CVE-2018-13379
Fortinet FortiOS Directory Traversal Vulnerability
Fortinet
|
Fortinet FortiOS is exposed to a directory traversal vulnerability because it fails to properly sanitize user supplied input. A path traversal vulnerability in the FortiOS SSL VPN web portal may allow an unauthenticated attacker to download FortiOS system files through specially crafted HTTP resource requests. |
CVSSv3BaseScore:9.8(AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H) |
06/04/2019 |
11/19/2020 |
CVE-2020-14882
Oracle WebLogic Server Remote Code Execution Vulnerability
Oracle
|
Oracle WebLogic Server (formerly known as BEA WebLogic Server) is an application server for building and deploying enterprise applications and services. A remote code execution vulnerability exists in the Oracle WebLogic Server product of Oracle Fusion Middleware |
CVSSv3BaseScore:9.8(AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H) |
10/21/2020 |
11/19/2020 |
CVE-2020-15505
MobileIron Core and Connector Remote Code Execution Vulnerability
MobileIron
|
A remote code execution vulnerability exists in MobileIron Core and Connector, and Sentry, that allows remote attackers to execute arbitrary code via unspecified vectors. The manipulation with an unknown input leads to a privilege escalation vulnerability. The UK's National Cyber Security Centre alerts that APT nation-state groups and cybercriminals are exploiting MobileIron RCE vulnerability to compromise the networks. |
CVSSv3BaseScore:9.8(AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H) |
07/06/2020 |
11/10/2020 |
CVE-2020-5902
F5 BIG-IP Remote Code Execution Vulnerability
F5
|
F5 BIG-IP is exposed to remote code execution vulnerability. The vulnerability that has been actively exploited in the wild allows attackers to read files, execute code or take complete control over vulnerable systems having network access. |
CVSSv3BaseScore:9.8(AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H) |
07/01/2020 |
08/07/2020 |
CVE-2020-9844
MacOS Catalina Memory Corruption Vulnerability
Apple
|
A double free issue was addressed with improved memory management. A remote attacker may be able to cause unexpected system termination or corrupt kernel memory. |
CVSSv3BaseScore:7.5(AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H) |
6/09/2020 |
10/16/2020 |
CVE-2018-12809
Adobe Experience Manager Server-Side Request Forgery Vulnerability
Adobe
|
Adobe Experience Manager is exposed to server-side request forgery vulnerability. Successful exploitation could lead to sensitive information disclosure. |
CVSSv3BaseScore:7.5(AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N) |
07/20/2018 |
09/17/2018 |
CVE-2020-1472
Microsoft Netlogon Elevation of Privilege Vulnerability
Microsoft
|
An elevation of privilege vulnerability exists when an attacker establishes a vulnerable Netlogon secure channel connection to a domain controller, using the Netlogon Remote Protocol (MS-NRPC). An attacker who successfully exploited the vulnerability could run a specially crafted application on a device on the network. To exploit the vulnerability, an unauthenticated attacker would be required to use MS-NRPC to connect to a domain controller to obtain domain administrator access. |
CVSSv3BaseScore:10.0(AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H) |
08/17/2020 |
11/23/2020 |

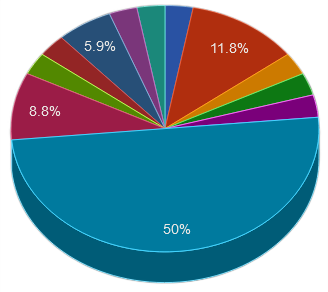


 United States
United States Russia
Russia China
China India
India Germany
Germany Netherlands
Netherlands Other
Other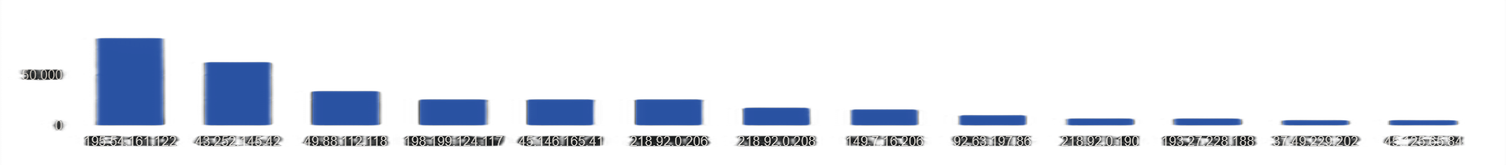
 Azorult
Azorult Loader
Loader Stealer
Stealer Trickbot
Trickbot Zloader
Zloader