Trends
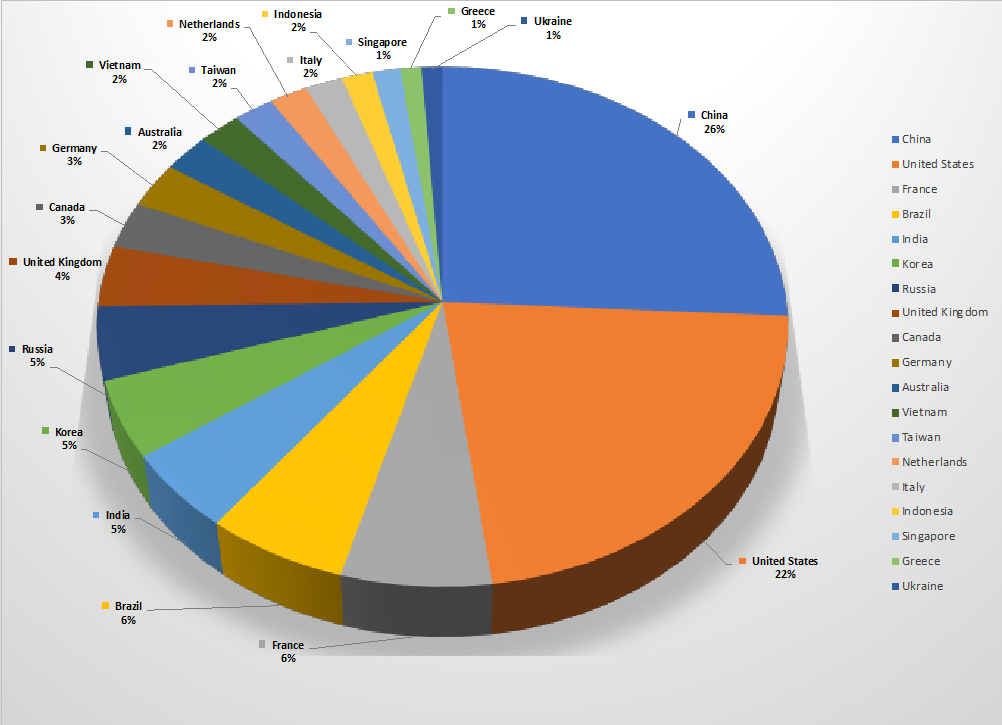
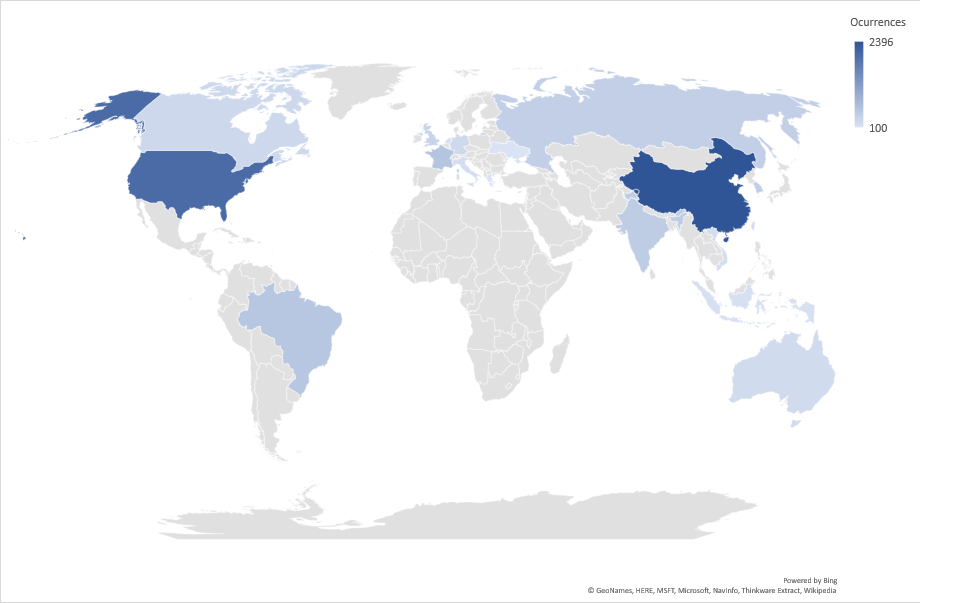
- The top attacker country was China with 2396 unique attackers (25.87%)
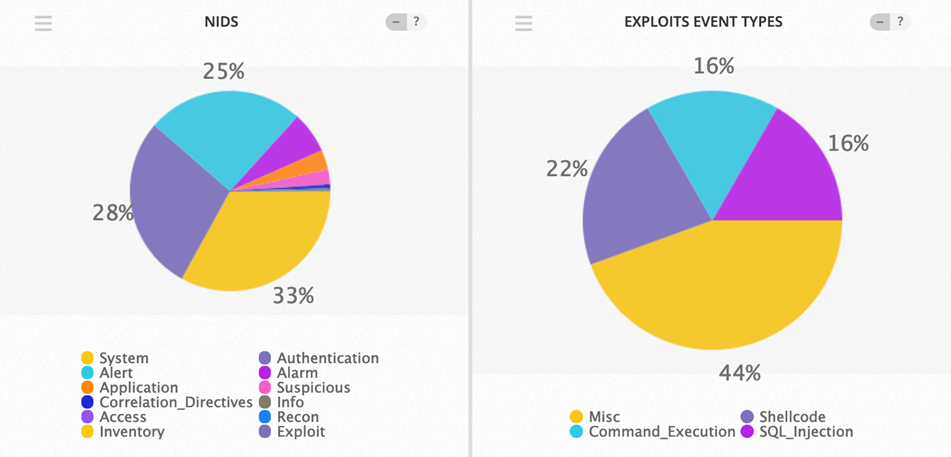
- The top Exploit event was Miscellaneous with 44% of occurrences
Top Attacker by Country
| Country | Occurrences | Percentage |
|---|---|---|
| China | 2396 | 25.87% |
| United States | 2040 | 22.03% |
| France | 597 | 6.45% |
| Brazil | 560 | 6.05% |
| India | 462 | 4.99% |
| Korea | 444 | 4.79% |
| Russia | 421 | 4.55% |
| United Kingdom | 352 | 3.80% |
| Canada | 270 | 2.92% |
| Germany | 264 | 2.85% |
| Australia | 223 | 2.41% |
| Vietnam | 202 | 2.18% |
| Taiwan | 190 | 2.05% |
| Netherlands | 182 | 1.97% |
| Italy | 180 | 1.94% |
| Indonesia | 146 | 1.58% |
| Singapore | 132 | 1.43% |
| Greece | 101 | 1.09% |
| Ukraine | 100 | 1.08% |
Threat Geo-location
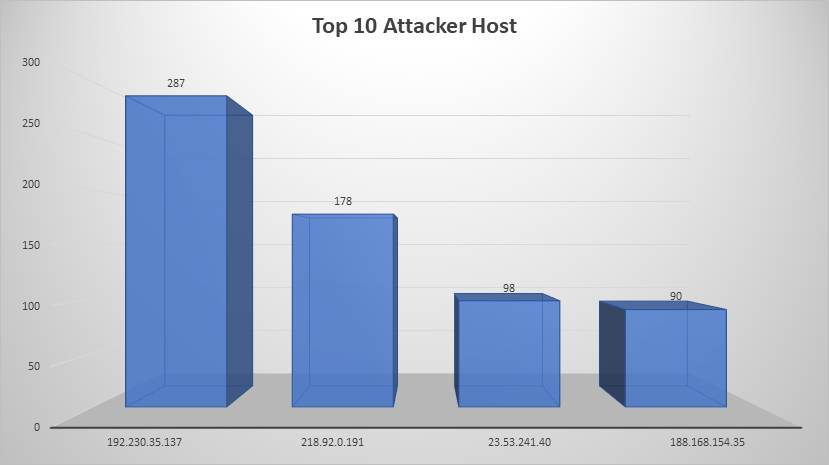
Top Attacking Hosts
| Host | Occurrences |
|---|---|
| 194.230.35.137 | 287 |
| 218.92.0.191 | 178 |
| 23.53.241.40 | 98 |
| 188.168.154.35 | 90 |
Top Network Attackers
| Origin AS | Announcement | Description |
|---|---|---|
| AS53889 | 192.230.32.0/19 | Micfo, LLC |
| AS4134 | 218.92.0.0/16 | CHINANET Jiangsu Province Network |
| AS35994 | 23.32.0.0/11 | Akamai Technologies, Inc. |
| AS15774 | 188.168.0.0/16 | Closed Joint Stock Company TransTeleCom |
Exploit Event Types and Top Event NIDS
Top Alarms
| Type of Alarm | No. of Occurrences |
|---|---|
| Red Piranha HIDS: IDS Event | 3073 |
| Suspicious Behaviour - SSH | 276 |
| OTX Indicators of Compromise - PULSE | 147 |
| Stored Procedure Access - Attack | 55 |
| Attack Tool Detected - Attack | 45 |
| Bruteforce Authentication - SSH | 43 |
| WebServer Attack - Attack | 39 |
| Network Discovery - Scan SSH | 32 |
| Hacking Tool - Squid Event | 8 |
Comparison from last week
| Type of Alarm | No. of Occurrences |
|---|---|
| Red Piranha HIDS: IDS Event | 1536 |
| OTX Indicators of Compromise - PULSE | 109 |
| Network Discovery - Scan SSH | 71 |
| Database Attack - Stored Procedure Access - Attack | 56 |
| Attack Tool Detected - Attack | 19 |
| System Compromise - Suspicious Behaviour - SSH | 14 |
| Delivery & Attack - WebServer Attack - Attack | 10 |
| Delivery & Attack - Network Discovery - IDS Event | 9 |
| Delivery & Attack - Bruteforce Authentication - SSH | 4 |
| Environmental Awareness - Trojan infection - IDS Event | 2 |
CVE
This is a list of recent vulnerabilities for which exploits are available.
ID: CVE-2019-9948
Title: Python urllib Security Bypass Vulnerability
Vendor: Python
ID: CVE-2019-9956
Title: ImageMagick Stack Buffer Overflow Vulnerability
Vendor: ImageMagick
ID: CVE-2019-9797, CVE-2019-9798, CVE-2019-9799, CVE-2019-9802, CVE-2019-9803, CVE-2019-9804, CVE-2019-9805, CVE-2019-9806, CVE-2019-9807, CVE-2019-9809, CVE-2019-9808, CVE-2019-9789
Title: Mozilla Firefox Multiple Security Vulnerabilities
Vendor: Mozilla Firefox
ID: CVE-2019-9970
Title: Signal Homograph Domain Spoofing Vulnerability
Vendor: Signal
ID: CVE-2019-9977
Title: Tesla Unspecified Arbitrary Code Execution Vulnerability
Vendor: Tesla
ID: CVE-2018-18065
Title: Net-SNMP Remote Denial of Service Vulnerability
Vendor: Net-SNMP
ID: CVE-2019-9020, CVE-2019-9021, CVE-2019-9023, CVE-2019-9024
Title: PHP Information Disclosure and Heap Buffer Overflow Vulnerabilities
Vendor: PHP
ID: CVE-2019-5787, CVE-2019-5788, CVE-2019-5789
Title: Google Chrome Use After Free Vulnerability
Vendor: Google
Vulnerabilities
Cisco IOS and IOS XE Software CVE-2019-1762 Local Information Disclosure Vulnerability
2019-03-27
securityfocus.com/bid/107594
Cisco IOS XE Software CVE-2019-1743 Arbitrary File Upload Vulnerability
2019-03-27
securityfocus.com/bid/107591
Cisco IOS XE Software CVE-2019-1754 Remote Privilege Escalation Vulnerability
2019-03-27
securityfocus.com/bid/107590