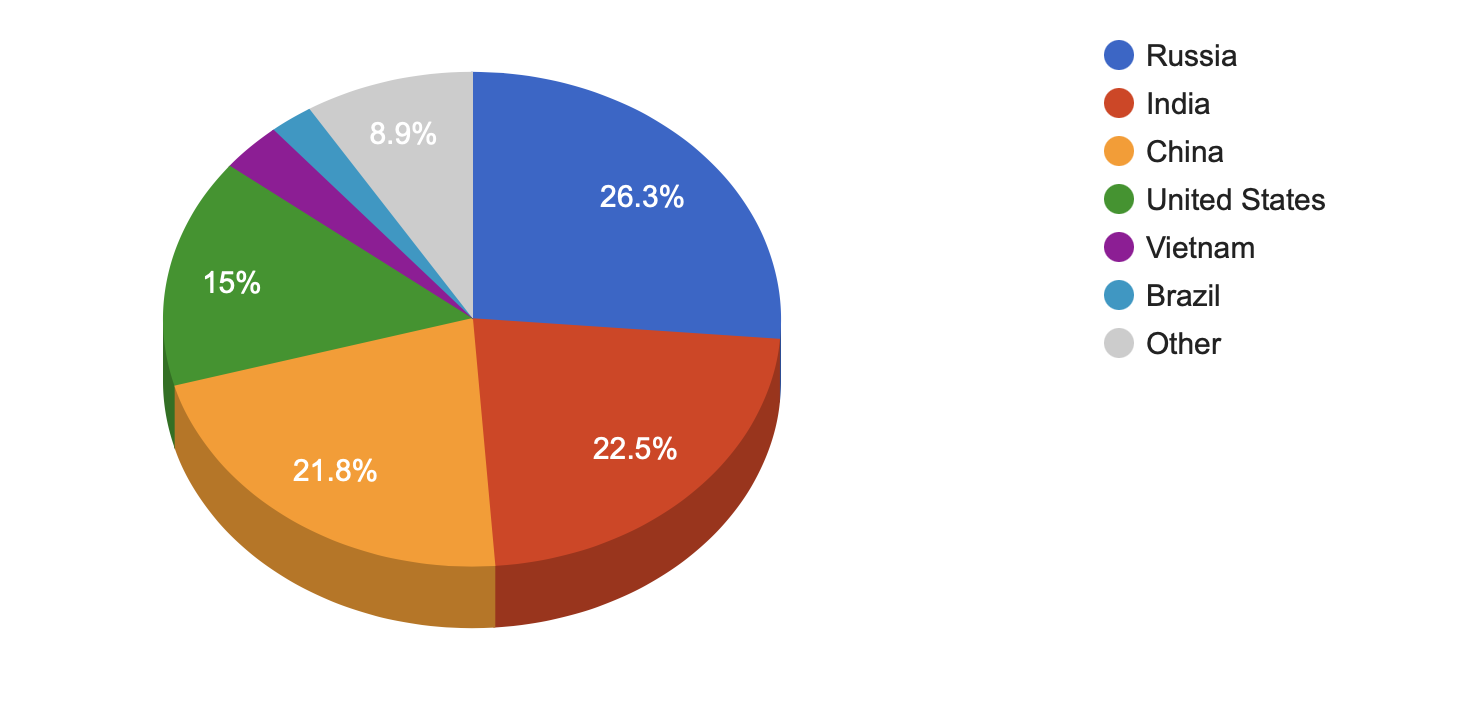
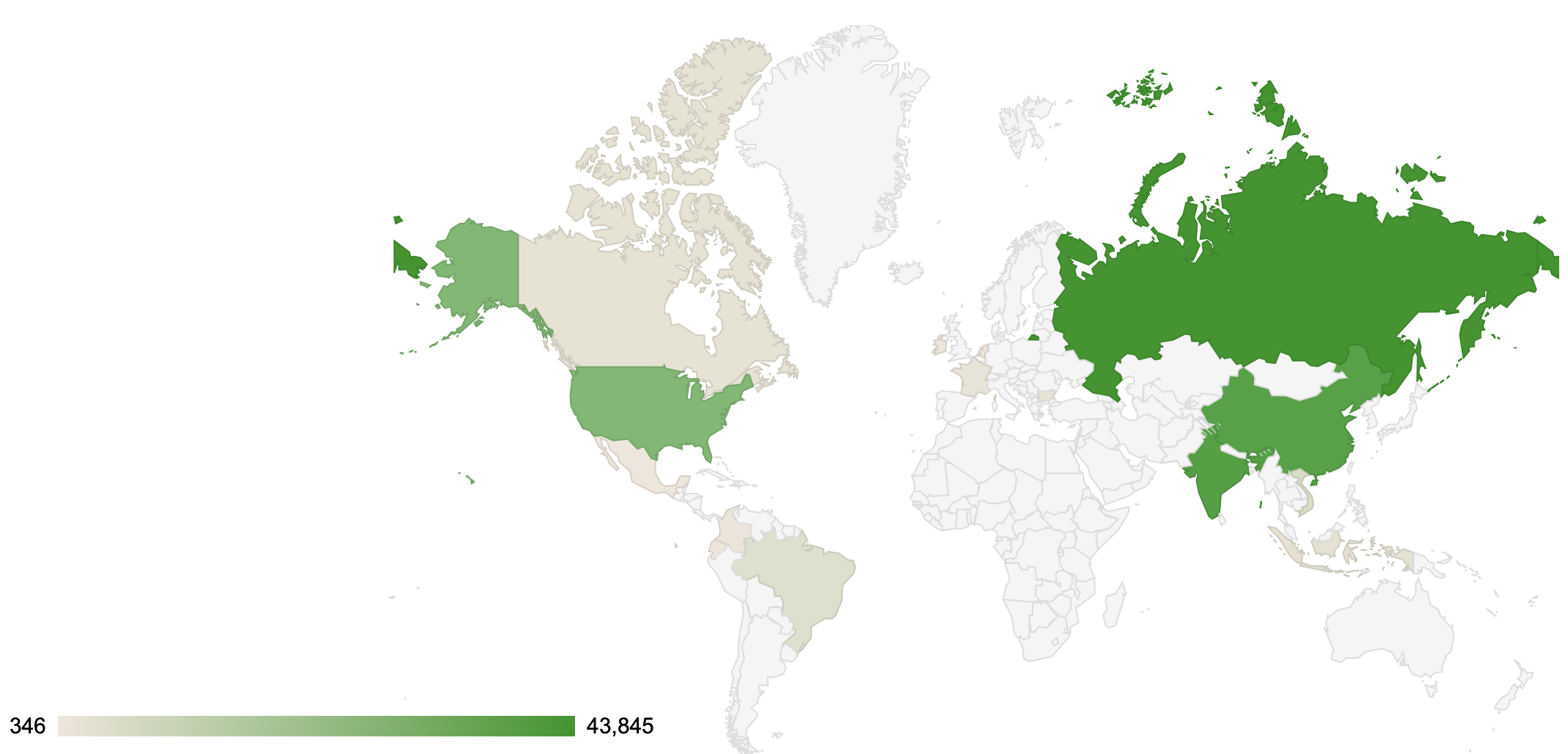
CVE-2021-30177SQL Injection Vulnerability in PHPNukePHPNuke | There is a SQL Injection vulnerability in PHP-Nuke 8.3.3 in the User Registration section, leading to remote code execution. This occurs because the U.S. state is not validated to be two letters, and the OrderBy field is not validated to be one of LASTNAME, CITY, or STATE. | 9.8 (AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H) | 04/07/2021 | 04/13/2021 |
CVE-2021-28925SQL Injection Vulnerability in NagiosNagios | SQL injection vulnerability in Nagios Network Analyzer before 2.4.3 via the o[col] parameter to api/checks/read/. | 9.8 (AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H) | 04/08/2021 | 04/13/2021 |
CVE-2021-24175Authentication Bypass Vulnerability in Posimyth WP PluginPosimyth | The Plus Addons for Elementor Page Builder WordPress plugin before 4.1.7 was being actively exploited to by malicious actors to bypass authentication, allowing unauthenticated users to log in as any user (including admin) by just providing the related username, as well as create accounts with arbitrary roles, such as admin. These issues can be exploited even if registration is disabled, and the Login widget is not active. | 9.8 (AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H) | 04/05/2021 | 04/09/2021 |
CVE-2021-1871Remote Code Execution Vulnerability in MacOS Big SurApple | A logic issue was addressed with improved restrictions. This issue is fixed in macOS Big Sur 11.2, Security Update 2021-001 Catalina, Security Update 2021-001 Mojave, iOS 14.4 and iPadOS 14.4. A remote attacker may be able to cause arbitrary code execution. Apple is aware of a report that this issue may have been actively exploited. | 9.8 (AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H) | 04/02/2021 | 04/12/2021 |
CVE-2020-17523Authentication Bypass Vulnerability in Apache ShiroApache | Apache Shiro before 1.7.1, when using Apache Shiro with Spring, a specially crafted HTTP request may cause an authentication bypass. | 9.8 (AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H) | 02/03/2021 | 04/12/2021 |
CVE-2021-22986Remote Code Execution Vulnerability in F5 Big IP systemF5 | This vulnerability allows for unauthenticated attackers with network access to the iControl REST interface, through the BIG-IP management interface and self IP addresses, to execute arbitrary system commands, create or delete files, and disable services. This vulnerability can only be exploited through the control plane and cannot be exploited through the data plane. Exploitation can lead to complete system compromise. The BIG-IP system in Appliance mode is also vulnerable. | 9.8 (AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H) | 03/31/2021 | 04/05/2021 |
CVE-2021-21983Privilege Escalation Vulnerability in VMware vRealizeVMware | Arbitrary file write vulnerability in vRealize Operations Manager API (CVE-2021-21983) prior to 8.4 may allow an authenticated malicious actor with network access to the vRealize Operations Manager API can write files to arbitrary locations on the underlying photon operating system. | 6.5 (AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:H/A:H) | 03/31/2021 | 04/05/2021 |