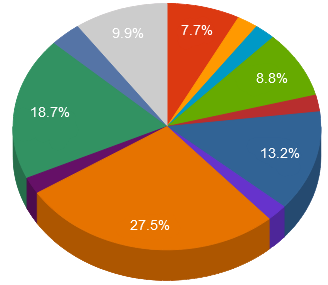

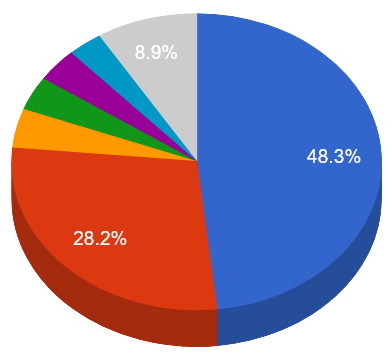
 China
China United States
United States Brazil
Brazil India
India Russia
Russia South Korea
South Korea Other
Other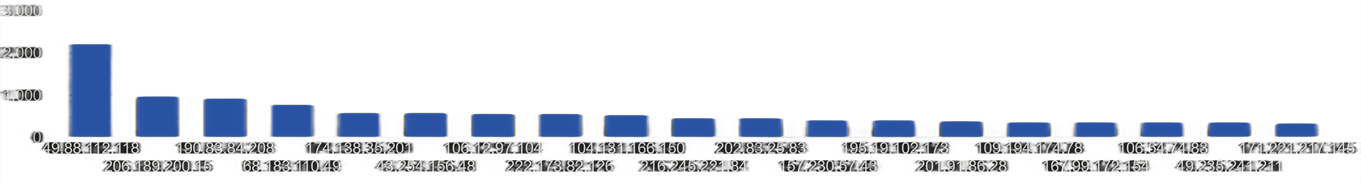
 Heodo
Heodo KeitaroTDS
KeitaroTDS Redirected
Redirected RedLine
RedLine Taurus
Taurus TriumphLoader
TriumphLoader