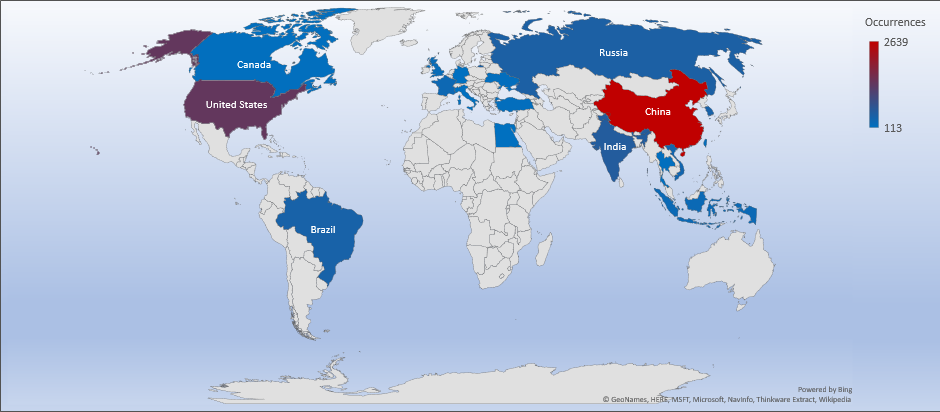
Trends
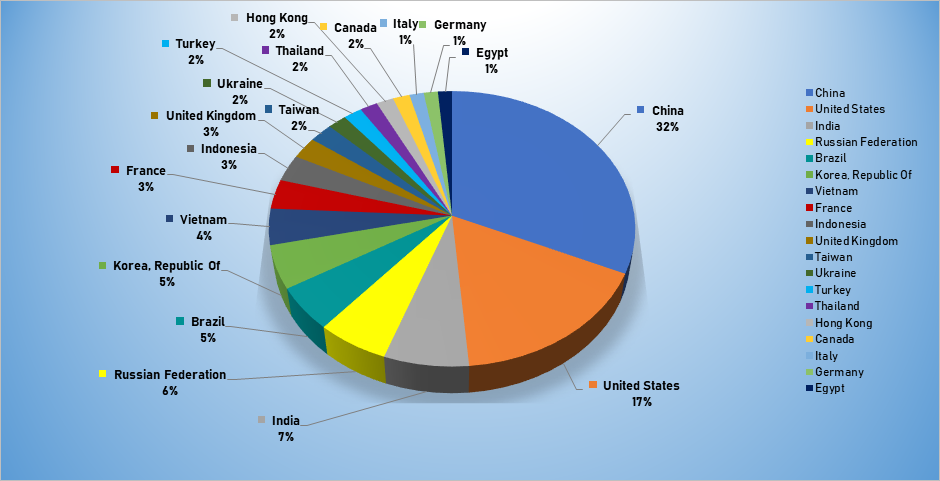
- The top attacker country was China with 2639 unique attackers (31%)
- The top Exploit event was Authentication with 60% of occurrences.
- The top Trojan C&C server detected was Trickbot with 43 instances detected.
Top Attacker by Country
| Country | Occurrences | Percentage |
|---|---|---|
| China | 2639 | 31.71% |
| United States | 1409 | 16.93% |
| India | 571 | 6.86% |
| Russian Federation | 483 | 5.80% |
| Brazil | 431 | 5.18% |
| Korea | 424 | 5.09% |
| Vietnam | 353 | 4.24% |
| France | 289 | 3.47% |
| Indonesia | 262 | 3.15% |
| United Kingdom | 213 | 2.56% |
| Taiwan | 190 | 2.28% |
| Ukraine | 151 | 1.81% |
| Turkey | 149 | 1.79% |
| Thailand | 142 | 1.71% |
| Hong Kong | 139 | 1.67% |
| Canada | 135 | 1.62% |
| Italy | 115 | 1.38% |
| Germany | 114 | 1.37% |
| Egypt | 113 | 1.36% |
Threat Geo-location
Top Attacking Hosts
| Host | Occurrences |
|---|---|
| 218.92.0.190 | 47 |
| 80.82.77.139 | 21 |
| 112.85.42.171 | 20 |
| 112.85.42.187 | 14 |
Top Network Attackers
| Origin AS | Announcement | Description |
|---|---|---|
| AS4134 | 218.92.0.0/16 | CHINANET Jiangsu Province Network |
| AS202425 | 80.82.77.0/24 | Red de Servicios IP |
| AS4837 | 112.80.0.0/13 | China Unicom Jiangsu Province Network |
Top Event NIDS and Exploits
Top Alarms
| Type of Alarm | Occurrences |
|---|---|
| Bruteforce Authentication | 808687 |
| Intrusion Detection | 33223 |
| Network Anomaly | 1721987 |
Comparison from last week
| Type of Alarm | Occurrences |
|---|---|
| Bruteforce Authentication | 2035 |
| Intrusion Detection | 2879 |
| Network Discovery | 20 |
Remote Access Trojan C&C Servers Found
| Name | Number Discovered | Location |
|---|---|---|
| Azorult | 18 | 167.86.123.249, 185.212.130.104, 185.212.130.17, 185.212.130.34, 185.212.130.39, 185.212.130.50, 185.212.130.54, 185.212.130.56, 185.212.130.69, 185.212.130.70, 185.212.130.74, 185.212.130.78, 185.212.130.8, 185.212.130.87, 194.67.90.231, 45.86.180.5, 93.189.43.82, babillonngloball.xyz |
| Betabot | 1 | 111.90.142.117 |
| CryptBot | 2 | 185.151.245.99 , 195.133.144.68 |
| Heodo | 22 | 133.167.80.63, 144.76.62.10, 173.249.157.58, 179.12.170.88, 181.230.126.152, 181.47.235.26, 187.155.233.46, 189.253.27.123, 198.199.114.69, 198.199.88.162, 201.184.105.242, 201.250.11.236, 203.99.188.203, 213.138.100.98, 216.98.148.181, 23.239.29.211, 24.45.195.162, 68.183.190.199, 70.32.94.58, 86.98.25.30, 91.109.5.28, 91.83.93.105 |
| Keitaro | 2 | 5.188.231.211, 5.8.88.124 |
| LokiBot | 3 | 194.67.206.57, 47.254.66.50, 91.211.245.184 |
| PredatorTheThief | 6 | 129.226.56.28, 193.124.186.171, 5.188.60.6, 5.8.88.64, 91.243.80.13, 45.128.184.2 |
| TrickBot | 43 | 104.244.76.156, 107.172.248.84, 178.252.26.235, 185.142.99.61, 185.14.31.109, 185.164.32.113, 185.222.202.223, 185.222.202.62, 185.244.150.142, 185.251.38.165, 185.79.243.37, 188.137.81.201, 194.5.250.79, 194.5.250.83, 194.5.250.89, 194.5.250.94, 195.123.220.88, 195.123.247.99, 198.24.134.7, 198.98.51.83, 199.195.254.138, 212.22.75.94, 212.80.216.58, 23.94.233.194, 31.202.132.155, 31.214.138.207, 38.132.99.147, 45.142.213.58, 45.66.11.116, 45.80.148.30, 46.21.153.17, 46.21.153.5, 5.185.67.137, 66.55.71.106, 66.55.71.15, 78.24.217.84, 81.177.26.27, 81.190.160.139, 85.11.116.194, 85.143.218.203, 89.25.238.170, 92.242.40.148, 94.156.144.3 |
Common Malware
| Malware Type | MD5 | Typical Filename |
|---|---|---|
Win.Trojan. | 47b97d e62ae8 b2b927 542aa5 d7f3c8 58 | qmreportupload.exe |
W32.7ACF | 4a5078 0ddb3d b16eba b57b0c a42da0 fb | xme64-2141.exe |
| W32.Coin Miner:Crypto MinerY.22 k3.1201 | 0e0255 5ede71 bc6c72 4f9f92 4320e0 20 | dllhostex.exe |
W32.Agent | e2ea31 5d9a83 e75770 53f52c 974f6a 5a | c3e530cc005583b 47322b6649ddc0d ab1b64bcf22b124a 492606763c52fb04 8f.bin |
| W32.Generic :Gen.22fz. 1201 | 799b30 f47060 ca05d8 0ece53 866e01 cc | mf2016341595.exe |
CVEs For Which Public Exploits Have Been Detected
ID: CVE-2019-11932
Title: Anchor CMS Information Disclosure Vulnerability
Vendor: Anchor CMS
Description: A double free vulnerability in the DDGifSlurp function in decoding.c in libpl_droidsonroids_gif as used in WhatsApp for Android, allows remote attackers to execute arbitrary code or cause a denial of service. By default, AnchorCMS will log errors to the "/anchor/errors.log" file in the webroot of the web application. This allows malicious users to access the error log and view potentially sensitive information.
CVSS v2 Base Score: 7.5 (AV:N/AC:L/Au:N/C:P/I:P/A:P)
ID: CVE-2019-1367
Title: Microsoft Scripting Engine Memory Corruption Vulnerability
Vendor: Microsoft
Description: A remote code execution vulnerability exists in the way that the scripting engine handles objects in memory in Internet Explorer. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. This CVE ID is unique from CVE-2019-1221.
CVSS v2 Base Score: 7.6 (AV:N/AC:H/Au:N/C:C/I:C/A:C)
ID: CVE-2019-1315
Title: Microsoft Windows Error Reporting Privilege Escalation Vulnerability
Vendor: Microsoft
Description: Microsoft Windows could allow a local authenticated attacker to gain elevated privileges on the system, caused by improper handling of hard links by the Error Reporting manager. By executing a specially-crafted program, an authenticated attacker could exploit this vulnerability to take control of the system.
CVSS v2 Base Score: 7.5 (AV:N/AC:L/Au:N/C:P/I:P/A:P)
ID: CVE-2019-16920
Title: D-Link Unauthenticated Command-Injection Vulnerability
Vendor: D-Link
Description: The vulnerability exists in the latest firmware for the DIR-655, DIR-866L, DIR-652 and DHP-1565 products, which are Wi-Fi routers. The vulnerability exists due to improper sanitization of arbitrary commands that are executed by the native command-execution function. An attacker who successfully triggers the command injection could achieve full system compromise.
Fortinet's FortiGuard Labs has discovered an unauthenticated remote code execution vulnerability in D-Link products.
CVSS v2 Base Score: 10.0 (AV:N/AC:L/Au:N/C:C/I:C/A:C)
ID: CVE-2019-17132
Title: vBulletin Authenticated Remote Code Execution Vulnerability
Vendor: vBulletin
Description: A remote code execution vulnerability exist in User input passed through the "data[extension]" and "data[filedata]" parameters to the "ajax/api/user/updateAvatar" endpoint, that is not properly validated before being used to update users avatars. This can be exploited to inject and execute arbitrary PHP code. Successful exploitation of this vulnerability requires the "Save Avatars as Files" option to be enabled (disabled by default).
CVSS v2 Base Score: 6.4 (AV:N/AC:L/Au:N/C:P/I:N/A:P)
ID: CVE-2019-4013
Title: IBM Bigfix Platform Arbitrary File Upload Vulnerability
Vendor: IBM
Description: IBM BigFix Platform could allow any authenticated user to upload any file to any location on the server with root privileges. This results in code execution on underlying system with root privileges. An attacker can for example upload script file on the web server and execute it by sending GET request.
CVSS v2 Base Score: 9.0 (AV:N/AC:L/Au:S/C:C/I:C/A:C)