Trends
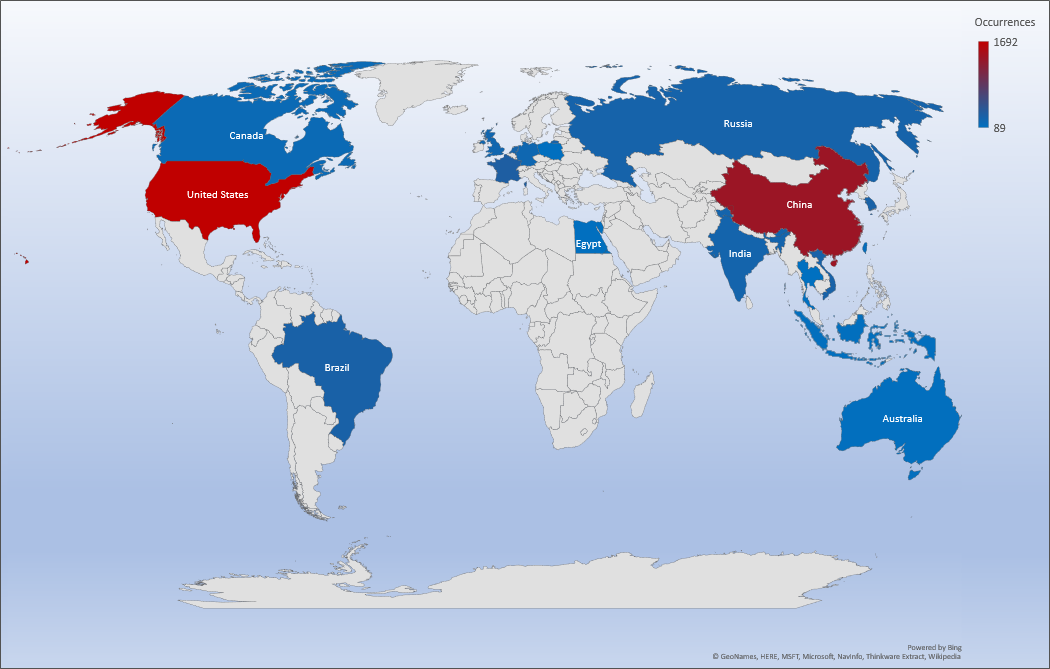
- The top attacker country was United States with 1692 unique attackers (24%).
- The top Exploit event was Shellcode with 61% of occurrences.
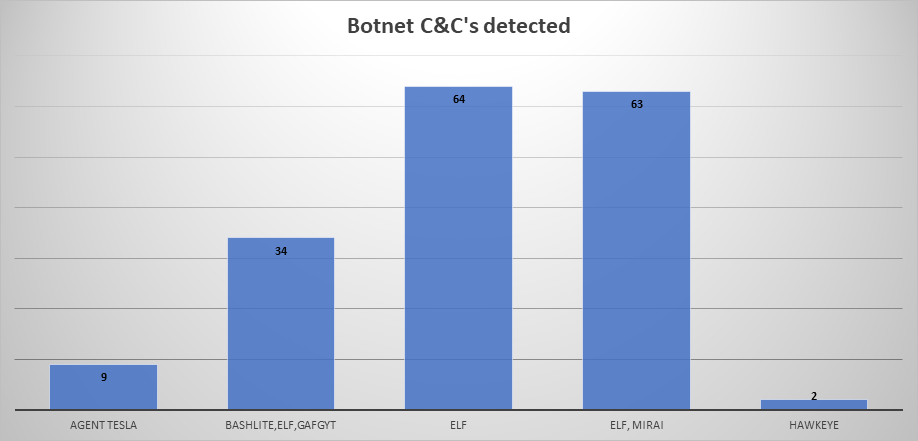
- The top Trojan C&C server detected was Elf with 64 instances detected.
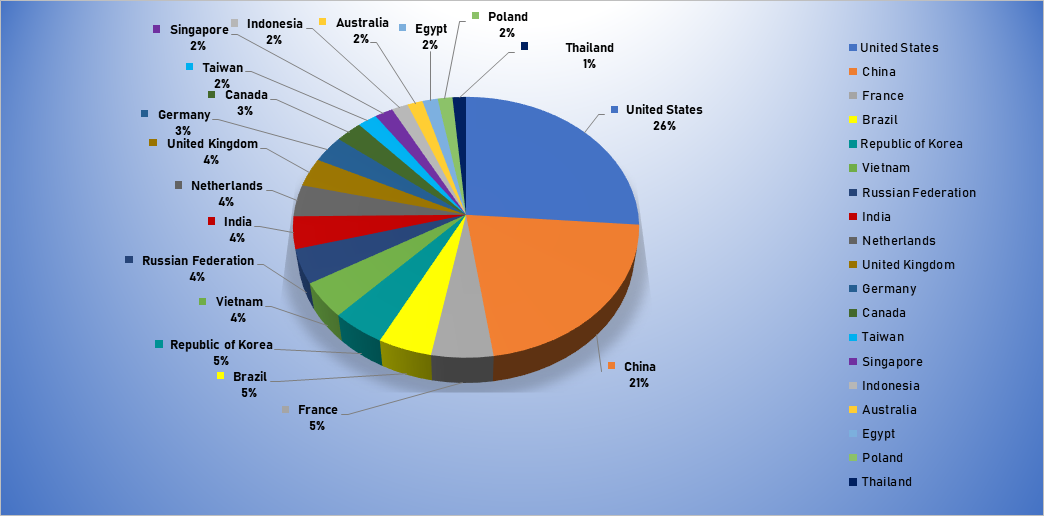
Top Attacker by Country
| Country | Occurrences | Percentage |
|---|---|---|
| United States | 1692 | 26.21% |
| China | 1386 | 21.47% |
| France | 340 | 5.27% |
| Brazil | 298 | 4.62% |
| Republic of Korea | 294 | 4.55% |
| Vietnam | 287 | 4.45% |
| Russian Federation | 274 | 4.24% |
| India | 259 | 4.01% |
| Netherlands | 254 | 3.93% |
| United Kingdom | 229 | 3.55% |
| Germany | 217 | 3.36% |
| Canada | 178 | 2.76% |
| Taiwan | 129 | 2.00% |
| Singapore | 121 | 1.87% |
| Indonesia | 108 | 1.67% |
| Australia | 102 | 1.58% |
| Egypt | 101 | 1.56% |
| Poland | 98 | 1.52% |
| Thailand | 89 | 1.38% |
Threat Geo-location
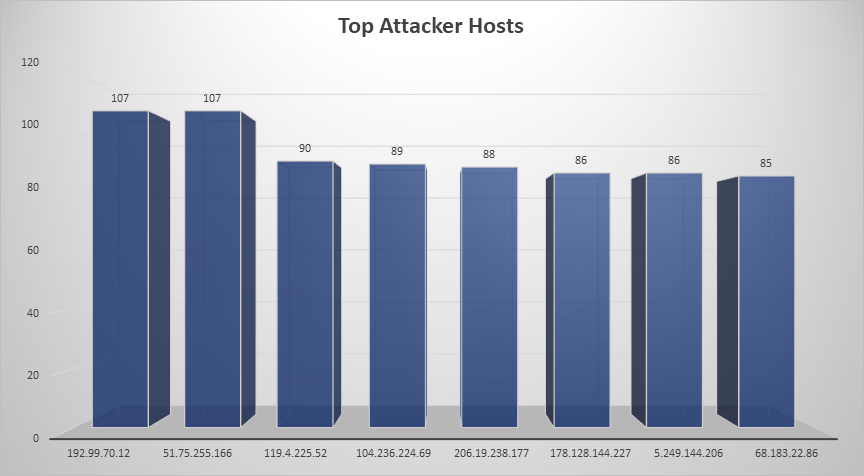
Top Attacking Hosts
| Host | Occurrences |
|---|---|
| 192.99.70.12 | 107 |
| 51.75.255.166 | 103 |
| 119.4.225.52 | 90 |
| 104.236.224.69 | 84 |
| 206.19.238.177 | 78 |
| 178.128.144.227 | 75 |
| 5.249.144.206 | 56 |
| 68.183.22.86 | 24 |
Top Network Attackers
| Origin AS | Announcement | Description |
|---|---|---|
| AS16276 | 192.99.0.0/16 | OVH Hosting Inc. |
| AS4837 | 119.4.0.0/14 | China Unicom SiChuan province network |
| AS7018 | 206.16.0.0/14 | CERFnet |
| AS31034 | 5.249.144.0/21 | Aruba S.p.A. - Cloud Services Farm2 |
Top Event NIDS and Exploits
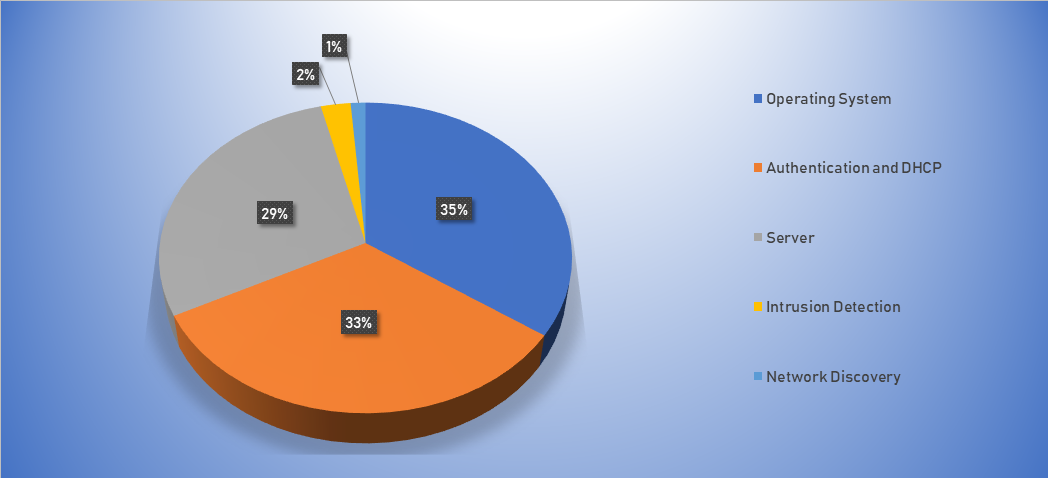
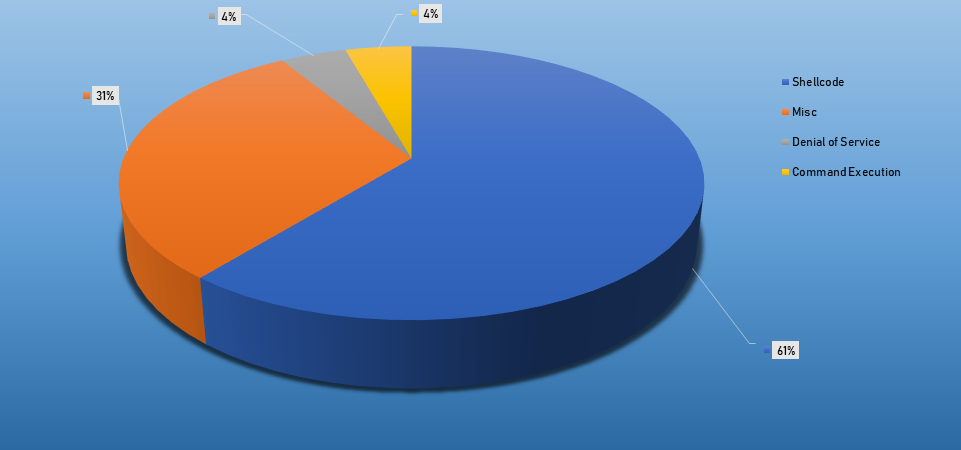
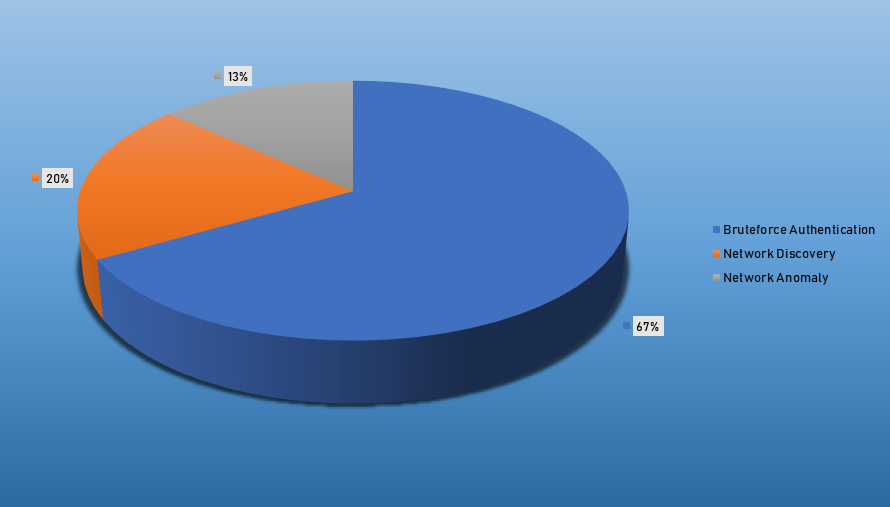
Top Alarms
| Type of Alarm | Occurrences |
|---|---|
| Bruteforce Authentication | 30 |
| Network Discovery | 9 |
| Network Anomaly | 6 |
Comparison from last week
| Type of Alarm | Occurrences |
|---|---|
| Bruteforce Authentication | 2637 |
| Network Discovery | 14 |
| Network Anomaly | 2 |
Remote Access Trojan C&C Servers Found
| Name | Number Discovered | Location |
|---|---|---|
| Agent Tesla | 9 | 149.202.110.2 |
| bashlite,elf,gafgyt | 34 | 185.224.131.155 51.77.95.123 192.236.208.231 192.236.208.28 |
| elf | 64 | 192.236.208.231 185.22.154.189 185.52.1.235 198.167.143.202 51.91.174.30 79.159.202.162 91.234.99.177 151.80.209.229 45.80.37.4 5.182.210.141 110.47.230.127 91.98.229.33 185.224.131.155 91.234.99.177 |
| elf, mirai | 63 | 122.165.186.126 31.13.195.49 185.22.154.189 198.167.143.202 164.68.115.67 51.91.174.30 142.11.240.29 151.80.209.229 5.182.210.141 89.35.39.74 185.164.72.155 |
| Hawkeye | 2 | 13.67.107.73 13.75.76.78 |
Common Malware
| Malware Type | MD5 | Typical Filename |
|---|---|---|
| Win.Trojan. Generic | 47b97de62 ae8b2b927 542aa5d7f3 c858 | qmreport upload.exe |
PUA.Osx. | 125ef5dc3 | helpermcp |
W32.Agent | e2ea315d9 | Tempmf |
W32.Generic: | 799b30f47 | mf201634 1595.exe |
| W32.7ACF 71AFA8-95.SBX.TG | 4a50780d | xme64-2 141.exe |
CVE
This is a list of recent vulnerabilities for which exploits are available.
ID: CVE-2019-1125
Title: Microsoft Windows Kernel Information Disclosure Vulnerability
Vendor: Microsoft
Description: An information disclosure vulnerability exists when certain central processing units speculatively access memory. An attacker who successfully exploited the vulnerability could read privileged data across trust boundaries. To exploit this vulnerability, an attacker would have to log on to an affected system and run a specially crafted application. The vulnerability would not allow an attacker to elevate user rights directly, but it could be used to obtain information that could be used to try to compromise the affected system further.
CVSS v2 Base Score: 4.0
ID: CVE-2019-11247
Title: Kubernetes Incomplete Fix Arbitrary File Overwrite Vulnerability
Vendor: Kubernetes
Description: A vulnerability exists in the K8s API that could allow users to read, modify or delete cluster-wide custom resources, even if they only have RBAC permissions for namespaced resources. This vulnerability allows access to a cluster-scoped custom resource if the request is made as if the resource were namespaced. Authorizations for the resource accessed in this manner are enforced using roles and role bindings within the namespace, meaning that a user with access only to a resource in one namespace could create, view update or delete the cluster-scoped resource (according to their namespace role privileges).
CVSS v2 Base Score: 5.1
ID: CVE-2019-13377
Title: WPA3 Timing Based Side Channel Vulnerability
Vendor: WPA3
Description: New Side-Channel Attack against WPA3 exists when using brainpool curves. The first vulnerability is a timing-based side-channel attack against WPA3's Dragonfly handshake when using Brainpool curves, which the WiFi Alliance recommended vendors to use as one of the security recommendations to add another layer of security. The new side-channel leak is located in the password encoding algorithm of Dragonfly.
CVSS v2 Base Score: 5.4
ID: CVE-2019-14234
Title: Django JSONField SQL injection Vulnerability
Vendor: Django
Description: Key and index lookups for django.contrib.postgres.fields.JSONField and key lookups for django.contrib.postgres.fields.HStoreField were subject to SQL injection, using a suitably crafted dictionary, with dictionary expansion, as the **kwargs passed to QuerySet.filter().
CVSS v2 Base Score: 5.0
ID: CVE-2019-13143
Title: FB50 Smart Lock Information Disclosure Vulnerability
Vendor: Shenzhen Dragon Brother Technology
Description: An HTTP parameter pollution issue was discovered on Shenzhen Dragon Brothers Fingerprint Bluetooth Round Padlock FB50 2.3. With the user ID, user name, and the lock's MAC address, anyone can unbind the existing owner of the lock, and bind themselves instead. This leads to complete takeover of the lock. The user ID, name, and MAC address are trivially obtained from APIs found within the Android or iOS application. With only the MAC address of the lock, any attacker can transfer ownership of the lock from the current user, over to the attacker's account. Thus rendering the lock completely inaccessible to the current user.
CVSS v2 Base Score: 4.0
ID: CVE-2019-14697
Title: musl libc x87 Stack Overflow Vulnerability
Vendor: musl libc
Description: musl libc has an x87 floating-point stack adjustment imbalance, related to the math/i386/ directory. In some cases, use of this library could introduce out-of-bounds writes that are not present in an application's source code. This can lead to x87 stack overflow in the execution of subsequent math code, causing it to incorrectly produce a NAN in place of the actual result.
CVSS v2 Base Score: 3.6
ID: CVE-2019-14286
Title: Misp Cross Site Scripting Vulnerability
Vendor: Misp
Description: In app/webroot/js/event-graph.js in MISP, a stored XSS vulnerability exists in the event-graph view when a user toggles the event graph view. A malicious MISP event must be crafted in order to trigger the vulnerability.
CVSS v2 Base Score: 4.3
ID: CVE-2019-14654
Title: Joomla Remote code Execution Vulnerability
Vendor: Joomla
Description: In Joomla!, inadequate filtering allows users authorised to create custom fields to manipulate the filtering options and inject an unvalidated option.In other words, the filter attribute in subform fields allows remote code execution.
CVSS v2 Base Score: 5.0
Vulnerabilities
Jenkins Credentials Binding Plugin CVE-2019-1010241 Information Disclosure Vulnerability
2019-07-26
securityfocus.com/bid/109320
Qualcomm Components CVE-2019-2307 Integer Underflow Vulnerability
2019-07-26
securityfocus.com/bid/109383
LibreOffice Remote Code Execution and Unauthorized Access Vulnerabilities
2019-07-26
securityfocus.com/bid/109374
KDE KAuth CVE-2017-8422 Local Privilege Escalation Vulnerability
2019-07-25
securityfocus.com/bid/98412
FreeBSD CVE-2019-5604 Out of Bounds Read Denial of Service Vulnerability
2019-07-25
securityfocus.com/bid/109369
Exim CVE-2019-13917 Privilege Escalation Vulnerability
2019-07-24
securityfocus.com/bid/109338
Libdwarf CVE-2019-14249 Remote Denial Of Service Vulnerability
2019-07-24
securityfocus.com/bid/109380
McAfee Data Loss Prevention Endpoint for Windows Multiple Local Security Vulnerabilities
2019-07-24
securityfocus.com/bid/109377
