| New Threat Detection Added | 2 - New Mirai Variant and LandUpdate808 Fake Update Variant |
| New Threat Protections | 163 |
Weekly Detected Threats
The following threats were added to Crystal Eye XDR this week:
Threat name: | New Mirai Variant | ||||||||||||||||||
A recent analysis has identified a new variant of the Mirai botnet, known for targeting IoT/Linux devices across various architectures, including ARM, MIPS, and x86. This variant, referred to as Mirai.CatDDoS or GorillaBot, is operated by the CatDDoS group and incorporates the TEA algorithm for encryption, deviating from the original Mirai's XOR-based string decryption. Notably, it lacks the Telnet brute force scanning module present in the original Mirai, focusing instead on enhanced DDoS attack capabilities. The malware communicates with its command-and-control (C2) servers using hardcoded OpenNIC DNS servers and employs a broader range of attack vectors compared to its predecessor. | |||||||||||||||||||
Threat Protected: | 2 | ||||||||||||||||||
Rule Set Type: |
| ||||||||||||||||||
Class Type: | Trojan-activity | ||||||||||||||||||
Kill Chain: |
| ||||||||||||||||||
Threat name: | LandUpdate808 Fake Update Variant | ||||||||||||||||||
LandUpdate808 is a recently identified fake update malware variant that deceives users into downloading malicious payloads by presenting fraudulent software update prompts. Unlike other fake update malware such as SocGholish, LandUpdate808 employs a distinct delivery mechanism involving specific URI patterns like /p/land.php and /wp-content/uploads/update.php. The malware's payloads are typically named following the pattern update_DD_MM_YYYY_####### and have been observed with .js, .exe, or .msix extensions. The initial infection vector involves injecting malicious scripts into compromised websites, which then display fake update pages to visitors, prompting them to download and execute the malicious payload. | |||||||||||||||||||
Threat Protected: | 14 | ||||||||||||||||||
Rule Set Type: |
| ||||||||||||||||||
Class Type: | Trojan-activity | ||||||||||||||||||
Kill Chain: |
| ||||||||||||||||||
Known exploited vulnerabilities (Week 1 - January 2025)
For more information, please visit the Red Piranha Forum:
https://forum.redpiranha.net/t/known-exploited-vulnerabilities-catalog-1st-week-of-january-2025/535
Vulnerability | CVSS | Description | |
CVE-2024-3393 | 8.7 (High) | Palo Alto Networks PAN-OS Malicious DNS Packet Vulnerability |
Updated Malware Signatures (Week 1 - January 2025)
Threat | Description | |
Lumma Stealer | A type of malware classified as an information stealer. Its primary purpose is to steal sensitive information from infected systems, including but not limited to credentials, financial information, browser data, and potentially other personal or confidential information. | |
Mirai | A malware that turns networked devices running out-of-date Linux-based firmware—such as routers, IP cameras, and other Internet of Things (IoT) devices—into remotely controlled bots. These bots are then used as part of a botnet in large-scale Distributed Denial of Service (DDoS) attacks. |
| Ransomware Report | |
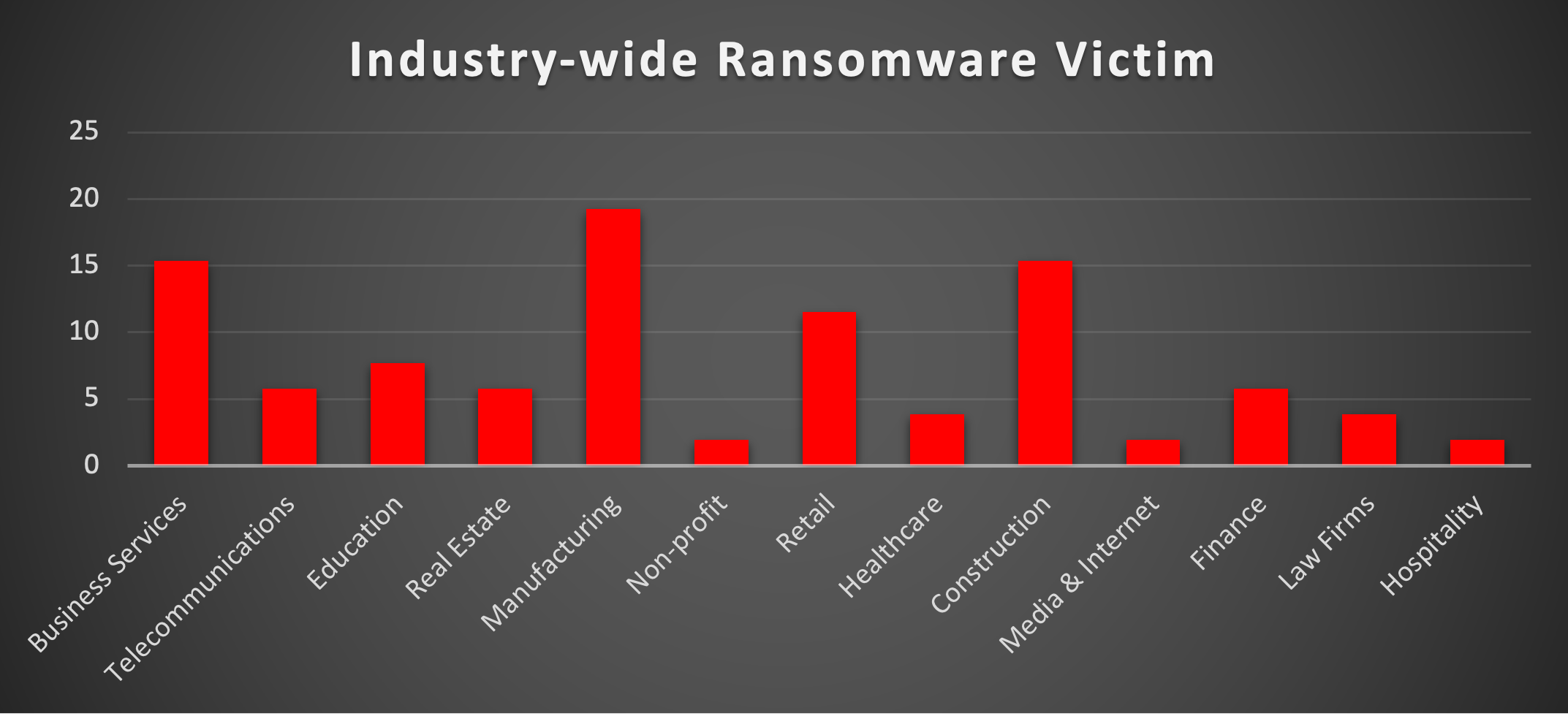
The Red Piranha Team conducts ongoing surveillance of the dark web and other channels to identify global organisations impacted by ransomware attacks. In the past week, our monitoring revealed multiple ransomware incidents across diverse threat groups, underscoring the persistent and widespread nature of these cyber risks. Presented below is a detailed breakdown of ransomware group activities during this period. | |
| Name of Ransomware Group | Overall %age of total attack coverage |
El Dorado | 1.92% |
DarkVault | 3.85% |
15.38% | |
RansomHouse | 1.92% |
RA Group | 7.69% |
Inc Ransom | 1.92% |
Space Bears | 1.92% |
DragonForce | 3.85% |
Arcus Media | 13.46% |
FunkSec | 1.92% |
7.69% | |
Handala | 1.92% |
13.46% | |
Cloak | 5.77% |
Ciphbit | 1.92% |
Cicada3301 | 1.92% |
Hunters | 1.92% |
Lynx | 1.92% |
8base | 9.62% |
RansomHouse Ransomware Analysis
1. Overview
The Red Piranha Team conducts ongoing surveillance of the dark web and other channels to identify global organisations impacted by ransomware attacks. Since late 2021, our monitoring has revealed consistent activity from the RansomHouse ransomware group. Despite positioning themselves as a "professional mediator community," their operations remain aggressive, combining data encryption with double-extortion tactics. They primarily target enterprise-level hypervisor systems, exploiting vulnerabilities and misconfigurations. Their attacks are supported by sophisticated tools such as Mario ESXi ransomware and the MrAgent automation tool, enabling large-scale ransomware deployments.
2. Key Findings
- Primary Targets: Corporate Windows and Linux hypervisor environments.
- Key Tools: Mario ESXi ransomware, MrAgent deployment automation tool.
- Attack Strategy: Double extortion (data encryption + public data exposure).
- Infrastructure: CDN servers, Command-and-Control (C2) servers, and Tor-based communication platforms.
- Tool Evolution: Heavy reliance on leaked Babuk ransomware source code for Mario ESXi.
3. Ransomware Tools and Techniques
3.1 MrAgent Binary
Purpose: Automates and streamlines the deployment of ransomware across extensive hypervisor environments.
Platform Compatibility: Windows & ESXi.
Key Features:
- Creates unique host identifiers using hostname and MAC addresses.
- Disables ESXi firewalls.
- Executes remote commands on infected systems.
- Removes files and drops SSH sessions.
- Modifies welcome messages displayed on ESXi hypervisor consoles.
- Maintains ongoing communication with C2 servers.
Command-and-Control Protocol: JSON-based protocol for consistent communication with C2 servers. Supports commands like info, config, exec, run, remove, abort, and quit.
Windows Binary Adjustments:
- Utilises PowerShell for key functionalities.
- Limited ability to disable firewalls or modify system passwords.
- Relies on popen syscalls for command execution.
3.2 Mario ESXi Ransomware
Background: Forked from the leaked Babuk ransomware source code.
Capabilities:
- Encrypts virtual machines efficiently.
- Changes root system passwords.
- Iteratively shuts down and encrypts VMs to maximise damage.
- Blocks remote management services.
Common Commands:
- esxcli network firewall set --enabled false
- ps | grep sshd | grep -v root | awk {print "kill -9", $2} | sh
4. Tactics, Techniques, and Procedures (TTPs)
Tactic | Technique | ID | Description |
Initial Access | Valid Accounts | T1078.002 | Exploiting weak credentials for access |
Exploit Public-Facing Application | T1190 | Vulnerabilities in public-facing systems | |
Resource Development | Acquire Infrastructure | T1583.004 | Leveraging CDN servers for data exfiltration |
Execution | Unix Shell | T1059.004 | Direct execution of shell commands |
Lateral Movement | Remote Services | T1021.001 | Unauthorised RDP/SMB sessions |
Impact | Data Encrypted for Impact | T1486 | Encrypted virtual machine data |
Command-and-Control | Application Layer Protocol | T1071 | JSON-based communication via C2 servers |
Discovery | System Network Discovery | T1016 | Gathering IP and MAC address information |
5. Indicators of Compromise (IOCs)
MrAgent File Hashes:
- 8189c708706eb7302d7598aeee8cd6bdb048bf1a6dbe29c59e50f0a39fd53973
- bfc9b956818efe008c2dbf621244b6dc3de8319e89b9fa83c9e412ce70f82f2c
Mario ESXi File Hashes:
- 3934b3da6bad0b4a28483e25e7bab919d7ed31f2f51cca22c56535b9f8183a0e
- afe398e95a75beb4b0508c1bbf7268e8607d03776af0b68386d1e2058b374501
Windows-Specific Hashes:
- bfc9b956818efe008c2dbf621244b6dc3de8319e89b9fa83c9e412ce70f82f2c
6. Recommendations for Mitigation
- Patch Systems Regularly: Ensure all hypervisors are up to date.
- Secure Remote Access: Limit access to essential services.
- Deploy Advanced Endpoint Protection: Use EDR solutions for threat detection.
- Backup Regularly: Store backups offline and validate integrity.
- Monitor Traffic Patterns: Flag suspicious JSON-based C2 communications.
- Employee Awareness: Provide regular training on phishing and social engineering.
Chat Server:
URLs |
File servers |
Chat servers |
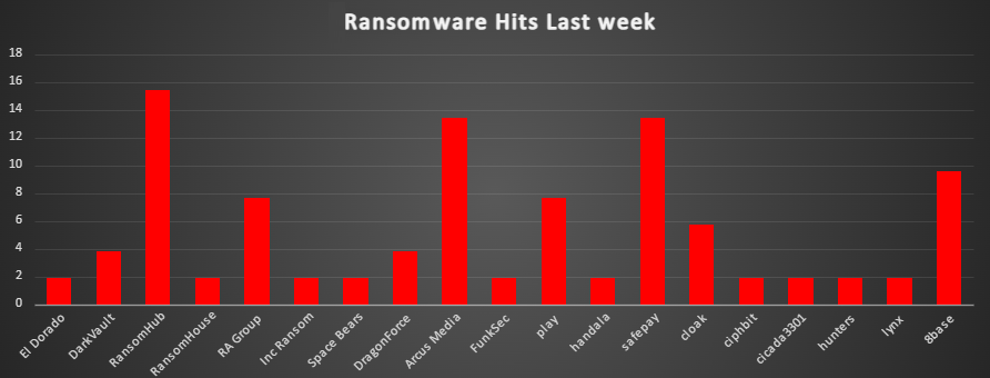
Ransomware Victims Worldwide
A recent ransomware analysis reveals that the United States remains the most heavily impacted nation, accounting for a staggering 38.46% of global incidents, highlighting its continued vulnerability to ransomware threats. Following this, Singapore reported 7.69% of the attacks, emerging as a notable target.
Countries including Germany, France, Spain, and Brazil each accounted for 5.77% of the incidents, reflecting a significant level of exposure. Meanwhile, Canada and Australia reported 3.85% of ransomware attacks, underscoring persistent threats across North America and Oceania.
A broader set of countries, including Mongolia, Greece, South Africa, New Zealand, Italy, Ukraine, Tanzania, India, Belgium, Vietnam, Portugal, and Japan, each contributed 1.92% to the overall ransomware incident landscape, signifying a widespread global reach of these attacks.
This analysis underscores the persistent and global nature of ransomware threats, with North America and parts of Asia bearing a significant portion of the impact. The findings emphasise the critical need for strengthened cybersecurity infrastructure, proactive defence strategies, and heightened vigilance across all sectors to combat the relentless growth of ransomware attacks worldwide.
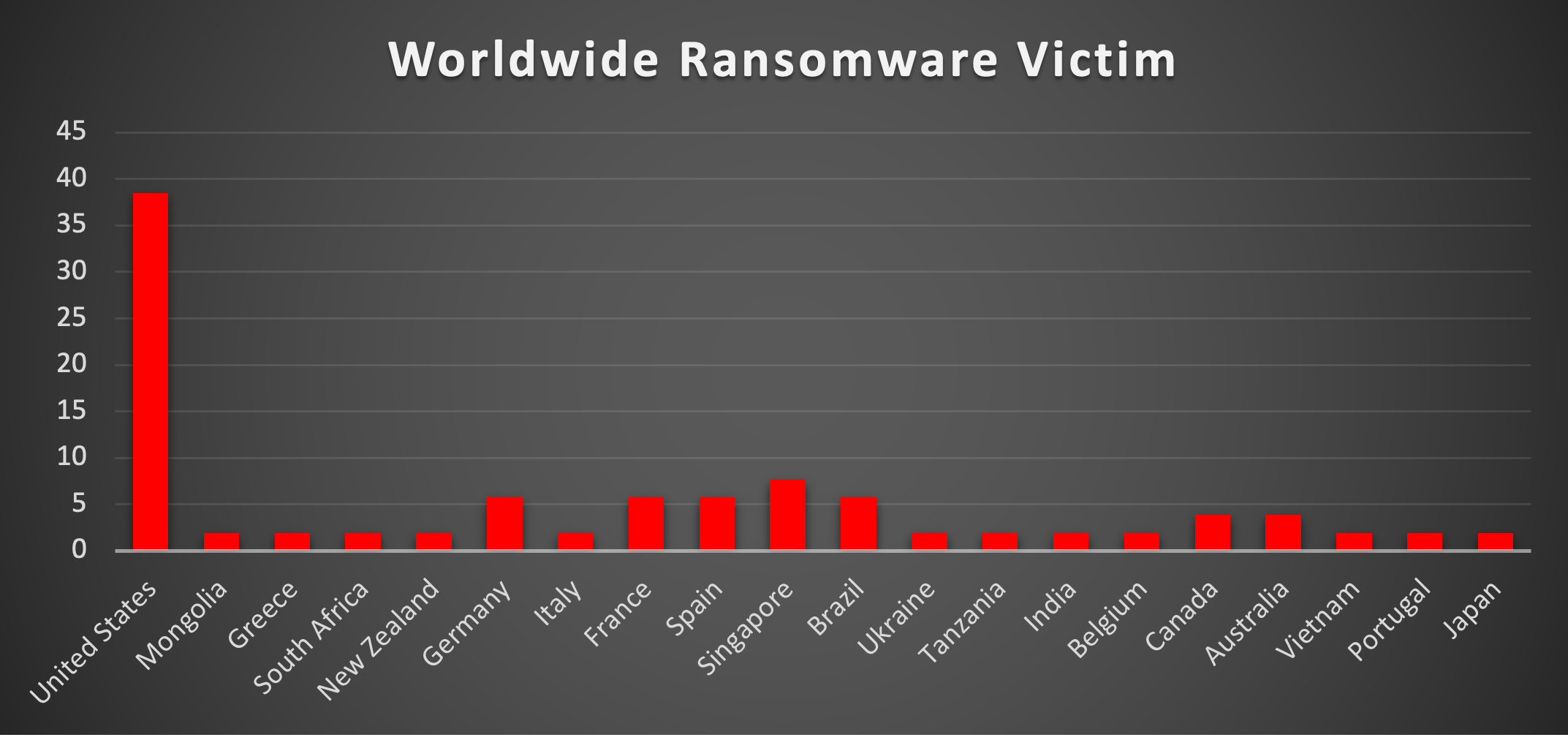
Ransomware Victims Industry-wide
A recent ransomware analysis highlights the Manufacturing sector as the most targeted industry, accounting for 19.23% of total reported incidents. This emphasises the critical vulnerability of essential production and supply chain operations to cyber threats.
Following closely are the Business Services and Construction sectors, each representing 15.38% of ransomware attacks. The Retail sector follows with 11.54%, reflecting its susceptibility due to customer-facing operations and transactional systems.
Industries such as Education (7.69%), Telecommunications, Real Estate, and Finance (each 5.77%) also faced significant ransomware exposure. Meanwhile, Healthcare and Law Firms reported 3.85% of incidents, indicating ongoing cybersecurity challenges in sectors handling sensitive data.
Sectors with a smaller, yet notable impact include Non-profit, Media & Internet, and Hospitality, each contributing 1.92% of reported incidents.
This analysis underscores the pervasive and indiscriminate nature of ransomware threats, impacting industries across critical infrastructure, public services, and commercial enterprises. The findings highlight the pressing need for tailored cybersecurity strategies, robust defences, and proactive risk management to mitigate the ever-evolving ransomware landscape effectively.