| New Threat Detection Added | 4 (KEKW Python Stealer, Atomic Stealer, ScarCruft APT and Atlassian Confluence CVE-2023-22527) |
| New Threat Protections | 237 |
| New Ransomware Victims Last Week | 111 |
Weekly Detected Threats
The following threats were added to Crystal Eye XDR this week:
Threat name: | KEKW Python Stealer | ||||||||||||||||||||||||
PyPI (Python Package Index) serves as a vital hub for Python developers globally, enabling code sharing and distribution. Unfortunately, its popularity makes it an attractive target for Threat Actors (TAs). TAs exploit PyPI by uploading malicious packages, disguising them as legitimate software or mimicking well-known projects. Recently, Researchers identified malicious Python .whl files distributing a new malware named KEKW. This malware not only steals sensitive information but also engages in clipper activities, potentially hijacking cryptocurrency transactions. | |||||||||||||||||||||||||
Threat Protected: | 02 | ||||||||||||||||||||||||
Rule Set Type: |
| ||||||||||||||||||||||||
Class Type: | Trojan-activity | ||||||||||||||||||||||||
Kill Chain: |
| ||||||||||||||||||||||||
Threat name: | Atomic Stealer | |||||||||||||||||||||
Atomic Stealer (AMOS), a popular Mac-targeting stealer, underwent an update introducing payload encryption to evade detection. Prolific in malvertising and compromised sites, AMOS developers justified its $3000/month rental fee with continuous enhancements. A January 2024 malvertising campaign revealed the updated version, potentially accessed by customers through software cracks. Despite a holiday slowdown in malvertising, a renewed campaign featured AMOS's updated variant. As Mac users face persistent threats, caution in downloading software from reputable sources is crucial, given the deceptive nature of malicious ads. Reported incidents to relevant parties aim for prompt mitigation. | ||||||||||||||||||||||
Threat Protected: | 01 | |||||||||||||||||||||
Rule Set Type: |
| |||||||||||||||||||||
Class Type: | Trojan-activity | |||||||||||||||||||||
Kill Chain: |
| |||||||||||||||||||||
Threat name: | ScarCruft APT | ||||||||||||||||||
ScarCruft, also known as APT37 and InkySquid, is a suspected North Korean cyber threat group. They are currently in the planning and testing stages, using a technical threat research report on Kimsuky as a decoy. ScarCruft focuses on gathering insights from technical threat intelligence consumers, aiming to refine their operational approaches. Their use of oversized Windows Shortcut files in infection chains, delivering the RokRAT backdoor, demonstrates their advanced tactics. By targeting high-profile North Korean affairs experts, ScarCruft aligns with its goal of strategic intelligence gathering, contributing to North Korea's decision-making. The group's interest in mimicking cybersecurity professionals suggests a growing threat landscape with potential implications for specific targets and brand impersonation. | |||||||||||||||||||
Threat Protected: | 32 | ||||||||||||||||||
Rule Set Type: |
| ||||||||||||||||||
Class Type: | Trojan-activity | ||||||||||||||||||
Kill Chain: |
| ||||||||||||||||||
Threat name: | Atlassian Confluence RCE (CVE-2023-22527) | ||||||||||||||||||
A template injection vulnerability present in earlier versions of Confluence Data Center and Server enables an unauthorised attacker to execute remote code on a compromised instance. The most recent supported iterations of Confluence Data Centre and Server remain unaffected, as the vulnerability was successfully addressed in routine version updates. Nevertheless, Atlassian advises customers to prioritise installing the latest version to safeguard their instances against non-critical vulnerabilities highlighted in the January Security Bulletin. | |||||||||||||||||||
Threat Protected: | 1 | ||||||||||||||||||
Rule Set Type: |
| ||||||||||||||||||
Class Type: | Attempted-admin | ||||||||||||||||||
Kill Chain: |
| ||||||||||||||||||
Known exploited vulnerabilities (Week 4 - January 2024)
Threat | CVSS | Description | |
CVE-2023-34048 | 9.8 (Critical) | VMware vCenter Server Out-of-Bounds Write Vulnerability | |
CVE-2023-22527 | 9.8 (Critical) | Atlassian Confluence Data Centre and Server Template Injection Vulnerability |
Updated Malware Signatures (Week 4 - January 2024)
Threat | Description | |
Valyria | A Microsoft Word-based malware which is used as a dropper for second-stage malware. | |
LokiBot | An information-stealer malware used to gather data from victims’ machines such as stored account credentials, banking information and other personal data. | |
CoinMiner | This malicious software installs and runs cryptocurrency mining applications. | |
Qakbot | A malware designed to acquire valuable data such as banking credentials and is also capable of stealing FTP credentials and spreading across a network by utilising SMB. |
| New Ransomware Victims Last Week: | 111 | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
The Red Piranha Team actively collects information on organisations globally affected by ransomware attacks from various sources, including the Dark Web. In the past week alone, our team uncovered a total of 111 new ransomware victims or updates on previous victims across 21 different industries spanning 21 countries. This underscores the widespread and indiscriminate impact of ransomware attacks, emphasising their potential to affect organisations of varying sizes and sectors worldwide. LockBit 3.0 ransomware group stands out as the most prolific, having updated a significant number of victims (27) distributed across multiple countries. In comparison, Blackbasta and Akira ransomware groups updated 13 and 9 victims, respectively, in the past week. The following list provides the victim counts in percentages for these ransomware groups and a selection of others. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Name of Ransomware Group | Percentage of new Victims last week | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
0Mega | 0.90% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
8Base | 7.21% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Abyss data | 0.90% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Akira | 8.11% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Alphv | 6.31% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Bianlian | 4.50% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Blackbasta | 11.71% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Cactus | 1.80% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Cuba | 0.90% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Hunters | 6.31% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Inc Ransom | 1.80% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Lockbit3 | 24.32% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Medusa | 5.41% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Meow | 0.90% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Money Message | 0.90% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Monti | 0.90% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Mydata | 7.21% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Play | 0.90% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Qilin | 2.70% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Ransomhouse | 1.80% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Trigona | 4.50% | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
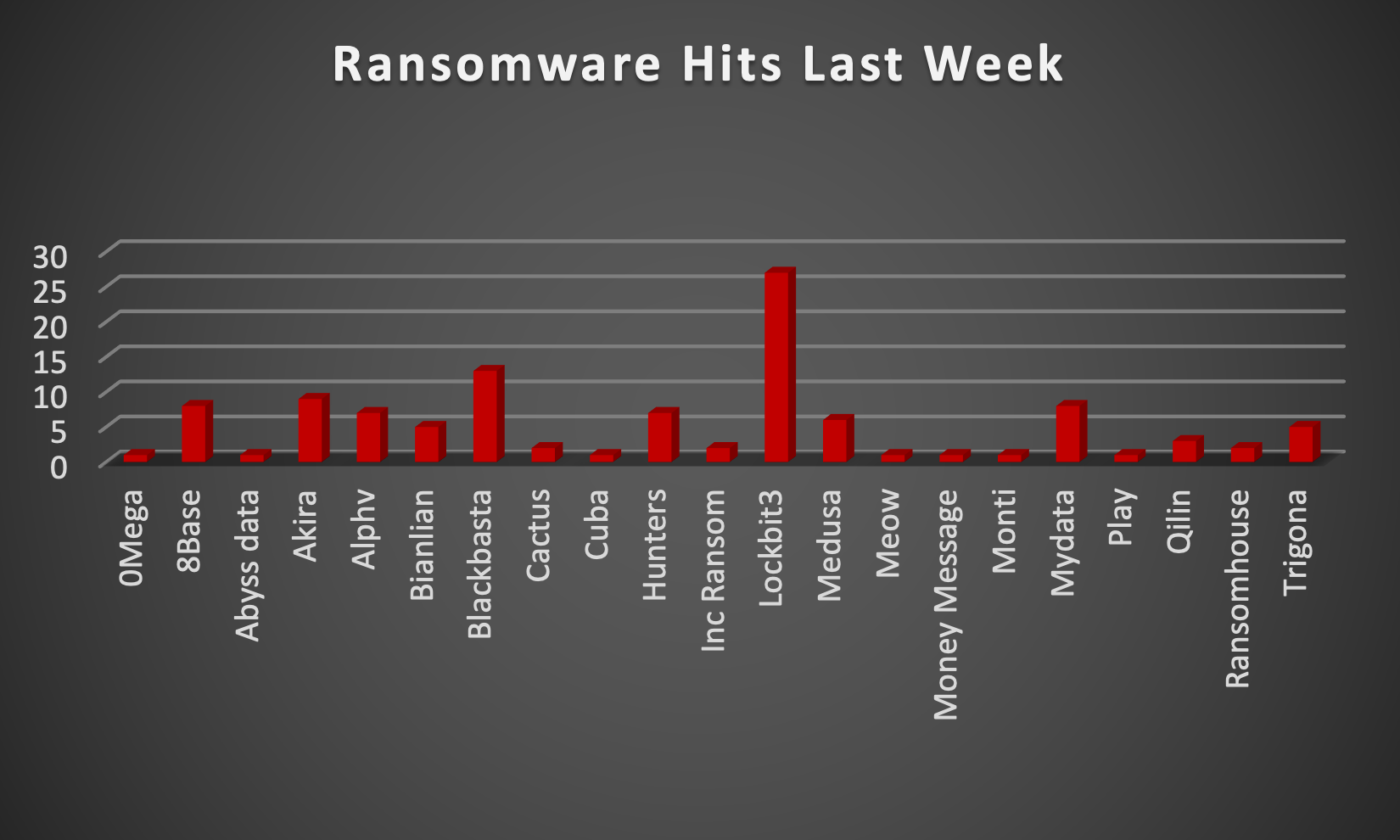
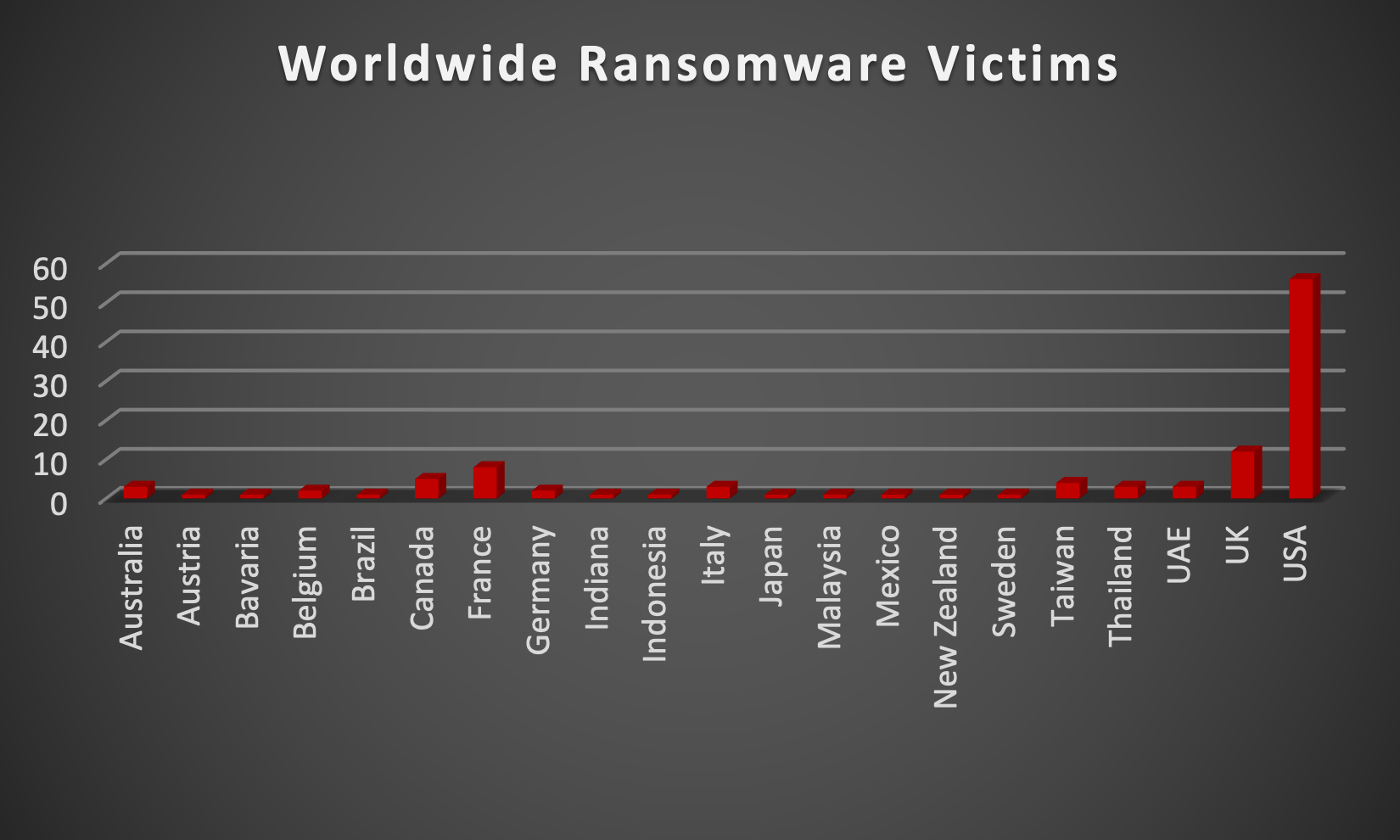
LockBit3.0, also known as LockBit Black, stands out as a highly dangerous ransomware that has inflicted widespread damage on a global scale. Its history unfolds with the emergence of the original LockBit in 2016, initially a basic but effective ransomware. By 2019, LockBit 2.0 arrived, featuring enhanced encryption and a focus on larger organisations. A significant shift occurred in 2020 when LockBit transformed into a Ransomware-as-a-Service (RaaS) model, allowing anyone to launch ransomware attacks through its platform. This evolution marked a turning point, granting widespread access to LockBit and amplifying its threat level. In 2022, LockBit3.0, or LockBit Black, made its debut, introducing increased modularity, evasion tactics, and customisation, making detection and prevention more challenging. LockBit3.0 has left a trail of disruption across critical sectors, impacting hospitals, schools, and government agencies. In 2021, it notably crippled the Colonial Pipeline, leading to significant fuel disruptions in the US. Even manufacturing giants like CISA and Samsung have fallen victim to LockBit's powerful encryption. Efforts are underway globally to dismantle LockBit and its operators, with companies investing heavily in defence measures. Despite these endeavours, LockBit3.0 remains a persistent threat. Its RaaS model ensures constant evolution, posing an ongoing challenge for the cybersecurity community. Staying vigilant and implementing robust security practices are crucial to confront this ever-growing and evolving cyber threat. In a comprehensive analysis of ransomware victims across 21 countries, the United States emerges as the most heavily impacted nation, reporting a staggering 56 victim updates in the past week. The following list provides a breakdown of the number and percentage of new ransomware victims per country, underscoring the persistent and concerning prevalence of ransomware attacks, with the USA particularly susceptible to these cybersecurity threats.
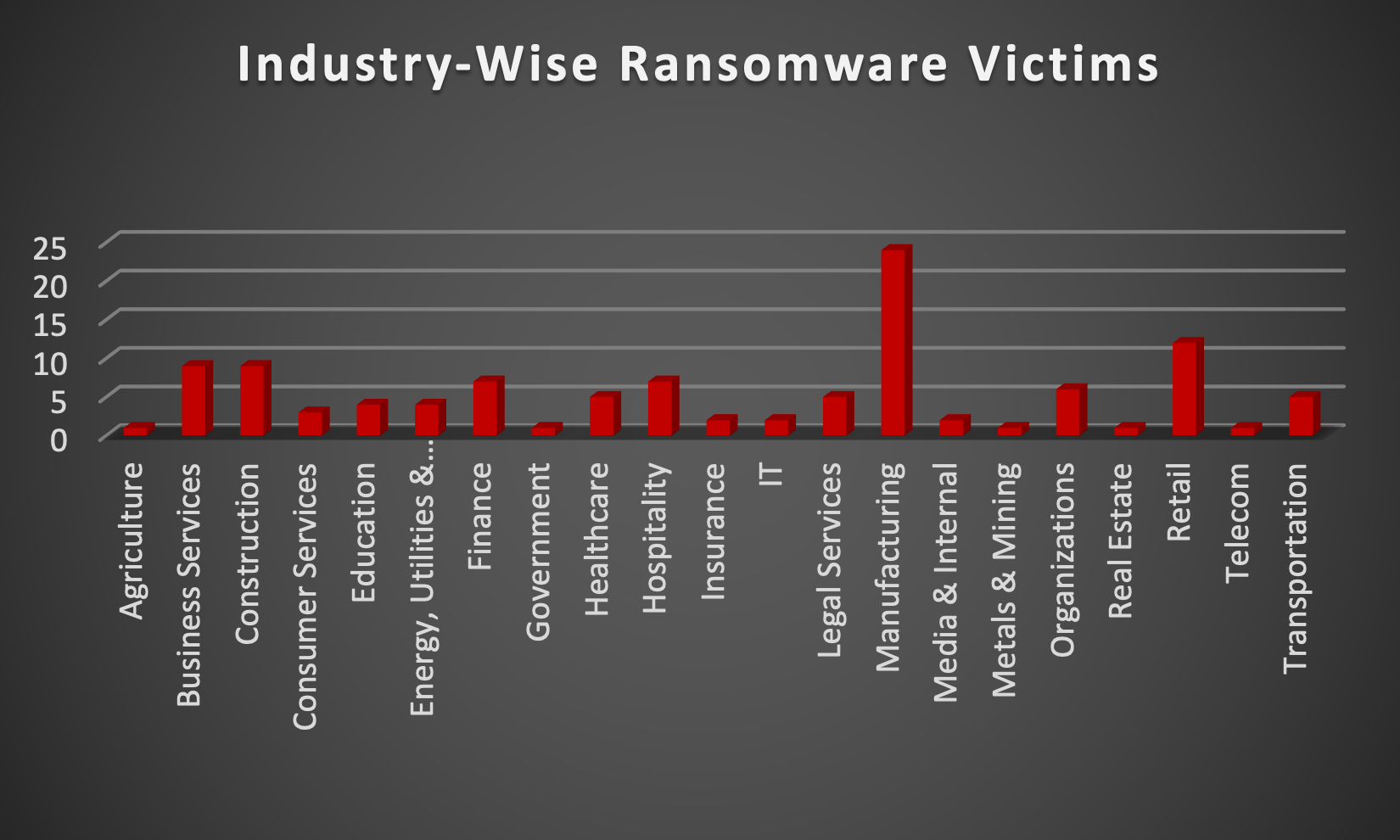
 Upon further investigation, it has been identified that ransomware has left its mark on 21 different industries worldwide. Notably, the Manufacturing and Retail sectors bore the brunt of the attacks in the past week, accounting for 21% and 10% of the total ransomware victims, respectively. The table below delineates the most recent ransomware victims, organised by industry, shedding light on the sectors grappling with the significant impact of these cyber threats.
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||