Trends
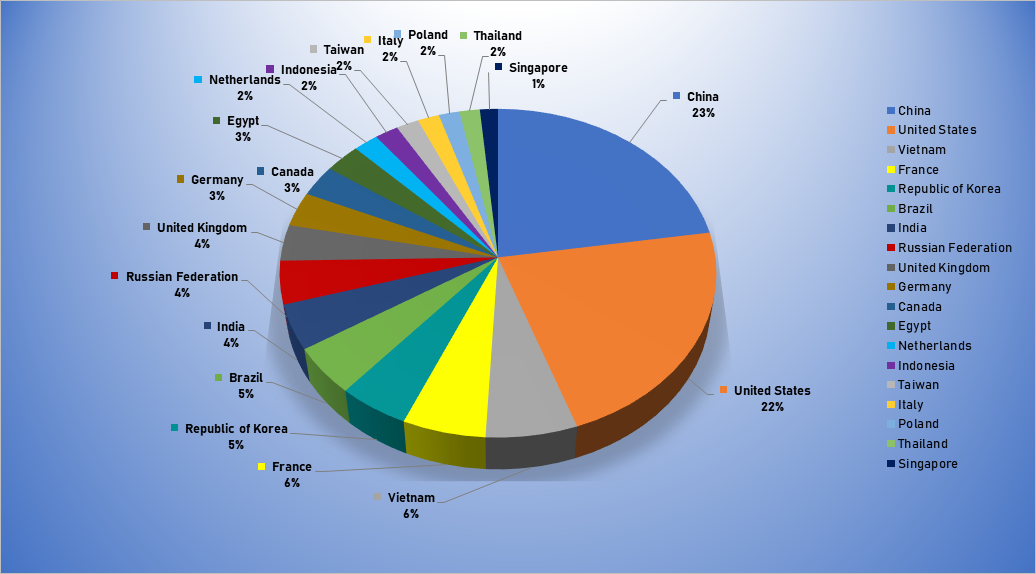
- The top attacker country was China with 1185 unique attackers (23%).
- The top Exploit event was SSH Attack Tool with 99% of occurrences.
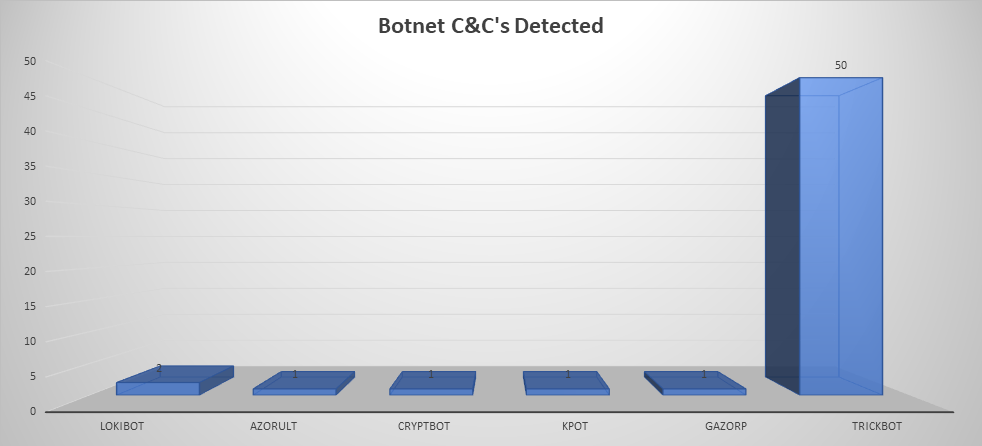
- The top Trojan C&C server detected was TrickBot with 50 instances detected.
Top Attacker by Country
| Country | Occurrences | Percentage |
|---|---|---|
| China | 1185 | 22.52% |
| United States | 1163 | 22.11% |
| Vietnam | 326 | 6.20% |
| France | 297 | 5.65% |
| Republic of Korea | 253 | 4.81% |
| Brazil | 249 | 4.73% |
| India | 233 | 4.43% |
| Russian Federation | 223 | 4.24% |
| United Kingdom | 187 | 3.55% |
| Germany | 179 | 3.40% |
| Canada | 164 | 3.12% |
| Egypt | 153 | 2.91% |
| Netherlands | 107 | 2.03% |
| Indonesia | 100 | 1.90% |
| Taiwan | 97 | 1.84% |
| Italy | 92 | 1.75% |
| Poland | 89 | 1.69% |
| Thailand | 87 | 1.65% |
| Singapore | 77 | 1.46% |
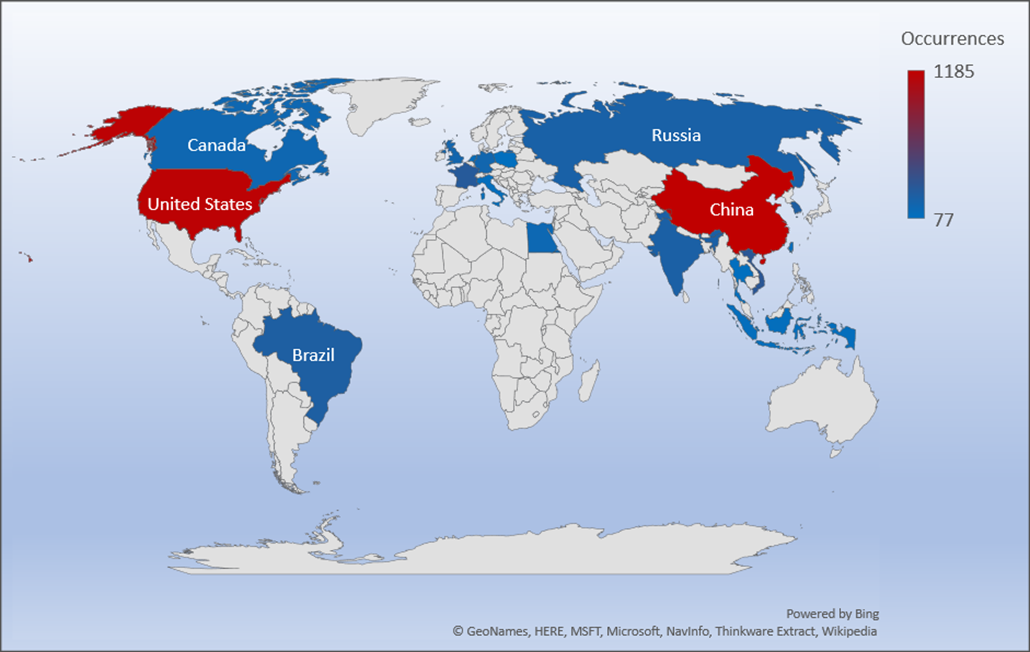
Threat Geo-location
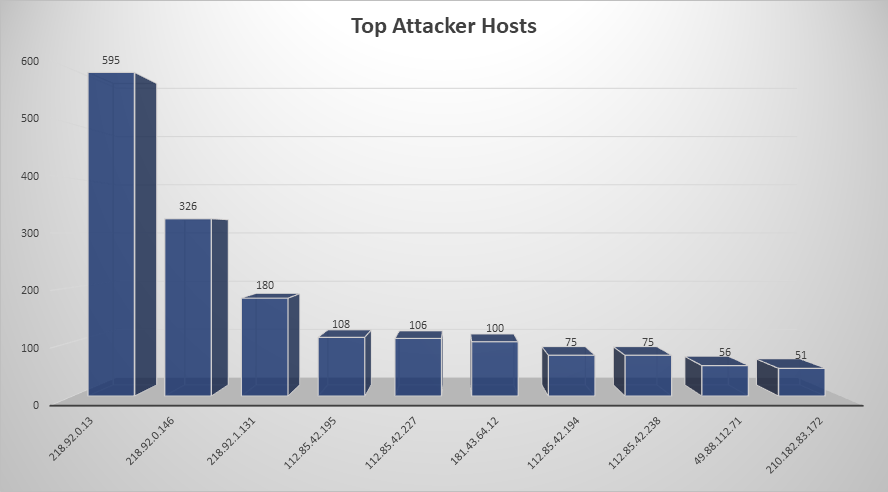
Top Attacking Hosts
| Host | Occurrences |
|---|---|
| 218.92.0.13 | 595 |
| 218.92.0.146 | 326 |
| 218.92.1.131 | 180 |
| 112.85.42.195 | 108 |
| 112.85.42.227 | 106 |
| 181.43.64.12 | 100 |
| 112.85.42.194 | 75 |
| 112.85.42.238 | 75 |
Top Network Attackers
| Origin AS | Announcement | Description |
|---|---|---|
| AS4134 | 218.91.0.0/16 | CHINANET Jiangsu province |
| AS4837 | 112.85.42.195/13 | CHINANET Jiangsu province |
| AS6471 | 181.43.64.0/18 | ENTEL CHILE S.A. |
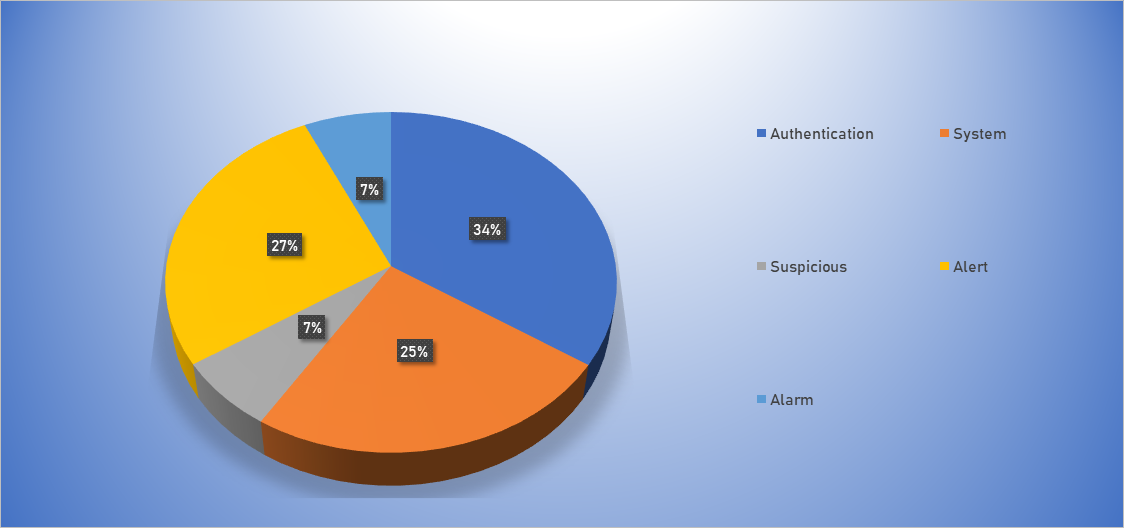
Top Event NIDS and Exploits
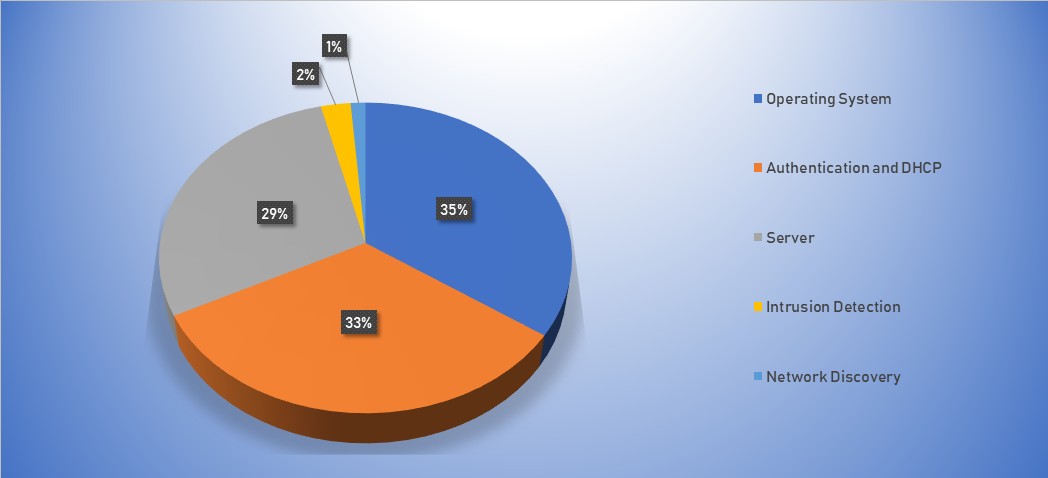
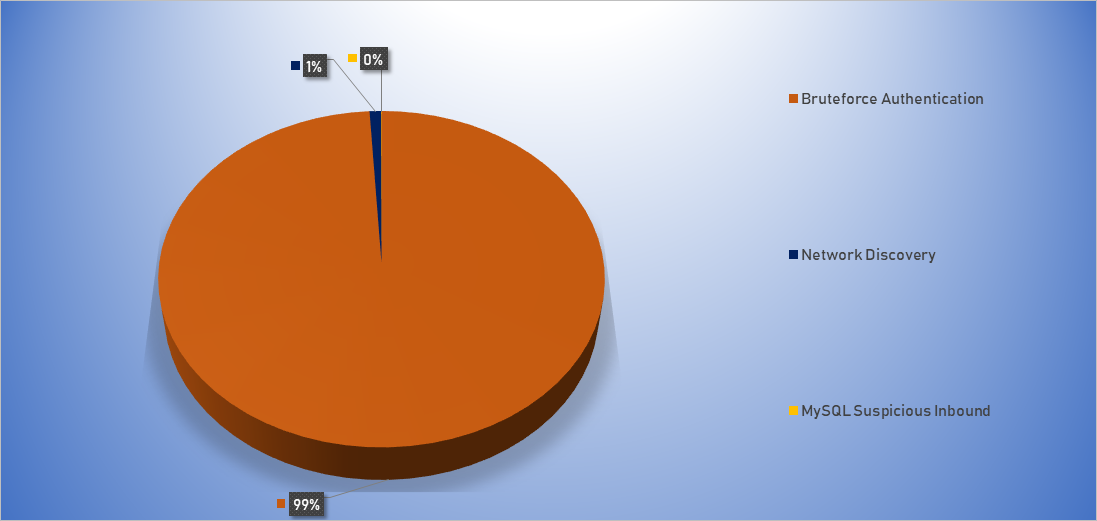
Top Alarms
| Type of Alarm | Occurrences |
|---|---|
| Bruteforce Authentication | 2844 |
| Network Discovery | 26 |
| Network Anomaly | 1 |
Comparison from last week
| Type of Alarm | Occurrences |
|---|---|
| Bruteforce Authentication | 2637 |
| Network Discovery | 14 |
| Network Anomaly | 2 |
Remote Access Trojan C&C Servers Found
| Name | Number Discovered | Location |
|---|---|---|
| Trickbot | 24 | 185.173.92.121, 185.241.52.38, 176.57.215.128, 185.141.25.91, 185.183.97.152, 85.141.27.172, 217.107.34.34, 80.87.200.37, 5.253.63.134, 185.141.27.134, 162.247.155.165, 45.239.188.88, 192.3.83.176, 198.12.101.164, 51.75.232.232, 217.107.34.104, 185.198.57.86, 37.44.215.174, 85.203.118.145, 81.177.26.91, 107.173.125.68, 85.204.116.189, 185.183.96.48, 185.141.25.79, 192.3.247.104, 23.94.184.109, 85.143.223.188, 172.245.110.126, 37.18.30.153, 185.141.25.75, 195.133.144.112, 91.228.218.50, 23.94.49.229, 23.95.44.51, 37.44.215.180, 162.248.225.20, 92.38.171.57, 31.202.132.185, 107.175.115.147, 185.141.25.126, 78.140.223.27, 185.65.202.127, 23.94.53.171, 195.123.238.9, 94.156.35.190, 195.123.245.16, 192.243.108.105, 23.94.137.229, 192.3.61.236, 85.204.116.192 |
| AzorUlt | 1 | 185.159.82.56 |
| CryptBot | 1 | 85.143.222.232 |
| KPOT | 1 | 5.53.124.117 |
| Gazorp | 1 | 162.221.190.147 |
| LokiBot | 2 | 149.129.174.115, 111.90.142.52 |
Common Malware
| Malware Type | MD5 | Typical Filename |
|---|---|---|
| Win.Trojan. Generic |
47b97de62ae8b2 b927 542aa5d7f3c858 |
qmreport upload.exe |
| Unix.Exploit. Lotoor |
f7145b132e23e3 a55d 2269a008395034 |
r2 |
| XLS Trojan Agent |
cc0f21a356dfa1 b7eb eb904ce80d9ddf |
f1cf1595f0a6ca 785e 7e511fe0df7 bc756e8d66d.xls |
| Win64 Crypto Miner | 4a50780ddb3db1 6eba b57b0ca42da0fb |
xme64-2141.exe |
| Win32 Crypto Miner | db69eaaea4d497 | xme32-2141-gcc.exe |
CVE
This is a list of recent vulnerabilities for which exploits are available.
ID: CVE-2019-9848
Title: LibreOffice Remote Code Execution and Unauthorized Access Vulnerabilities
Description: LibreOffice is exposed to a remote code execution vulnerability and unauthorized access vulnerability. Attackers can exploit these issues to execute arbitrary code in the context of the user running the affected application and gain unauthorized access and perform malicious actions. LibreOffice has a feature where documents can specify that pre-installed scripts can be executed on various document events such as mouse-over, etc. LibreOffice is typically also bundled with LibreLogo, a programmable turtle vector graphics script, which can be manipulated into executing arbitrary python commands. By using the document event feature to trigger LibreLogo to execute python contained within a document a malicious document could be constructed which would execute arbitrary python commands silently without warning. In the fixed versions, LibreLogo cannot be called from a document event handler.
Vendor: LibreOffice
Publish Date: 2019-17-07 Last Update Date: 2019-29-07
CVSS Score 7.5
ID: CVE-2019-7839
Title: Adobe ColdFusion Arbitrary Command Injection Vulnerability
Description: ColdFusion vulnerable versions have a command injection vulnerability. Successful exploitation could lead to arbitrary code execution.
Adobe Digital Editions is exposed to an unspecified arbitrary command injection vulnerability. Attackers can exploit this issue to execute arbitrary code in the context of the application. An attacker could exploit this vulnerability to compromise Confidentiality, Integrity and/or Availability.
Vendor: Adobe
Publish Date: 2019-12-06 Last Update Date: 2019-26-06
CVSS Score 10.0
ID: CVE-2019-1010241
Title: Jenkins Credentials Binding Plugin Information Disclosure Vulnerability
Description: Jenkins Credentials Binding plugin is exposed to an information disclosure vulnerability. An attacker can exploit this issue to gain access to sensitive information that may aid in further attacks. Jenkins Credentials Binding Plugin is affected for storing passwords in a recoverable format. Authenticated users can recover credentials.
Vendor: Jenkins
Publish Date: 2019-19-07 Last Update Date: 2019-26-07
CVSS Score 7.2
ID: CVE-2019-1010155
Title: D-Link DSL-2750U Multiple Authentication Bypass Vulnerabilities
Description: D-Link DSL-2750U is exposed to multiple authentication bypass vulnerabilities. An attacker can exploit these issues to bypass authentication mechanism and perform unauthorized actions.
Vendor: Oracle
Publish Date: 2019-23-07 Last Update Date: 2019-24-07
CVSS Score 6.4
