
Trends
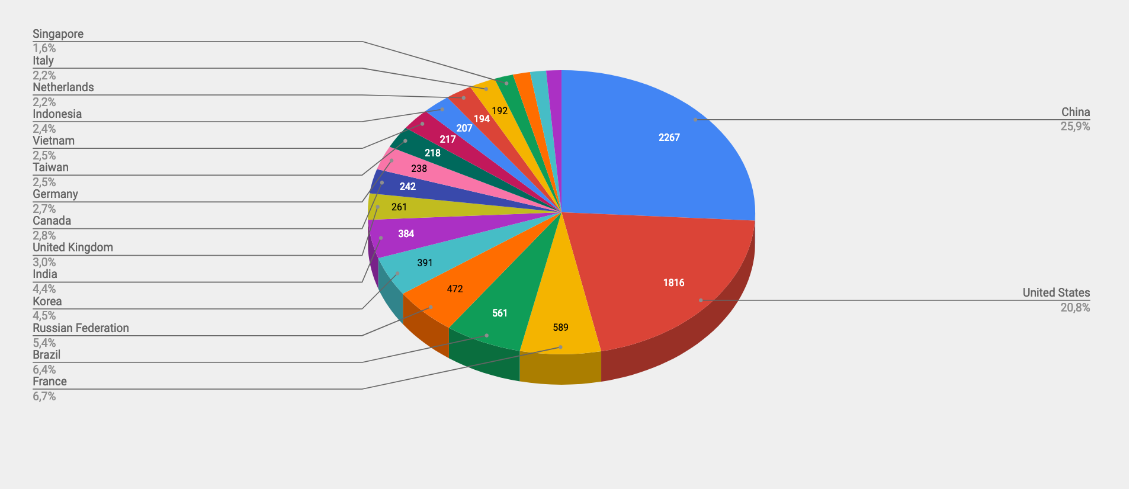
- The top attacker country was China with 2267 unique attackers (25.94%)
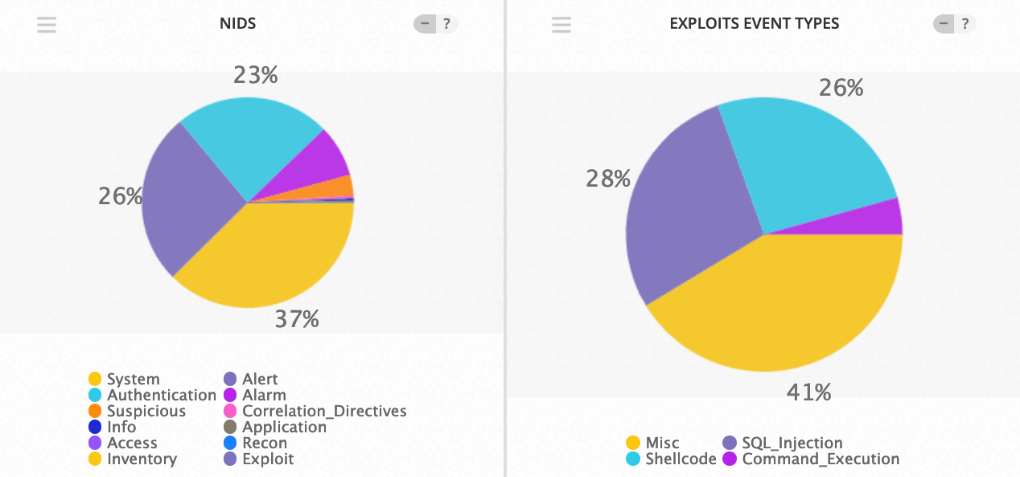
- The top Exploit event was Miscellaneous with 41% of occurrences
Top Attacker by Country
| Country | No. of Attackers | Occurrences |
|---|---|---|
| China | 2267 | 25.94% |
| United States | 1816 | 20.78% |
| France | 589 | 6.74% |
| Brazil | 561 | 6.42% |
| Russian Federation | 472 | 5.40% |
| Korea | 391 | 4.47% |
| India | 384 | 4.39% |
| United Kingdom | 261 | 2.99% |
| Canada | 242 | 2.77% |
| Germany | 238 | 2.72% |
| Taiwan | 218 | 2.49% |
| Vietnam | 217 | 2.48% |
| Indonesia | 207 | 2.37% |
| Netherlands | 194 | 2.22% |
| Italy | 192 | 2.20% |
| Singapore | 138 | 1.58% |
| Colombia | 125 | 1.43% |
| Spain | 117 | 1.34% |
| Thailand | 111 | 1.27% |
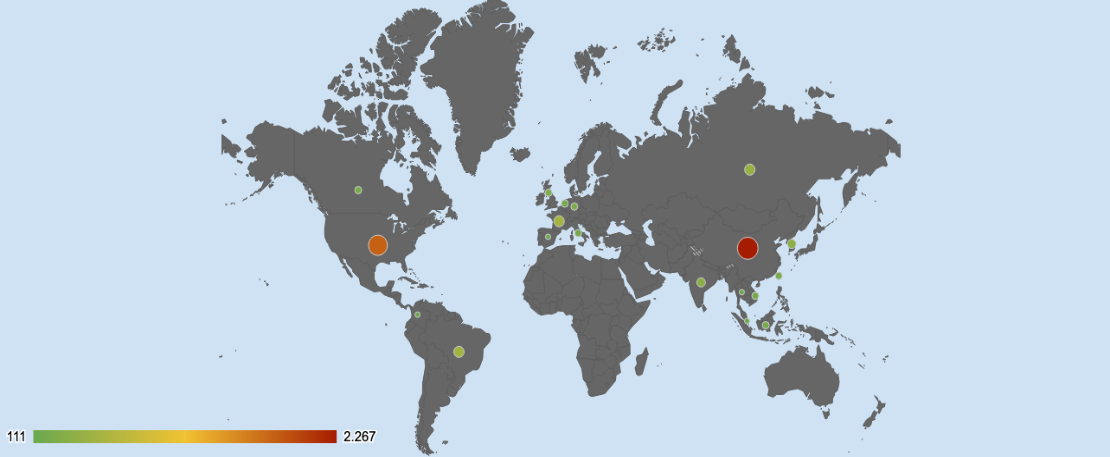
Threat Geo-location
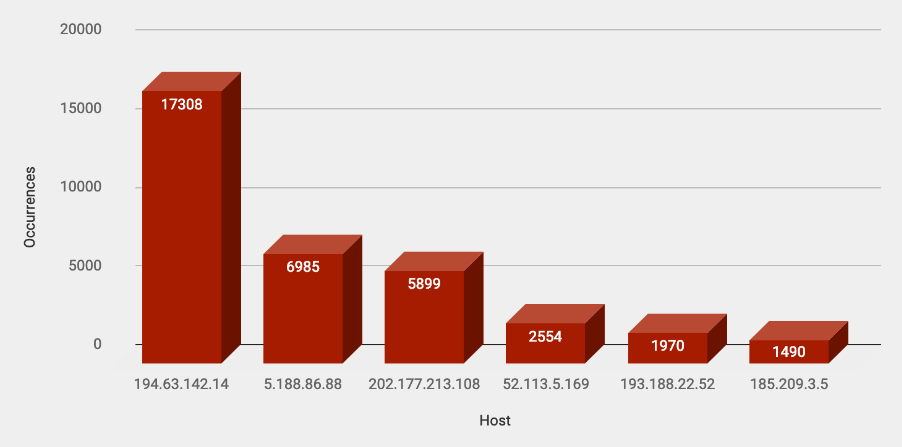
Top Attacking Hosts
| Host | Occurrences |
|---|---|
| 194.63.142.14 | 17308 |
| 5.188.86.88 | 6985 |
| 202.177.213.108 | 5899 |
| 193.188.22.52 | 1970 |
| 185.209.3.5 | 1490 |
Top Network Attackers
| Origin AS | Announcement | Description |
|---|---|---|
| AS50113 | 194.63.142.0/24 | NTX |
| AS49453 | 5.188.86.0/24 | Channelnet LTD |
| AS17819 | 202.177.212.0/22 | Equinix Australia Pty Ltd |
| AS8075I | 52.122.0.0/14 | Microsoft Corporation |
| AS57043 | 193.188.22.0/24 | xWEB LTD |
| AS209804 | 185.209.3.0/24 | SIA "IT Services" |
| AS16509 | 52.10.0.0/15 | Amazon Technologies Inc. |
Exploit Event Types and Top Event NIDS
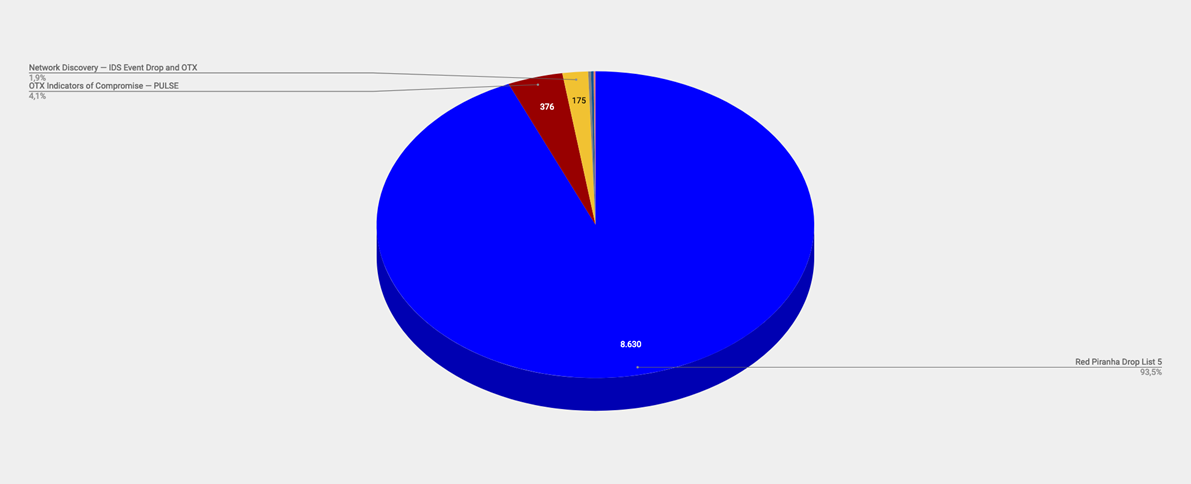
Top Alarms
| Type of Alarm | No. of Occurrences |
|---|---|
| Red Piranha Drop List 5 | 8630 |
| OTX Indicators of Compromise - PULSE | 376 |
| Network Discovery - IDS Event Drop and OTX | 175 |
| Database Attack - Stored Procedure Access - Attack | 19 |
| Attack Tool Detected - Attack | 18 |
| Webserver Attack - Attack Bruteforce Authentication - SSH | 10 |
| Bruteforce Authentication - SSH | 2 |
Comparison from Last Week
| Type of Alarm | No. of Occurrences |
|---|---|
| IDS Event | 6670 |
| Environmental Awareness - OTX Indicators of Compromise - PULSE | 283 |
| Reconnaissance & Probing — DatabaseAttack - Stored Procedure Access — Attack | 182 |
| Reconnaissance & Probing — Attack Tool detected — Attack | 92 |
| Delivery & Attack — WebServer Attack — Attack | 41 |
| Reconnaissance & Probing — Attack Tool detected — SSH | 22 |
| Delivery & Attack — Bruteforce Authentication — SSH | 8 |
| Exploitation & Installation — WebServer Attack — XSS | 3 |
| Environmental Awareness — Trojan infection — IDS Event | 2 |
CVE
This is a list of recent vulnerabilities for which exploits are available.
CVE-2019-9125
An issue was discovered on D-Link DIR-878 1.12B01 devices. Because strncpy is misused, there is a stack-based buffer overflow vulnerability that does not require authentication via the HNAP_AUTH HTTP header
CVE-2019-9041
An issue was discovered in ZZZCMS zzzphp V1.6.1. In the inc/zzz_template.php file, the parserIfLabel() function's filtering is not strict, resulting in PHP code execution, as demonstrated by the if:assert substring.
CVE-2019-9025
An issue was discovered in PHP 7.3.x before 7.3.1. An invalid multibyte string supplied as an argument to the mb_split() function in ext/mbstring/php_mbregex.c can cause PHP to execute memcpy() with a negative argument, which could read and write past buffers allocated for the data.
CVE-2019-9023
An issue was discovered in PHP before 5.6.40, 7.x before 7.1.26, 7.2.x before 7.2.14, and 7.3.x before 7.3.1. A number of heap-based buffer over-read instances are present in mbstring regular expression functions when supplied with invalid multibyte data. These occur in ext/mbstring/oniguruma/regcomp.c, ext/mbstring/oniguruma/regexec.c, ext/mbstring/oniguruma/regparse.c, ext/mbstring/oniguruma/enc/unicode.c, and ext/mbstring/oniguruma/src/utf32_be.c when a multibyte regular expression pattern contains invalid multibyte sequences.
CVE-2019-8985
On Netis WF2880 and WF2411 2.1.36123 devices, there is a stack-based buffer overflow that does not require authentication. This can cause denial of service (device restart) or remote code execution. This vulnerability can be triggered by a GET request with a long HTTP "Authorization: Basic" header that is mishandled by user_auth->user_ok in /bin/boa.
CVE-2018-20122
The web interface on FASTGate Fastweb devices with firmware through 0.00.47_FW_200_Askey 2017-05-17 (software through 1.0.1b) exposed a CGI binary that is vulnerable to a command injection vulnerability that can be exploited to achieve remote code execution with root privileges. No authentication is required in order to trigger the vulnerability.
CVE-2019-8979
Koseven through 3.3.9, and Kohana through 3.3.6, has SQL Injection when the order_by() parameter can be controlled.
CVE-2019-8950
The backdoor account dnsekakf2$$ in /bin/login on DASAN H665 devices with firmware 1.46p1-0028 allows an attacker to login to the admin account via TELNET.
CVE-2019-8948
PaperCut MF before 18.3.6 and PaperCut NG before 18.3.6 allow script injection via the user interface, aka PC-15163.
Vulnerabilities
WPA2 Key Reinstallation Multiple Security Weaknesses
2019-02-21
securityfocus.com/bid/101274
