| New Threat Detection Added | 3 (RomCom RAT, Erbium Stealer and Parallax RAT) |
| New Threat Protections | 79 |
Weekly Detected Threats
The following threats were added to Crystal Eye XDR this week:
|
Threat name:
|
RomCom RAT | ||||||||||||||||||
|
Storm-0978, also known as RomCom, is a cybercriminal group from Russia. They use sneaky tactics like ransomware and extortion to make money. They also steal login details for spying. Storm-0978 creates and spreads a sneaky program called RomCom. They also use a ransomware called Underground, linked to another called Industrial Spy. They recently used a computer bug called CVE-2023-36884 to sneak RomCom onto computers. Storm-0978 tricks people by hiding their bad software in popular good ones. They often target government and military groups in Ukraine, plus other organisations in Europe and North America, especially those connected to Ukraine. They have hit telecom and finance companies.
|
|||||||||||||||||||
|
Threat Protected:
|
04 | ||||||||||||||||||
|
Rule Set Type:
|
|
||||||||||||||||||
|
Class Type:
|
Trojan-activity | ||||||||||||||||||
|
Kill Chain:
|
|
||||||||||||||||||
|
Threat name:
|
Erbium Stealer | |||||||||||||||||||||
|
Erbium is a new type of malicious software that is becoming popular among cybercriminals. It is like a service - people pay to use it. Erbium steals information from computers and is getting attention because it does various things, has good customer service, and is cheap. It was first talked about in July 2022, but it is not clear if it is being used yet. At first, it cost $9 a week, but now it is $100 a month or $1000 a year. Compared to another similar program called RedLine, Erbium is cheaper. It steals passwords, credit card details, and cryptocurrency info from web browsers.
|
||||||||||||||||||||||
|
Threat Protected:
|
03 | |||||||||||||||||||||
|
Rule Set Type:
|
|
|||||||||||||||||||||
|
Class Type:
|
Trojan-activity | |||||||||||||||||||||
|
Kill Chain:
|
|
|||||||||||||||||||||
|
Threat name:
|
Parallax RAT | |||||||||||||||||||||
|
Parallax RAT infiltrated systems through a drive-by download disguised as a Fortinet VPN client distributed via popular search engines. The threat actor behind it utilised PsExec for lateral movement from the initial infection point to the Domain Controller within a tight 2-hour window. The RAT ensured persistence by integrating itself into the Startup folder and renaming its executable. It also deployed NetSupportRAT on the Domain Controller. Offering various functionalities like remote control, data exfiltration, keylogging, and more, Parallax RAT's
cracked version persists despite the project's closure, utilising evasion tactics like anti-disassembly measures and RC4 encryption for configuration concealment.
|
||||||||||||||||||||||
|
Threat Protected:
|
01 | |||||||||||||||||||||
|
Rule Set Type:
|
|
|||||||||||||||||||||
|
Class Type:
|
Trojan-activity | |||||||||||||||||||||
|
Kill Chain:
|
|
|||||||||||||||||||||
Known exploited vulnerabilities (Week 2 - April 2024)
|
Threat
|
CVSS
|
Description | |
|
CVE-2024-3272
|
9.8 (Critical)
|
D-Link Multiple NAS Devices Use of Hard-Coded Credentials Vulnerability
|
|
|
CVE-2024-3273
|
9.8 (Critical)
|
D-Link Multiple NAS Devices Command Injection Vulnerability
|
|
|
CVE-2024-3400
|
10.0 (Critical)
|
Palo Alto Networks PAN-OS Command Injection Vulnerability
|
Updated Malware Signatures (Week 2 - April 2024)
|
Threat
|
Description
|
|
|
Cerber
|
Another type of ransomware, but instead of the usual ransom text files, it plays audio on the victim’s infected machine.
|
|
|
Remcos
|
Remcos functions as a remote access trojan (RAT), granting unauthorised individuals the ability to issue commands on the compromised host, record keystrokes, engage with the host's webcam, and take snapshots. Typically, this malicious software is distributed through Microsoft Office documents containing macros, which are often attached to malicious emails.
|
|
|
Gh0stRAT
|
Gh0stRAT is a widely recognised group of remote access trojans strategically crafted to grant an assailant full authority over a compromised system. Its functionalities encompass monitoring keystrokes, capturing video via the webcam, and deploying subsequent malware. The source code of Gh0stRAT has been openly accessible on the internet for an extended period, substantially reducing the hurdle for malicious actors to adapt and employ the code in fresh attack endeavours.
|
|
|
MacStealer
|
A remote access trojan enables its operator to take control of a victim machine and steal data. It is usually distributed through spam and phishing emails.
|
| Ransomware Report | |
|
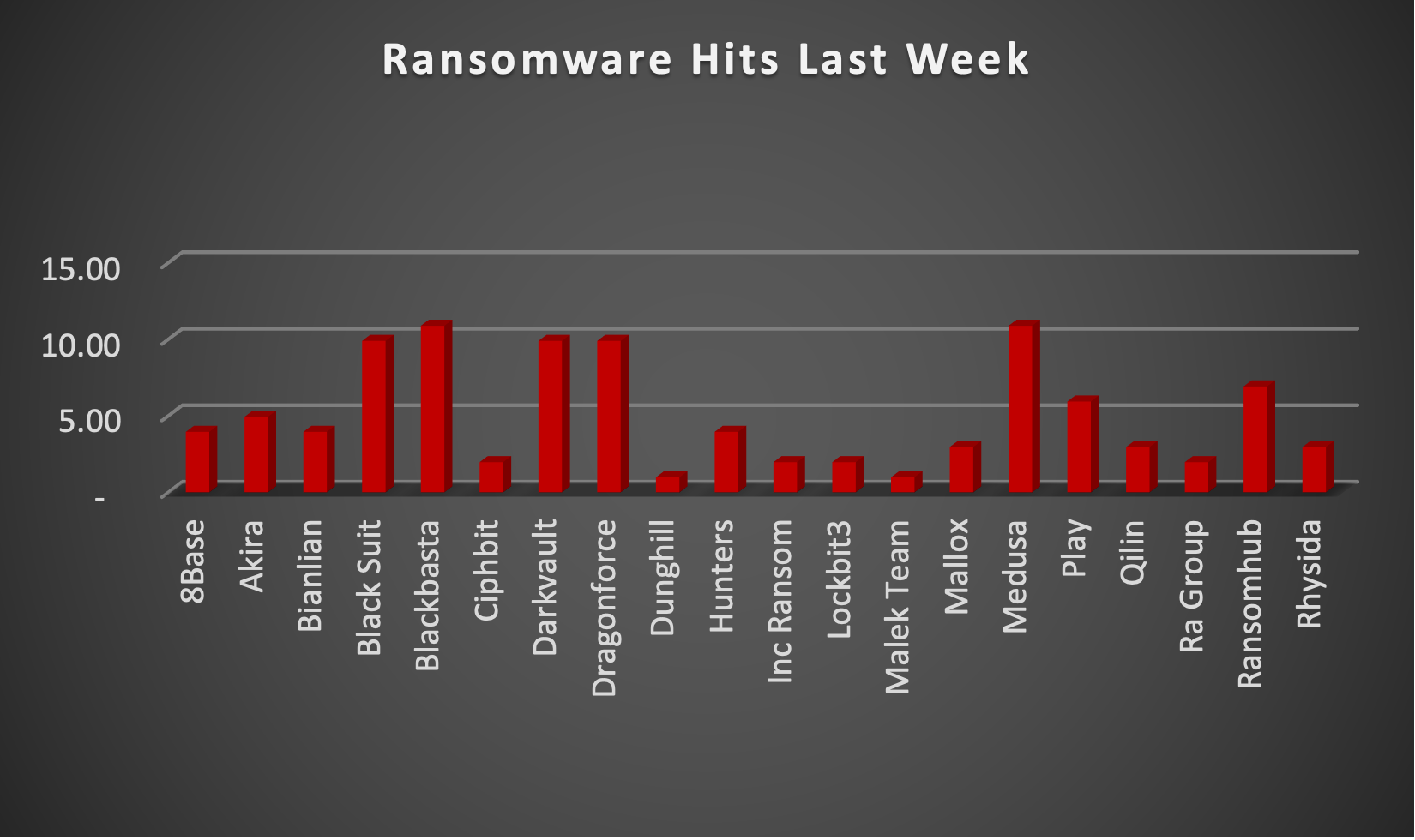
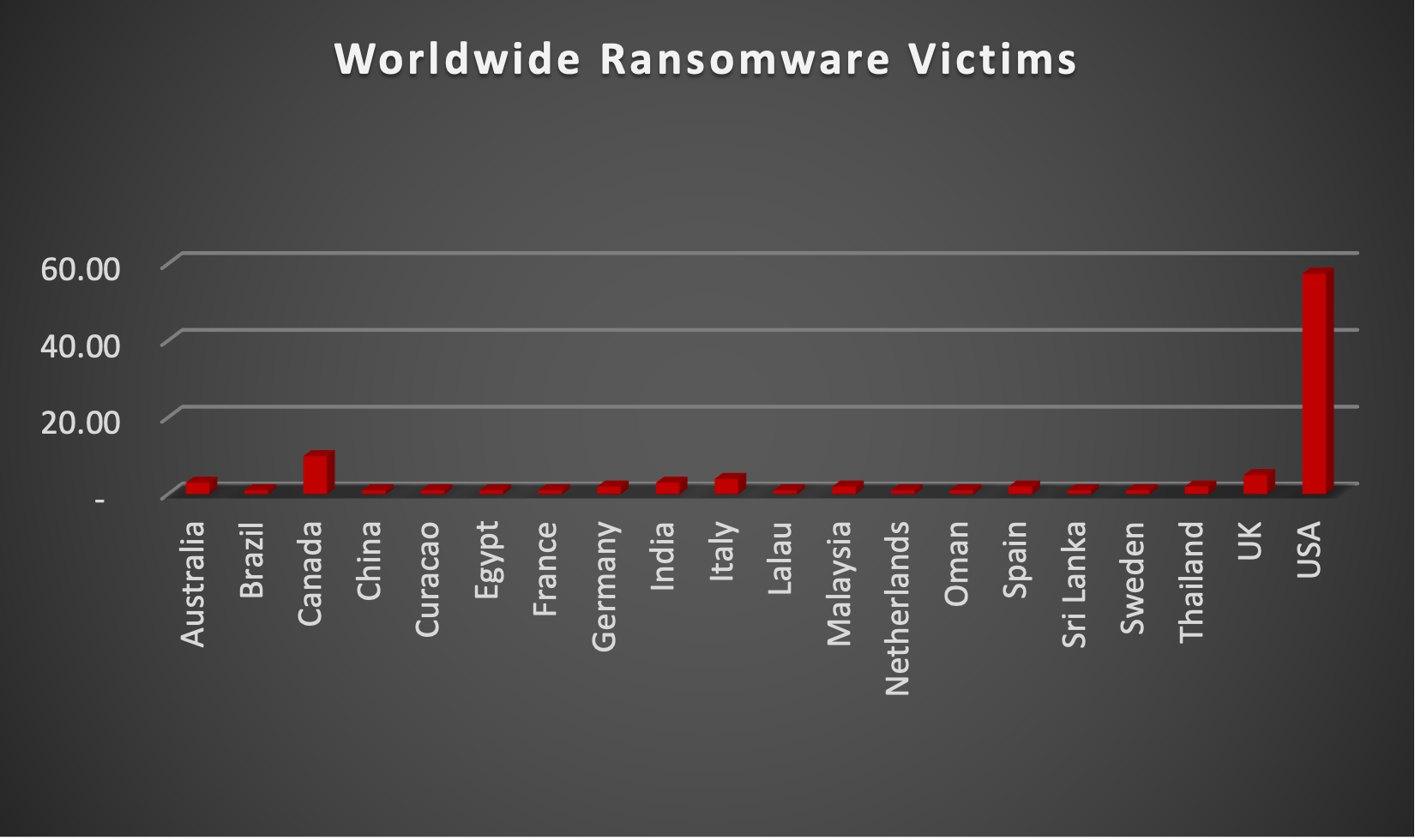
The Red Piranha Team actively collects information on organisations globally affected by ransomware attacks from various sources, including the Dark Web. In the past week alone, our team uncovered new ransomware victims and updates on previous victims across 21 different industries spanning 20 countries. This underscores the widespread and indiscriminate impact of ransomware attacks, emphasising their potential to affect organisations of varying sizes and sectors worldwide. BlackBasta and Medusa ransomware groups stand out as the most prolific, having updated a significant number of victims (10%) each distributed across multiple countries. In comparison, Black Suit, Darkvault and Dragonforce ransomware groups updated 9% of victims each, in the past week. The following list provides the victim counts in percentages for these ransomware groups and a selection of others. |
|
| Name of Ransomware Group | Percentage of new Victims last week |
|
8Base
|
3.96%
|
|
Akira
|
4.95%
|
|
Bianlian
|
3.96%
|
|
Black Suit
|
9.90%
|
|
BlackBasta
|
10.89%
|
|
Ciphbit
|
1.98%
|
|
Darkvault
|
9.90%
|
|
Dragonforce
|
9.90%
|
|
Dunghill
|
0.99%
|
|
Hunters
|
3.96%
|
|
Inc Ransom
|
1.98%
|
|
Lockbit3
|
1.98%
|
|
Malek Team
|
0.99%
|
|
Mallox
|
2.97%
|
|
Medusa
|
10.89%
|
|
Play
|
5.94%
|
|
Qilin
|
2.97%
|
|
Ra Group
|
1.98%
|
|
Ransomhub
|
6.93%
|
|
Rhysida
|
2.97%
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
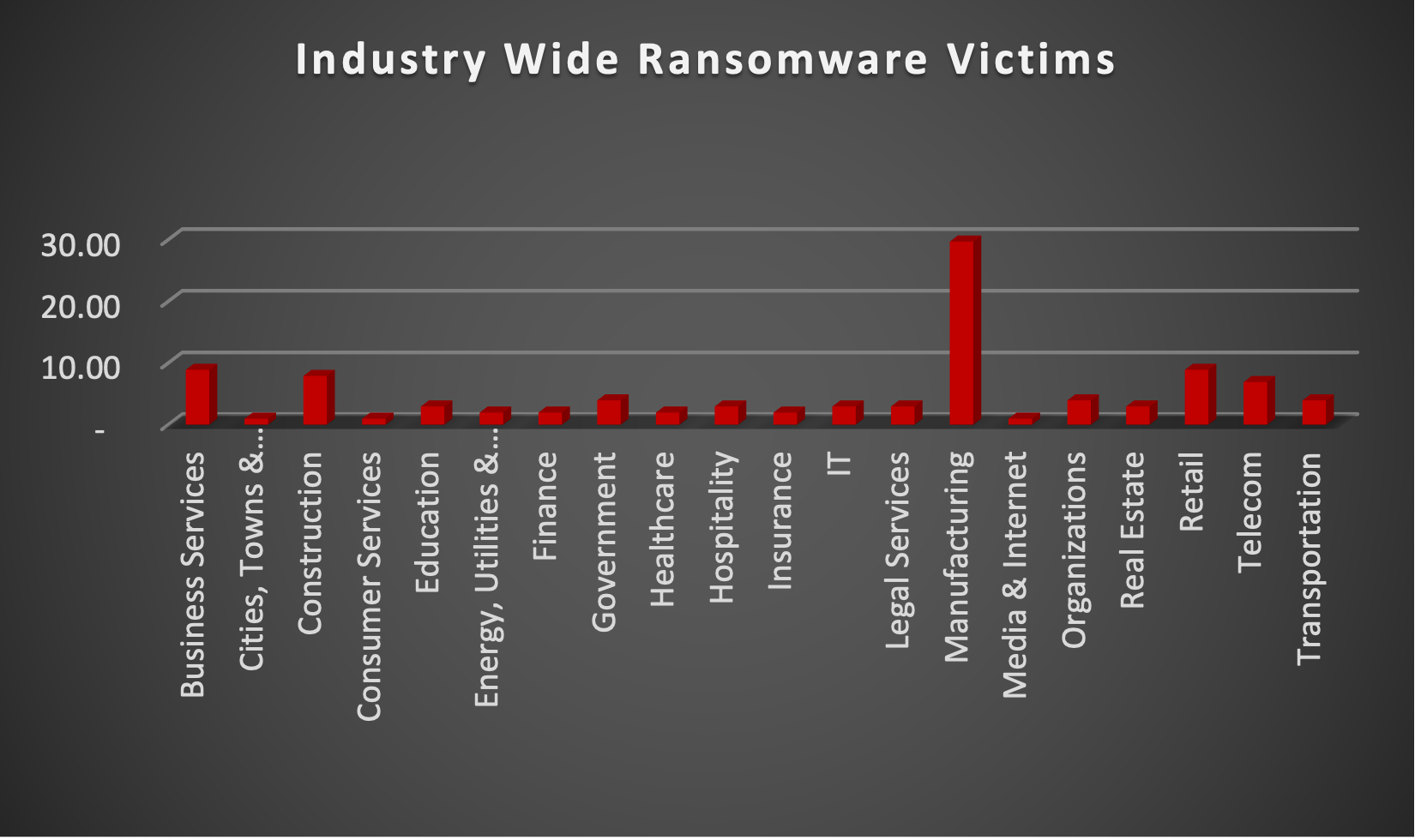
Upon further investigation, it has been identified that ransomware has left its mark on 21 different industries worldwide. Notably, the Manufacturing bore the brunt of the attacks in the past week, accounting for 29% of victims. The table below delineates the most recent ransomware victims, organised by industry, shedding light on the sectors grappling with the significant impact of these cyber threats.
|
Name of the affected Industry
|
Victims Count (%)
|
|
Business Services
|
8.91%
|
|
Cities, Towns & Municipalities
|
0.99%
|
|
Construction
|
7.92%
|
|
Consumer Services
|
0.99%
|
|
Education
|
2.97 %
|
|
Energy, Utilities & Waste Treatment
|
1.98%
|
|
Finance
|
1.98%
|
|
Government
|
3.96%
|
|
Healthcare
|
1.98%
|
|
Hospitality
|
2.97%
|
|
Insurance
|
1.98%
|
|
IT
|
2.97%
|
|
Legal Services
|
2.97%
|
|
Manufacturing
|
29.70 %
|
|
Media & Internet
|
0.99 %
|
|
Organisations
|
3.96%
|
|
Real Estate
|
2.97%
|
|
Retail
|
8.91%
|
|
Telecom
|
6.93%
|