| New Threat Detection Added | 3 (WarzoneRAT, Xehook Stealer and Lumma Stealer) |
| New Threat Protections | 55 |
Weekly Detected Threats
The following threats were added to Crystal Eye XDR this week:
|
Threat name:
|
WarzoneRAT | ||||||||||||||||||||||||
|
In February, the FBI shut down the WarzoneRAT malware operation and arrested two people involved. Recently, researchers found malware spread via tax-themed spam emails, using WarzoneRAT as the final attack. One method involves an attachment with a LNK file that triggers a chain of downloads leading to malicious activity. Another method uses an executable file to load the WarzoneRAT DLL module. Once activated, WarzoneRAT connects to a Command-and-Control server to carry out harmful actions on the victim's computer.
|
|||||||||||||||||||||||||
|
Threat Protected:
|
01 | ||||||||||||||||||||||||
|
Rule Set Type:
|
|
||||||||||||||||||||||||
|
Class Type:
|
Trojan-activity | ||||||||||||||||||||||||
|
Kill Chain:
|
|
||||||||||||||||||||||||
|
Threat name:
|
Xehook Stealer | |||||||||||||||||||||
|
Discovered in January 2024, Xehook Stealer is a malware designed for Windows computers using .NET. It can collect data from Chromium and Gecko browsers, supporting over 110 cryptocurrencies and 2FA extensions. The Stealer also has tools for creating custom traffic bots and recovering Google cookies. Its evolution traces back to the free MaaS Cinoshi Project, leading to Agniane Stealer and finally, Xehook Stealer, possibly indicating rebranding and improvements. Xehook Stealer spreads mainly through SmokeLoader binaries, showing active distribution efforts. It shares code similarities with Agniane Stealer and communicates with the same control server, suggesting a close connection. Similar web panel designs across Cinoshi, Agniane, and Xehook Stealer indicate ongoing development.
|
||||||||||||||||||||||
|
Threat Protected:
|
01 | |||||||||||||||||||||
|
Rule Set Type:
|
|
|||||||||||||||||||||
|
Class Type:
|
Trojan-activity | |||||||||||||||||||||
|
Kill Chain:
|
|
|||||||||||||||||||||
|
Threat name:
|
Lumma Stealer | ||||||||||||||||||
|
Lumma is a piece of malicious software categorised as a stealer. Malware within this category is designed to steal sensitive data. These programs are capable of exfiltrating data from infected systems and the applications installed onto them. Lumma's behaviour is like that of the Mars, Arkei, and Vidar stealers. Stealer-type malware can exfiltrate both device/system and personal data. The latter entails downloading various files (e.g., databases, images, documents, videos, etc.) from the compromised system. Typically, these malicious programs can extract information from browsers, which could include browsing and search engine data, autofills, usernames/passwords, personally identifiable details, credit card numbers, and so forth. Stealers often target various accounts like emails, social media, social networking, messengers, gaming-related software, online banking, e-commerce, cryptocurrency wallets, FTPs, password managers, authentication software, VPNs, and many others.
|
|||||||||||||||||||
|
Threat Protected:
|
10 | ||||||||||||||||||
|
Rule Set Type:
|
|
||||||||||||||||||
|
Class Type:
|
Trojan-activity | ||||||||||||||||||
|
Kill Chain:
|
|
||||||||||||||||||
Known exploited vulnerabilities (Week 1 - April 2024)
|
Threat
|
CVSS
|
Description | |
|
CVE-2024-29748
|
On-going analysis
|
Android Pixel Privilege Escalation Vulnerability
|
|
|
CVE-2024-29745
|
On-going analysis
|
Android Pixel Information Disclosure Vulnerability
|
Updated Malware Signatures (Week 1 - April 2024)
|
Threat
|
Description
|
|
|
Cerber
|
Another type of ransomware but instead of the usual ransom text files, it plays audio on the victim’s infected machine.
|
|
|
Remcos
|
Remcos functions as a remote access trojan (RAT), granting unauthorised individuals the ability to issue commands on the compromised host, record keystrokes, engage with the host's webcam, and take snapshots. Typically, this malicious software is distributed through Microsoft Office documents containing macros, which are often attached to malicious emails.
|
|
|
Gh0stRAT
|
Gh0stRAT is a widely recognised group of remote access trojans strategically crafted to grant an assailant full authority over a compromised system. Its functionalities encompass monitoring keystrokes, capturing video via the webcam, and deploying subsequent malware. The source code of Gh0stRAT has been openly accessible on the internet for an extended period, substantially reducing the hurdle for malicious actors to adapt and employ the code in fresh attack endeavours.
|
|
|
MacStealer
|
A remote access trojan enables its operator to take control of a victim machine and steal data. It is usually distributed through spam and phishing emails.
|
| Ransomware Report | |
|
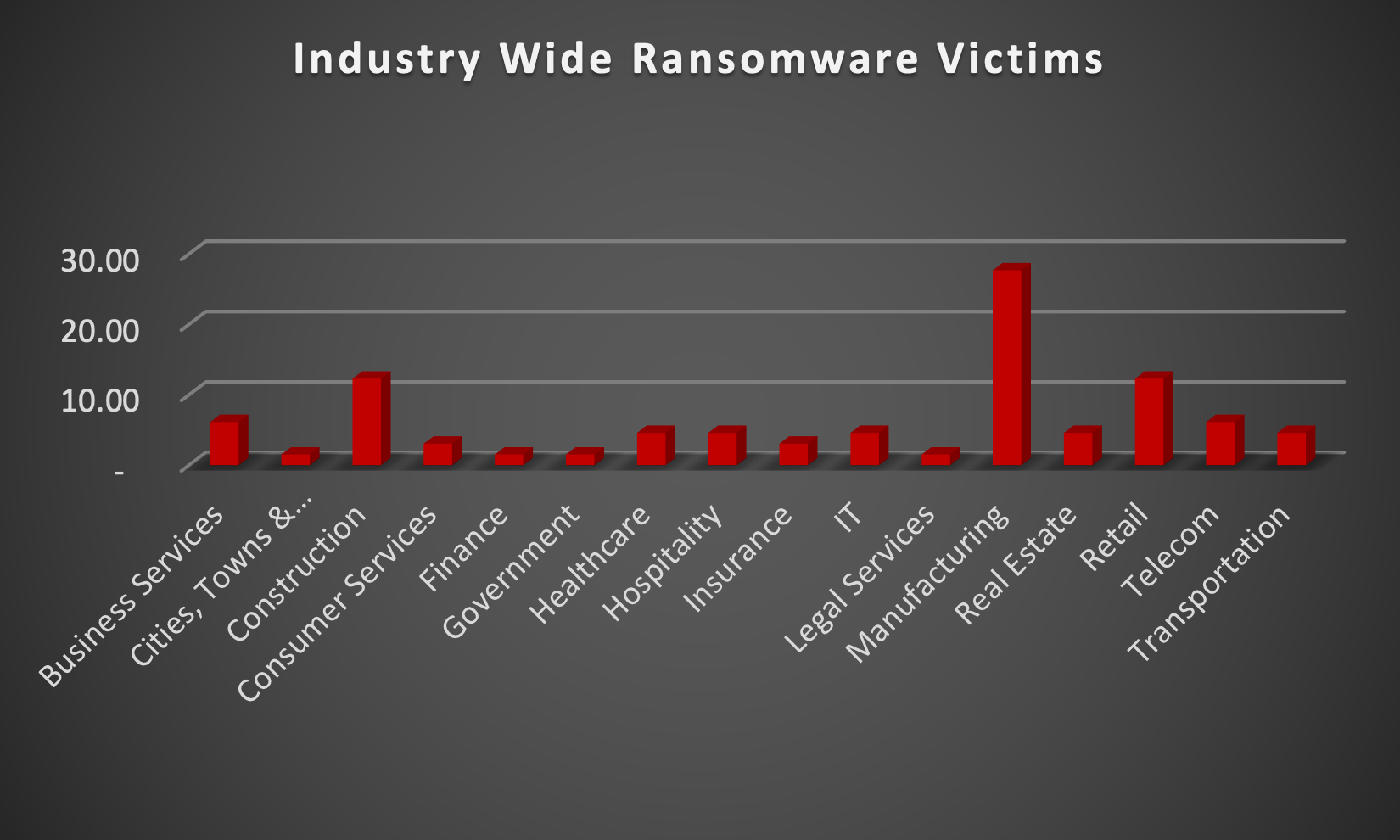
The Red Piranha Team actively collects information on organisations globally affected by ransomware attacks from various sources, including the Dark Web. In the past week alone, our team uncovered new ransomware victims and updates on previous victims across 16 different industries spanning 18 countries. This underscores the widespread and indiscriminate impact of ransomware attacks, emphasising their potential to affect organisations of varying sizes and sectors worldwide. Hunters International ransomware group stands out as the most prolific, having updated a significant number of victims (13%) each distributed across multiple countries. In comparison, Cactus and INC Ransom ransomware groups updated 10% of victims each, in the past week. The following list provides the victim counts in percentages for these ransomware groups and a selection of others. |
|
| Name of Ransomware Group | Percentage of new Victims last week |
|
8Base
|
7.69%
|
|
Akira
|
4.62%
|
|
Bianlian
|
1.54%
|
|
Black Suit
|
6.15%
|
|
Blackbasta
|
4.62%
|
|
Cactus
|
10.77%
|
|
Ciphbit
|
1.54%
|
|
Everest
|
3.08%
|
|
Hunters
|
13.85%
|
|
INC Ransom
|
10.77%
|
|
Killsec
|
1.54%
|
|
Lockbit3
|
6.15%
|
|
Malek Team
|
1.54%
|
|
Play
|
6.15%
|
|
Qilin
|
6.15%
|
|
RA Group
|
6.15%
|
|
Ransomhub
|
4.62%
|
|
Rhysida
|
1.54%
|
|
Trigona
|
1.54%
|
Hunters International Ransomware GroupHunters International, a Ransomware-as-a-Service (RaaS) entity, surfaced in Q3 of 2023, showing resemblances to the notorious Hive ransomware strain. The analysis revealed a significant overlap of approximately 60% between Hunters International and Hive ransomware version 61. This suggests a potential connection to the disrupted Hive cartel. Despite reports linking them, Hunters International has denied any affiliation with Hive.
Hunters International primarily targets Windows and Linux environments. Here's a breakdown of their attack methods: Data Exfiltration: Similar to its predecessor, Hunters International prioritises exfiltrating sensitive data before encryption. This stolen information becomes leverage for double extortion tactics. Encryption: The ransomware encrypts the victim's data, hindering access and demanding a ransom payment for decryption. The specific encryption algorithm used by Hunters is not definitively known in publicly available reports. Victim Targeting: Hunters International appears to target a broad range of industries, including healthcare, as evidenced by an attack on a plastic surgery clinic where patient data was stolen. Intelligence indicates that Hunters International primarily aims to exfiltrate data and extort victims with ransom demands. Notably, they targeted a US plastic surgery clinic, compromising data of around 248,000 files, including patient information. The ransomware appends ".LOCKED" to encrypted files and leaves "Contact Us.txt" instructions for victims to initiate negotiations on the dark web. Although the goal is to encrypt files, it will skip the following: Files in folders with these substrings in their names: $Recycle bin, $windows.~bt, $windows.~ws, all users, appdata, boot, config.msi, default, Google, Intel, Mozilla, MSOcache, perflogs, system volume information, tor browser, internet explorer, windows, windows.old, windows nt. Files named: autorun.inf, bootfont.bin, boot.ini, bootsect.bak, desktop.ini, iconcache.db, ntldr, ntuser.dat, ntuser.dat.log, ntuser.ini.log, thumbs.db Files with the following extensions: 386, adv, ani, bat, bin, cab, cmd, com, cpl, cur, deskthemepack, diagcab, diagcfg, diagpkg, dll, drv, exe, hlp, hta, icl, icns, ico, ics, idx, key, ldf, lnk, lock, mod, mpa, msc, msi, msp, msstyles, msu, nls, nomedia, ocx, pdb, prf, ps1, rom, rtp, scr, shs, spl, sys, theme, themepack, wpx Figure 3: Ransom Note of the Hunters International Ransomware Hunters International remains a relatively new threat actor, but their connection to Hive and their aggressive tactics warrant close attention. By prioritising data security, staying informed about evolving threats, and implementing strong cybersecurity measures, organisations can minimise the risk of falling victim to Hunters International. Kill Chain:
Indicators of Compromise (IOCs)
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
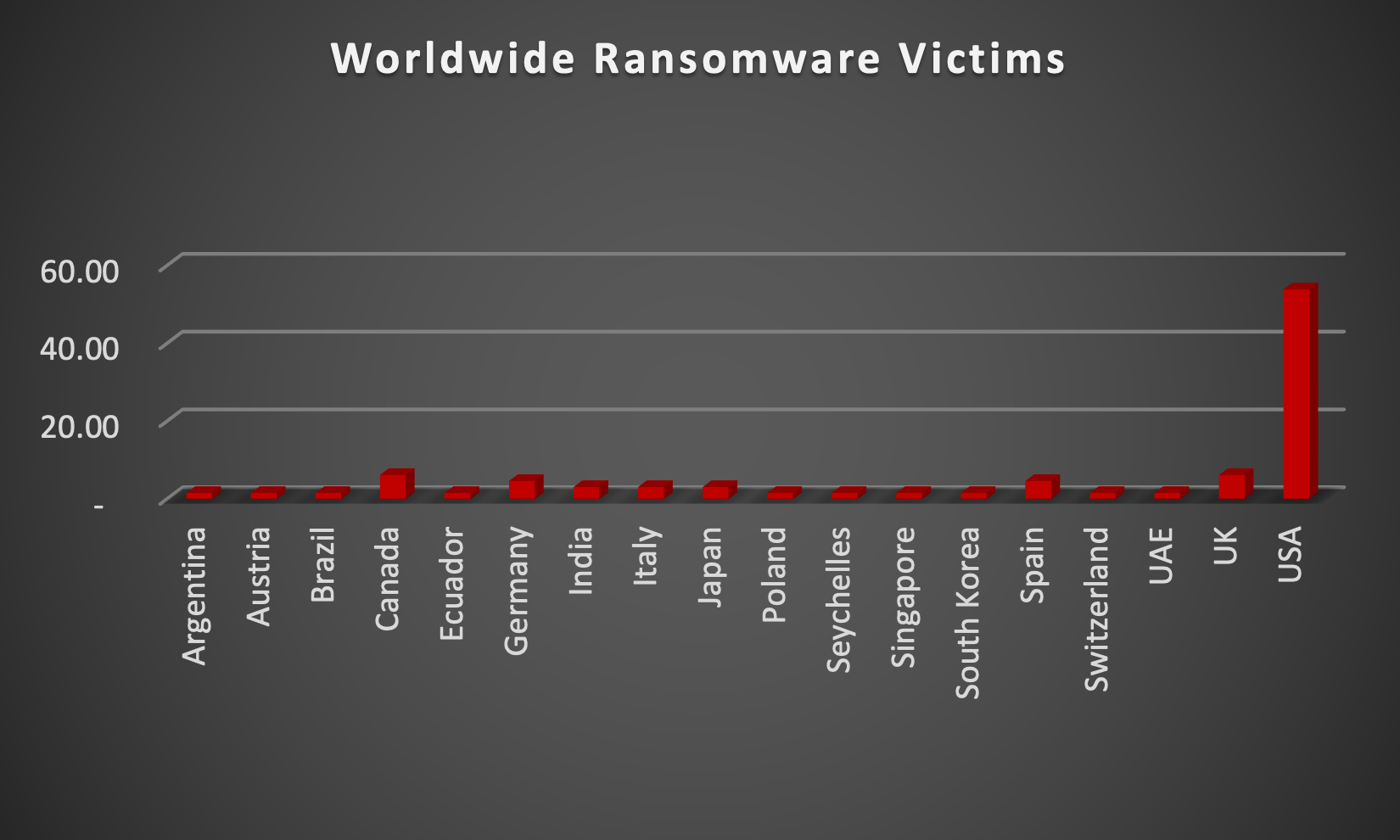
Upon further investigation, it has been identified that ransomware has left its mark on 16 different industries worldwide. Notably, the Manufacturing industry bore the brunt of the attacks in the past week, accounting for 27% of victims. The table below delineates the most recent ransomware victims, organised by industry, shedding light on the sectors grappling with the significant impact of these cyber threats. |