
| New Threat Detection Added | 5 (CrossLock Ransomware, DAAM Android Botnet, Sliver, CVE-2021-20090, and ScarCruft APT) |
| New Threat Protections | 9 |
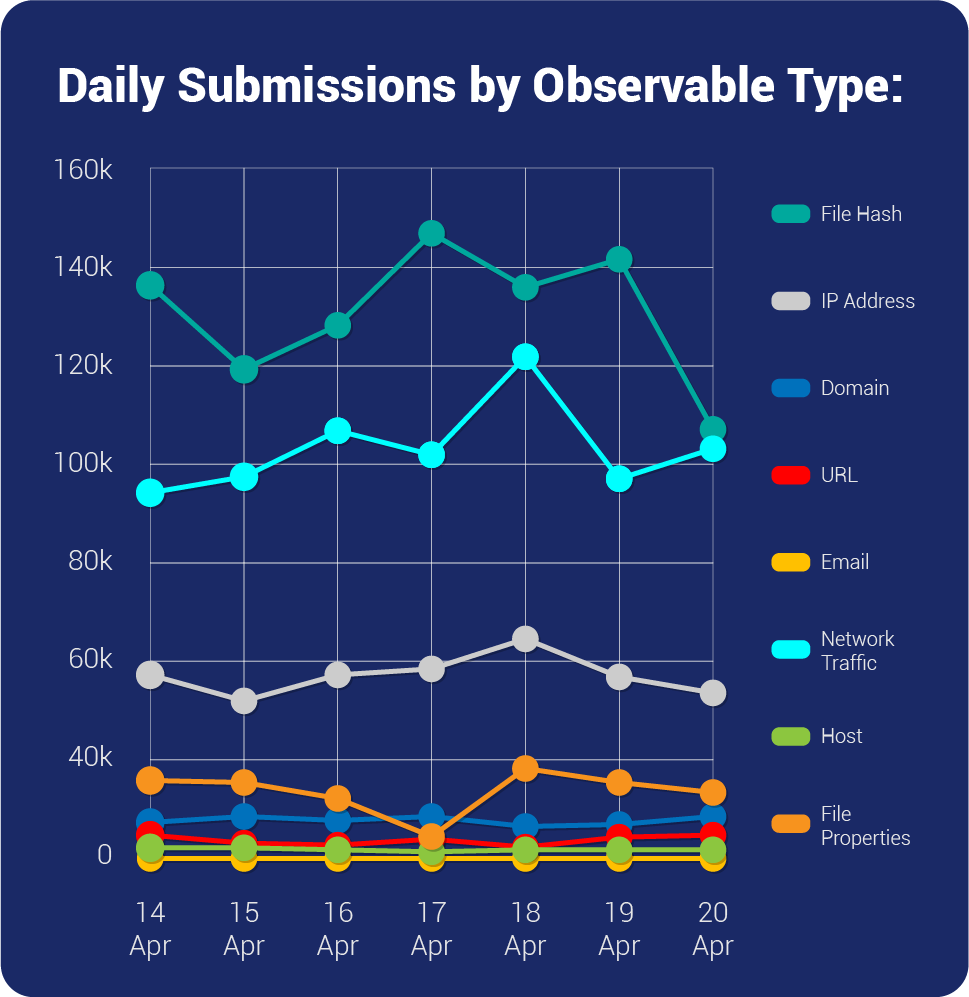
| Overall Weekly Observables Count | 2,409,148 |
| New Ransomware Victims Last Week | 83 |
Weekly Detected Threats
The following threats were added to Crystal Eye XDR this week:
Threat name: | CrossLock Ransomware | ||||||||||||||||||
CrossLock is a newly emerged ransomware group that targets businesses, demanding a significant ransom in return. Along with encrypting the victim's files, the attackers also adopt double-extortion tactics by stealing sensitive data and threatening to release it on their onion leak site unless the ransom is paid. The threat actors behind the CrossLock ransomware have coded it using the Go programming language, which offers numerous advantages. One such benefit is the ability to compile a single codebase that can function across various operating systems. However, the use of Event Trace (ETW) bypass techniques by this ransomware is particularly concerning. This feature allows the malware to avoid detection by security systems that rely on event logs. Moreover, CrossLock Ransomware employs several measures to lower the chances of data recovery and increase the attack's effectiveness. | |||||||||||||||||||
Threat Protected: | 01 | ||||||||||||||||||
Rule Set Type: |
| ||||||||||||||||||
Class Type: | Trojan-activity | ||||||||||||||||||
Kill Chain: | Execution T1059/T1204/T1047 - Defence Evasion T1564/T1027/T1497/T1070 - Discovery T1082/T1135/T1083/T1057 - Impact T1486/T1490 | ||||||||||||||||||
| Threat name: | DAAM Android Botnet | ||||||||||||||||||
A new Android botnet called DAAM has been discovered which is being distributed through trojanised applications. This botnet is capable of executing a variety of malicious actions, including data theft, DDoS attacks, and spamming. It uses a Command-and-Control infrastructure to communicate with its operators and receive instructions. Technical details about the botnet's functionality and the trojanised applications being used to distribute it have been provided by the researchers. To prevent falling prey to such botnets, downloading apps from trustworthy sources is critical. As the DAAM botnet is a significant threat to Android users, it is necessary to stay vigilant and take necessary precautions to avoid being infected. | |||||||||||||||||||
Threat Protected: | 02 | ||||||||||||||||||
Rule Set Type: |
| ||||||||||||||||||
Class Type: | Trojan-activity | ||||||||||||||||||
Kill Chain: | Initial Access T1476/T1444 - Collection T1433/T1432/T1429/T1512/T1414 - Discovery T1418 - Persistence T1402 - Impact T1471 | ||||||||||||||||||
| Threat name: | Sliver | ||||||||||||||||||
Sliver is an adversarial attack simulation tool designed to elude security products developed by researchers at BishopFox cybersecurity company. Sliver was utilised as a beachhead for the initial infection toolchain. It is utilised in the ransomware delivery framework for attacks observed in the wild. Sliver deployed via active opportunistic scanning and possible exploitation of Log4j/VMware Horizon vulnerabilities. It is utilised in targeting organisations within the Government, Research, Telecom, and University sectors, in addition to sporadic victims of opportunity. | |||||||||||||||||||
Threat Protected: | 01 | ||||||||||||||||||
Rule Set Type: |
| ||||||||||||||||||
Class Type: | Malware | ||||||||||||||||||
Kill Chain: | Execution TA0002 - Privilege Escalation TA0004 - Defence Evasion TA0005 - Discovery TA0007 - Command-and-Control TA0011 | ||||||||||||||||||
| Threat name: | CVE-2021-20090 | ||||||||||||||||||
A path traversal vulnerability in the web interfaces of networking devices manufactured by Arcadyan, including Buffalo WSR-2533DHPL2 firmware version <= 1.02 and WSR-2533DHP3 firmware version <= 1.24, could allow unauthenticated remote attackers to bypass authentication. The vulnerability exists due to a list of folders which fall under a "bypass list" for authentication. For most of the devices listed, that means that the vulnerability can be triggered by multiple paths. To have the pages load properly, one will need to use proxy match/replace settings to ensure any resources loaded which require authentication also leverage the path traversal. | |||||||||||||||||||
Threat Protected: | 01 | ||||||||||||||||||
Rule Set Type: |
| ||||||||||||||||||
Class Type: | Trojan | ||||||||||||||||||
Kill Chain: | Initial Access T1190 - Execution T1059 - Command-and-Control T1071 | ||||||||||||||||||
| Threat name: | ScarCruft APT | ||||||||||||||||||
ScarCruft is an APT group that has been observed to target the healthcare, telecommunications, and technology sectors. They are known to use a variety of TTPs including spear-phishing and watering hole attacks. They are attributed to the Operation Daybreak campaign where an Adobe 0-day was used. Such campaigns happened in early 2016 which also indicates that the APT group is constantly evolving. | |||||||||||||||||||
Threat Protected: | 04 | ||||||||||||||||||
Rule Set Type: |
| ||||||||||||||||||
Class Type: | Trojan-activity | ||||||||||||||||||
Kill Chain: | Initial Access T1566 - Execution T1059 - Command-and-Control T1102/T1071 | ||||||||||||||||||
Known exploited vulnerabilities (Week 3 April 2023):
For more information, refer to the Forum – Security Advisory
| Vulnerability | Description |
CVE-2023-2033 | Google Chromium V8 Engine Type Confusion Vulnerability |
CVE-2019-8526 | Apple macOS Use-After-Free Vulnerability |
CVE-2017-6742 | Cisco IOS and IOS XE Software SNMP Remote Code Execution Vulnerability |
Updated Malware Signatures (Week 3 April 2023)
Threat | Description |
| TeslaCrypt | A ransomware that started in the year 2015. It is usually distributed through spam email campaigns, malicious attachments, and exploit kits. |
| Zeus | Also known as Zbot and is primarily designed to steal banking credentials |
| DarkKomet | A remote access trojan that can take full control over an infected machine. |
| Bunitu | A malware that turns infected machines into a Proxy server for threat actors – also belongs to a family of botnets |
| New Ransomware Victims Last Week: | 83 | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Red Piranha proactively gathers information about organisations impacted by ransomware attacks through various channels, including the Dark Web. In the past week, our team identified a total of 83 new ransomware victims from 19 distinct industries across 28 countries worldwide. This highlights the global reach and indiscriminate nature of ransomware attacks, which can affect organisations of all sizes and sectors. LockBit 3.0, a specific ransomware, has affected the largest number of new victims (24) spread across various countries. Ransomware blog and Royal groups follow closely with each hitting 21 and 06 new victims respectively. Below are the victim counts (%) for these ransomware groups and a few others. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Name of Ransomware Group | Percentage of new Victims last week | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Abyss-data | 1.20% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Alphv | 4.82% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Blackbyte | 3.61% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Crosslock | 1.20% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Cryptnet | 2.41% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Dunghill | 2.41% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Everest | 1.20% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Karakurt | 2.41% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Lockbit3 | 28.92% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Medusa | 2.41% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Play | 6.02% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Ransomware blog | 25.30% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Royal | 7.23% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Trigona | 7.23% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Unsafe | 1.20% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Vicesociety | 2.41% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
