| New Threat Detection Added | 3 (DoNot Group (APT-C-35), Colibri Loader Malware, and Gomorrah Stealer Malware) |
| New Threat Protections | 149 |
Weekly Detected Threats
The following threats were added to Crystal Eye XDR this week:
Threat name: | DoNot Group (APT-C-35) | |||||||||||||||||||||
DoNot, also known as APT-C-35, is a sophisticated cyber threat actor group, widely recognised for its advanced capabilities in espionage and cyber warfare. Operating since at least 2014, DoNot primarily targets governmental, diplomatic, and military entities across the Middle East and South Asia, with a focus on Pakistan. Their modus operandi includes spear-phishing, malware deployment, and social engineering tactics to gain unauthorised access to sensitive information and conduct espionage activities. DoNot's arsenal often includes custom-developed malware and exploits, showcasing their high level of technical expertise. Their activities highlight the persistent and evolving nature of cybersecurity threats in the modern digital landscape. | ||||||||||||||||||||||
Threat Protected: | 05 | |||||||||||||||||||||
Rule Set Type: |
| |||||||||||||||||||||
Class Type: | Trojan-activity | |||||||||||||||||||||
Kill Chain: |
| |||||||||||||||||||||
Threat name: | Colibri Loader Malware | |||||||||||||||||||||
Colibri Loader is a potent malware loader utilised by cybercriminals to deploy various types of malicious payloads onto compromised systems. Emerging in recent years, it operates stealthily, evading detection by security software through encryption and obfuscation techniques. Colibri Loader's modular design allows it to adapt to different attack scenarios, facilitating the distribution of ransomware, banking Trojans, and other malware strains. It often spreads through phishing emails or exploit kits, leveraging social engineering tactics to trick users into executing it. Once installed, Colibri Loader acts as a gateway for further malicious activities, underscoring the persistent threat posed by sophisticated malware in cyberspace. | ||||||||||||||||||||||
Threat Protected: | 01 | |||||||||||||||||||||
Rule Set Type: |
| |||||||||||||||||||||
Class Type: | Trojan-activity | |||||||||||||||||||||
Kill Chain: |
| |||||||||||||||||||||
Threat name: | Gomorrah Stealer Malware | ||||||||||||||||||||||||
Gomorrah Stealer initiates its operations by collecting data on the operating system, processor, memory (RAM), device name, and anti-virus/security software. This malicious software specialises in extracting information, primarily passwords, from browsers such as Google Chrome, Mozilla Firefox, Opera, Amigo, Brave, Comodo, Kometa, Orbitum, Torch, and Yandex. Additionally, it targets other applications like Mozilla Thunderbird (email client), FileZilla (FTP - File Transfer Protocol client), Pidgin (IM - Instant Messaging client), and Proxifier (proxy server support). Gomorrah aims to pilfer cryptocurrency wallet credentials and credit card details. It can download various files from desktops and document folders, including databases (MySQL, SQLite, SQL server backups, and Microsoft Access), documents/text files (.txt, .doc, .docx, .xlsx, and .pdf), images (.jpg, .png, .gif, and .jpge), and log files (.log). Another capability of Gomorrah is capturing screenshots. | |||||||||||||||||||||||||
Threat Protected: | 01 | ||||||||||||||||||||||||
Rule Set Type: |
| ||||||||||||||||||||||||
Class Type: | Trojan-activity | ||||||||||||||||||||||||
Kill Chain: |
| ||||||||||||||||||||||||
Known exploited vulnerabilities (Week 3 - April 2024)
Threat | CVSS | Description | |
CVE-2024-28253 | 9.4 (Critical) | OpenMetadata Code Injection vulnerability | |
CVE-2024-28254 | 8.8 (High) | OpenMetadata OS Command injection vulnerability | |
CVE-2024-28255 | 9.8 (Critical) | OpenMetadata Authentication Bypass vulnerability | |
CVE-2024-28847 | 8.8 (High) | OpenMetadata Code Injection vulnerability | |
CVE-2024-28848 | 8.8 (High) | OpenMetadata Code Injection vulnerability |
Updated Malware Signatures (Week 3 - April 2024)
Threat | Description | |
Upatre | Upatre is also a malware dropper that downloads additional malware on an infected machine. It is usually observed to drop banking trojan after the initial infection. | |
Remcos | Remcos functions as a remote access trojan (RAT), granting unauthorised individuals the ability to issue commands on the compromised host, record keystrokes, engage with the host's webcam, and take snapshots. Typically, this malicious software is distributed through Microsoft Office documents containing macros, which are often attached to malicious emails. | |
QuasarRat | A remote access trojan that was made available to the public as an open-source project. Once installed on a victim’s machine, it is capable of keylogging, data and screen capturing among other things. It is also known to be highly customisable depending on the threat actor’s intended need. | |
Bifrost | A remote access trojan that enables its operator to take control of a victim machine and steal data. It is usually distributed through spam and phishing emails. |
| Ransomware Report | |
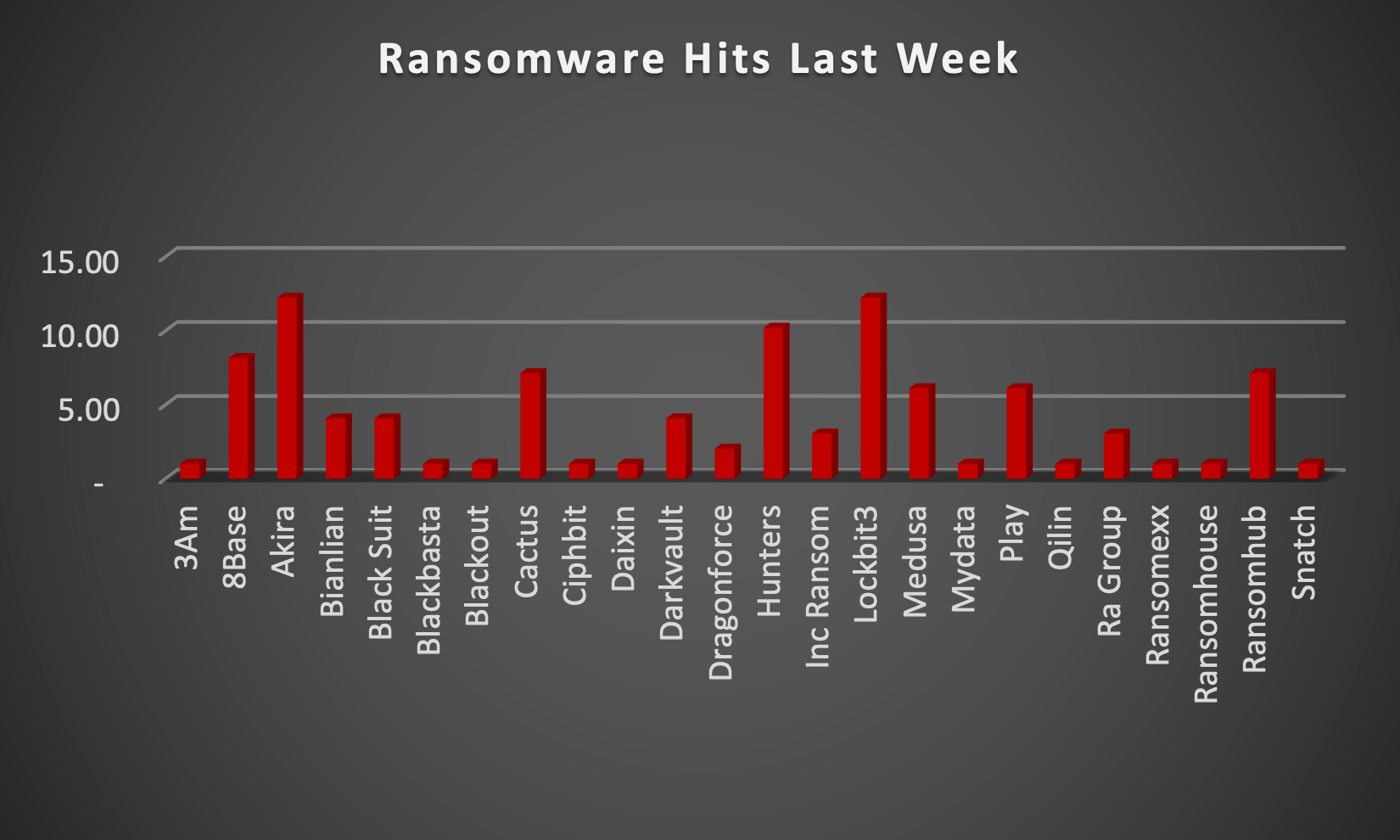
The Red Piranha Team actively collects information on organisations globally affected by ransomware attacks from various sources, including the Dark Web. In the past week alone, our team uncovered new ransomware victims and updates on previous victims across 20 different industries spanning 19 countries. This underscores the widespread and indiscriminate impact of ransomware attacks, emphasising their potential to affect organisations of varying sizes and sectors worldwide. Akira and Lockbit3.0 ransomware stand out as the most prolific, having updated a significant number of victims (12%) each distributed across multiple countries. In comparison, Hunters International ransomware updated 10% victims each, in the past week. The following list provides the victim counts in percentages for these ransomware groups and a selection of others. | |
| Name of Ransomware Group | Percentage of new Victims last week |
3Am | 1.02% |
8Base | 8.16% |
Akira | 12.24% |
Bianlian | 4.08% |
Black Suit | 4.08% |
Blackbasta | 1.02% |
Blackout | 1.02% |
Cactus | 7.14% |
Ciphbit | 1.02% |
Daixin | 1.02% |
Darkvault | 4.08% |
Dragonforce | 2.04% |
Hunters International | 10.20% |
INC Ransom | 3.06% |
Lockbit3 | 12.24% |
Medusa | 6.12% |
Mydata | 1.02% |
Play | 6.12% |
Qilin | 1.02% |
Ra Group | 3.06% |
Ransomexx | 1.02% |
Ransomhouse | 1.02% |
Ransomhub | 7.14% |
Snatch | 1.02% |
Akira Ransomware Group Relatively new, Akira first appeared in Q1 2023. By January 2024, they had impacted over 250 organisations globally, extorting a staggering $42 million. This rapid growth placed them among the top ransomware threats, particularly for critical infrastructure. Akira has targeted a wide range of businesses and government entities across North America, Europe, and Australia. Critical infrastructure hasn't been spared, making them a serious concern for national security. Tactics, Techniques, and Procedures (TTPs) Initial Access: They gain access through various means, including - VPN Exploits: A favourite target is vulnerabilities in Virtual Private Networks (VPNs), particularly Cisco ASA SSL VPN and Cisco AnyConnect. These vulnerabilities (like CVE-2020-3259 and CVE-2023-20269) allow them to bypass security if Multi-Factor Authentication (MFA) isn't enabled on the VPN. Lack of Multi-Factor Authentication (MFA): Akira heavily relies on exploiting systems where MFA is not enforced. MFA adds an extra layer of security beyond just usernames and passwords, making it significantly harder for unauthorised access. Remote Desktop Protocol (RDP) Attacks: In some cases, Akira targets RDP (Remote Desktop Protocol) to gain initial access. This can involve brute-force attacks on weak passwords or exploiting known vulnerabilities in RDP software. Stolen Credentials: The group may also take advantage of stolen usernames and passwords obtained through phishing campaigns or purchased on the dark web. Lateral Movement: Once inside, they disable security software and employ techniques to move laterally across the network, granting them broader access to valuable data. Encryption: Akira utilises a hybrid encryption combining Chacha20 and RSA algorithms, making decryption challenging. They also target shadow copies to prevent easy data recovery. Variants: The group uses strains written in C++ and Rust, with file extensions like .akira and .powerranges. Their malware, Megazord, written in Rust, emerged in April 2023 targeting Linux servers. Impact: Akira's success highlights the growing sophistication of ransomware attacks. Their focus on critical infrastructure raises concerns about potential disruption to essential services. Data Leak Site: They maintain a dark web leak site (Akira) where they threaten to publish stolen data from unpaid victims. Ransom Note: Kill Chain:
Indicators of Compromise (IOCs)
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
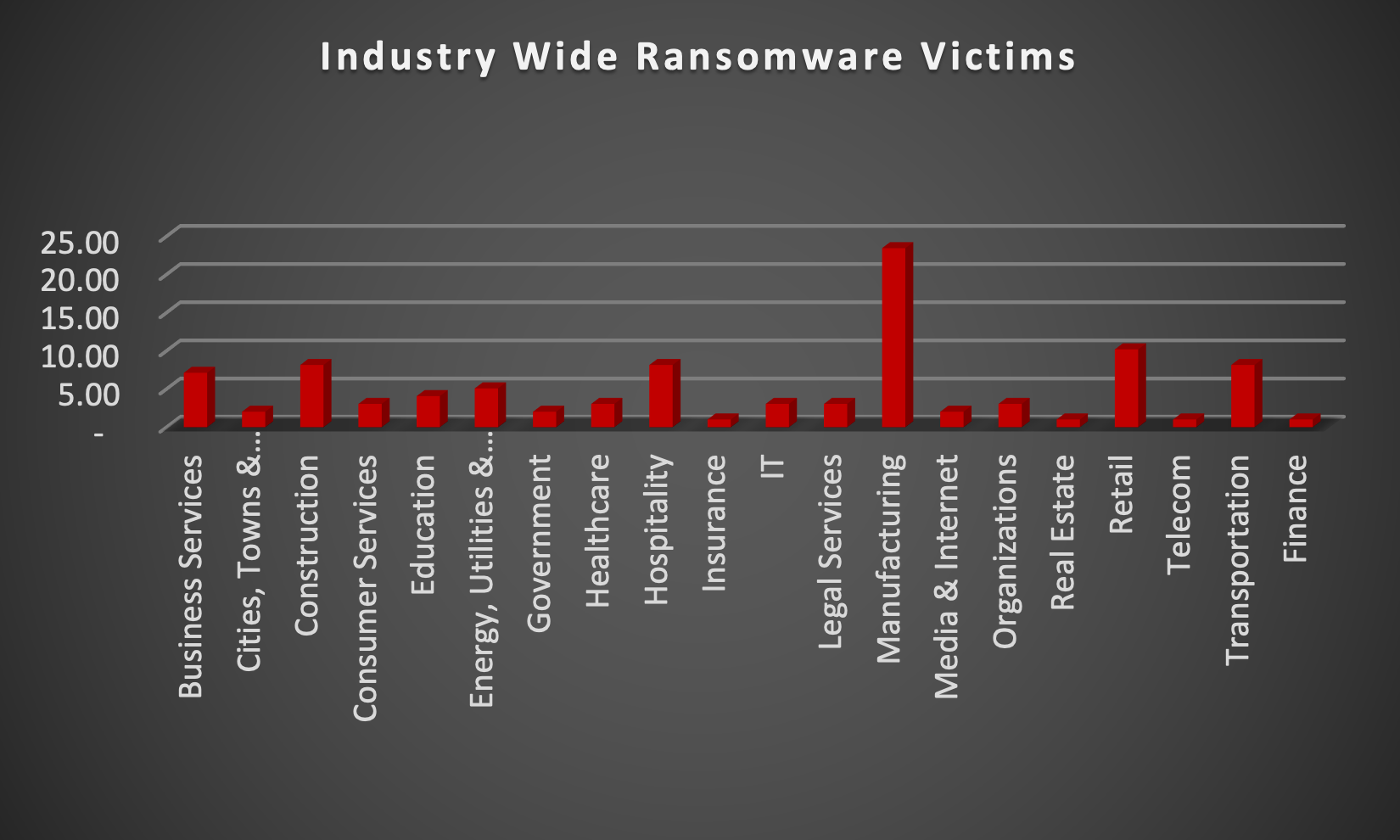
Upon further investigation, it has been identified that ransomware has left its mark on 20 different industries worldwide. Notably, Manufacturing bore the brunt of the attacks in the past week, accounting for 23% of victims. There are a few key reasons why the manufacturing sector is a prime target for ransomware groups:
High Disruption Potential: Manufacturing relies heavily on interconnected systems and just-in-time production. A ransomware attack can grind operations to a halt, causing significant financial losses due to production delays and lost revenue. This pressure to get back online quickly can make manufacturers more willing to pay the ransom.
Vulnerable Legacy Systems: Many manufacturers use legacy control systems (OT) that haven't been updated for security. These older systems often lack robust security features, making them easier targets for attackers to exploit.
Limited Cybersecurity Investment: Traditionally, cybersecurity might not have been a top priority for some manufacturers compared to production efficiency. This lack of investment in security awareness training and robust security protocols leaves them exposed.
Valuable Data: Manufacturing facilities often hold valuable intellectual property (IP) and trade secrets. Ransomware groups may not only disrupt operations but also threaten to leak this sensitive data if the ransom isn't paid.
Success Breeds Success: The high payout potential from past attacks on manufacturers incentivises ransomware groups to continue targeting them.
The table below delineates the most recent ransomware victims, organised by industry, shedding light on the sectors grappling with the significant impact of these cyber threats.
Name of the affected Industry | Victims Count (%) |
Business Services | 7.14% |
Cities, Towns & Municipalities | 2.04% |
Construction | 8.16% |
Consumer Services | 3.06% |
Education | 4.08% |
Energy, Utilities & Waste Treatment | 5.10% |
Government | 2.04% |
Healthcare | 3.06% |
Hospitality | 8.16% |
Insurance | 1.02% |
IT | 3.06% |
Legal Services | 3.06% |
Manufacturing | 23.47% |
Media & Internet | 2.04% |
Organisations | 3.06% |
Real Estate | 1.02% |
Retail | 10.20% |
Telecom | 1.02% |
Transportation | 8.16% |
Finance | 1.02% |