
Trends
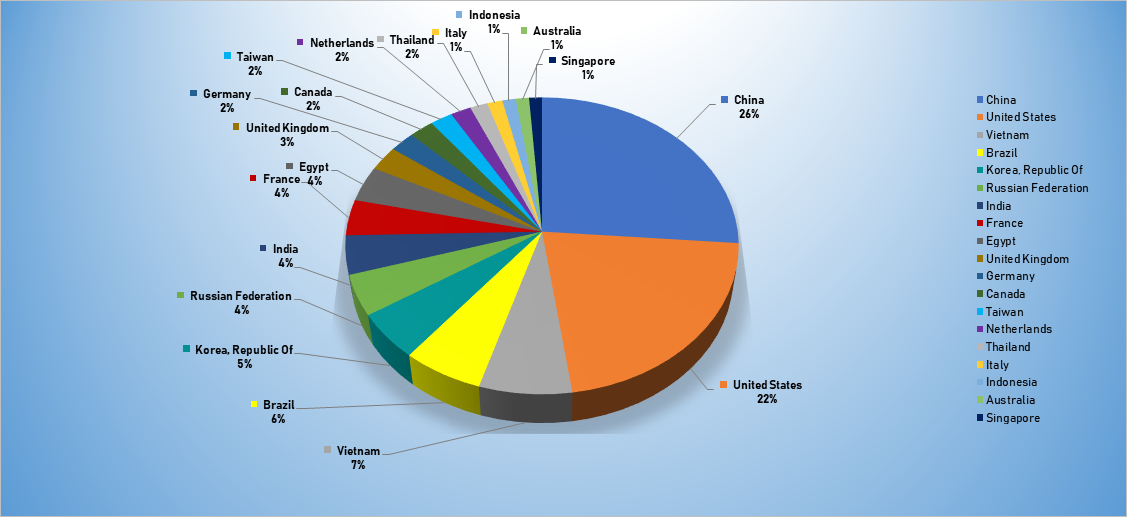
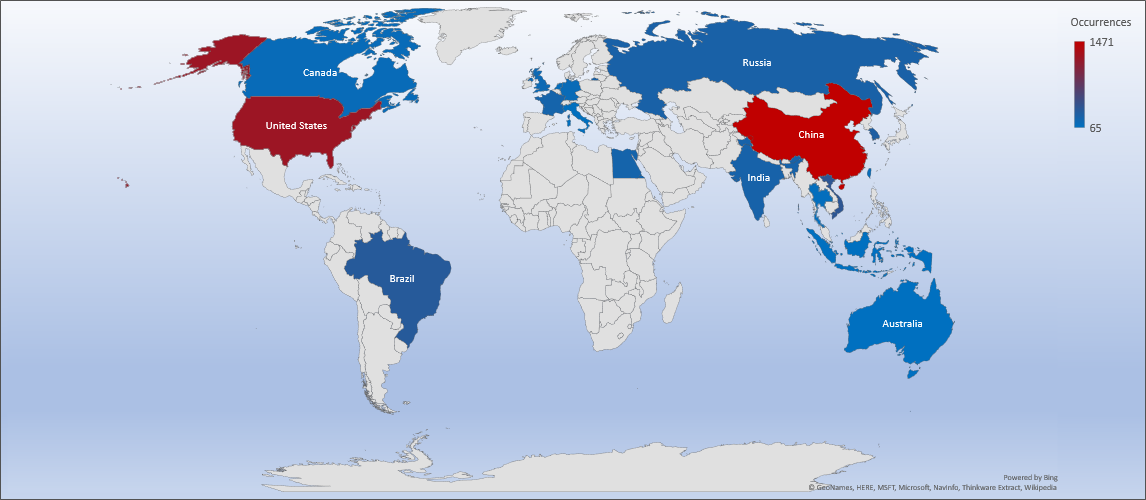
- The top attacker country was China with 1471 unique attackers (26%).
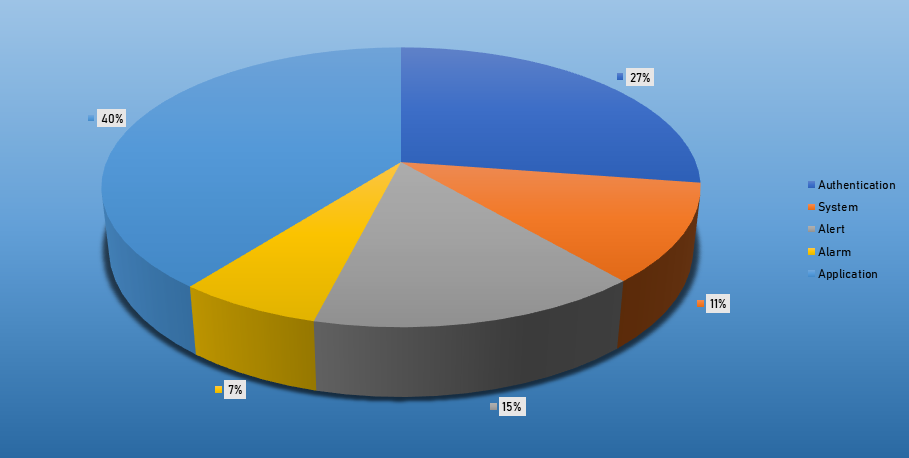
- The top Exploit event was Authentication with 25% of occurrences.
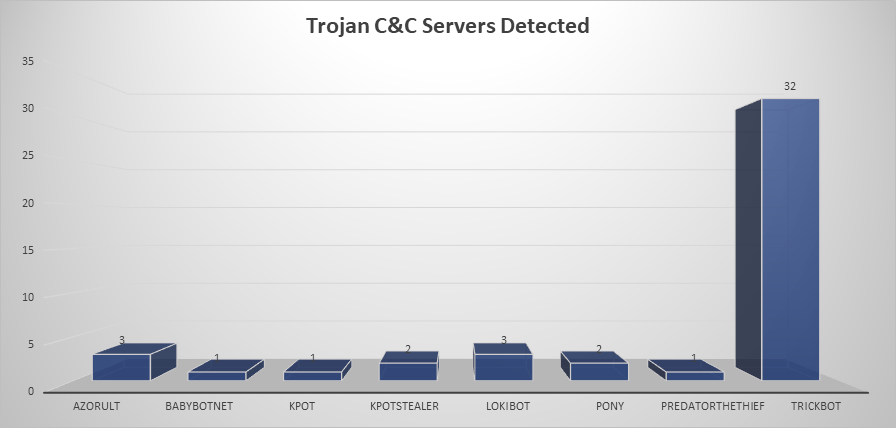
- The top Trojan C&C server detected was TrickBot with 32 instances detected.
Top Attacker by Country
| Country | Occurrences | Percentage |
|---|---|---|
| China | 1471 | 26.24% |
| United States | 1206 | 21.51% |
| Vietnam | 391 | 6.97% |
| Brazil | 341 | 6.08% |
| Republic of Korea | 287 | 5.12% |
| Russian Federation | 249 | 4.44% |
| India | 237 | 4.23% |
| Egypt | 218 | 3.89% |
| United Kingdom | 152 | 2.71% |
| Germany | 128 | 2.28% |
| Canada | 124 | 2.21% |
| Taiwan | 113 | 2.02% |
| Netherlands | 104 | 1.86% |
| Thailand | 89 | 1.59% |
| Italy | 77 | 1.37% |
| Indonesia | 68 | 1.21% |
| Australia | 67 | 1.20% |
| Singapore | 65 | 1.16% |
Threat Geo-location
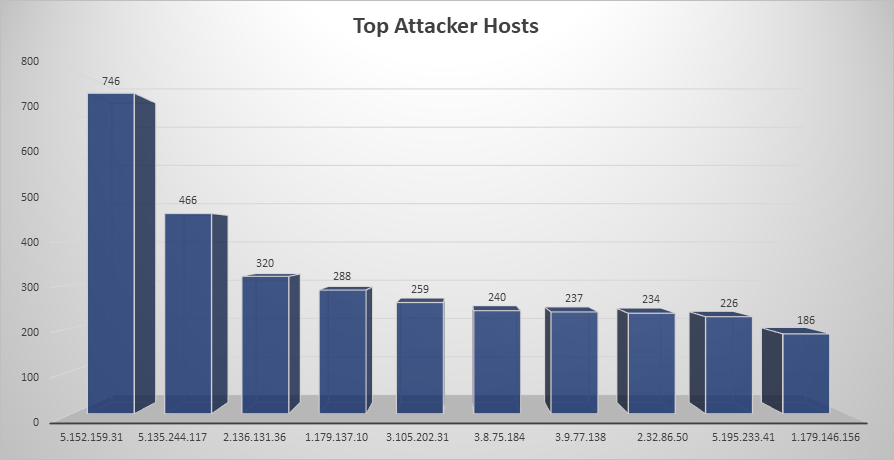
Top Attacking Hosts
| Host | Occurrences |
|---|---|
| 5.152.159.31 | 746 |
| 5.135.244.117 | 466 |
| 2.136.131.36 | 320 |
| 1.179.137.10 | 288 |
| 3.105.202.31 | 259 |
| 3.8.75.184 | 240 |
| 3.9.77.138 | 237 |
| 2.32.86.50 | 234 |
Top Network Attackers
| Origin AS | Announcement | Description |
|---|---|---|
| AS199026 | 5.152.159.0/24 | alternatYva S.r.l. |
| AS16276 | 5.135.0.0/16 | OVH SAS |
| AS3352 | 2.136.0.0/16 | Red de servicios IP |
Top Event NIDS and Exploits
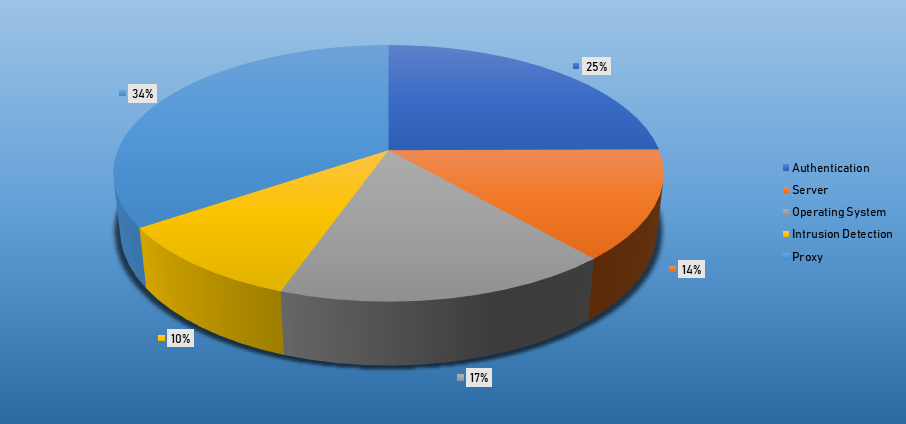
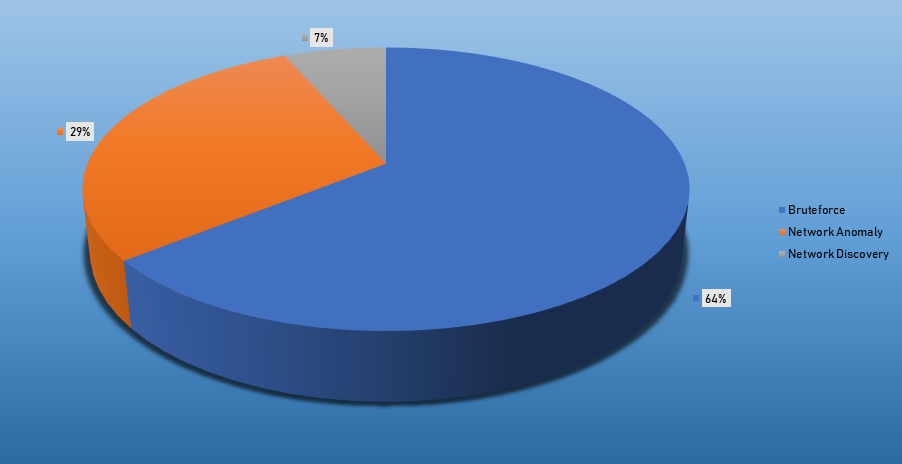
Top Alarms
| Type of Alarm | Occurrences |
|---|---|
| Bruteforce Authentication | 2294 |
| Network Anomaly | 1463 |
| Network Discovery | 324 |
Comparison from last week
| Type of Alarm | Occurrences |
|---|---|
| Bruteforce Authentication | 2294 |
| Network Anomaly | 2695 |
| Network Discovery | 8 |
Remote Access Trojan C&C Servers Found
| Name | Number Discovered | Location |
|---|---|---|
| Azorult | 3 | 185.213.211.34, 194.67.78.6, 82.202.173.113 |
| BabyBotNet | 1 | 77.222.62.31 |
| KPOT | 1 | 5.188.231.105 |
| KpotStealer | 2 | 47.88.102.244, 8.209.72.105 |
| LokiBot | 3 | 104.24.122.167, 104.27.157.100, 194.67.78.6 |
| Pony | 2 | 104.144.198.27, 116.0.23.168 |
| PredatorTheThief | 1 | 31.184.196.206 |
| TrickBot | 32 | 107.155.137.12, 107.160.141.53, |
Common Malware
| Malware Type | MD5 | Typical Filename |
|---|---|---|
Win.Trojan. | 47b97de | qmreportupload.exe |
W32.9A08 | 7a6f7f93 | DHL Scan File.img |
W32.7ACF | 4a50780 ddb3db1 6ebab57 b0ca42 da0fb | xme64-2141.exe |
W32.1755 | c785a8b 0be77a2 16a5223 c41d8dd 937f | cslast.gif |
| W32.093C C39350-100. SBX.TG | 3c7be1d be9eecfc 73f4476b f18d1df3f | sayext.gif |
CVEs For Which Public Exploits Have Been Detected
ID: CVE-2019-0708
Title: Microsoft Remote Desktop Services Remote Code Execution Vulnerability
Vendor: Microsoft
Description: A remote code execution vulnerability exists in Remote Desktop Services – formerly known as Terminal Services – when an unauthenticated attacker connects to the target system using RDP and sends specially crafted requests. This vulnerability is pre-authentication and requires no user interaction. An attacker who successfully exploited this vulnerability could execute arbitrary code on the target system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
CVSS v2 Base Score: 10.0 (AV:N/AC:L/Au:N/C:C/I:C/A:C)
ID: CVE-2019-12643
Title: Cisco IOS XE REST API Container Software Authentication Bypass Vulnerability
Vendor: Cisco
Description: This vulnerability resides in the Cisco REST API virtual service container, however, it affects devices running Cisco IOS XE Software when exploited. A successful exploit could allow the attacker to obtain the token-id of an authenticated user. This token-id could be used to bypass authentication and execute privileged actions through the interface of the REST API virtual service container on the affected Cisco IOS XE device. The security issue is tracked as CVE-2019-12643 and has received a maximum severity rating score of 10 based on CVSS v3 Scoring system.
CVSS v2 Base Score: 10.0 (AV:N/AC:L/Au:N/C:C/I:C/A:C)
ID: CVE-2019-1663
Title: Cisco Routers Remote Command Execution Vulnerability
Vendor: Cisco
Description: A vulnerability in the web-based management interface of the Cisco RV110W Wireless-N VPN Firewall, Cisco RV130W Wireless-N Multifunction VPN Router, and Cisco RV215W Wireless-N VPN Router could allow an unauthenticated, remote attacker to execute arbitrary code on an affected device. The vulnerability is due to improper validation of user-supplied data in the web-based management interface. A remote attacker can exploit this issue to execute arbitrary commands on the host operating system with escalated privileges.
CVSS v2 Base Score: 10.0 (AV:N/AC:L/Au:N/C:C/I:C/A:C)
ID: CVE-2019-1622
Title: Cisco Data Center Network Manager Information Disclosure Vulnerability
Vendor: Cisco
Description: A vulnerability in the web-based management interface of Cisco Data Center Network Manager (DCNM) could allow an unauthenticated, remote attacker to retrieve sensitive information from an affected device. The vulnerability is due to improper access controls for certain URLs on affected DCNM software. An attacker could exploit this vulnerability by connecting to the web-based management interface of an affected device and requesting specific URLs. A successful exploit could allow the attacker to download log files and diagnostic information from the affected device.
CVSS v2 Base Score: 5.0 (AV:N/AC:L/Au:N/C:P/I:N/A:N)
ID: CVE-2019-1935
Title: Cisco UCS Director Unauthenticated Remote Access Vulnerability
Vendor: Cisco
Description: A vulnerability in Cisco Integrated Management Controller (IMC) Supervisor, Cisco UCS Director, and Cisco UCS Director Express for Big Data could allow an unauthenticated, remote attacker to log in to the CLI of an affected system by using the SCP User account (scpuser), which has default user credentials. The vulnerability is due to the presence of a documented default account with an undocumented default password and incorrect permission settings for that account. Due to several coding errors, it is possible for an unauthenticated remote attacker with no privileges to bypass authentication and abuse a password change function to inject arbitrary commands and execute code
as root. An attacker could exploit this vulnerability by using the account to log in to an affected system. A successful exploit could allow the attacker to execute arbitrary commands with the privileges of the scpuser account.
CVSS v2 Base Score: 10.0 (AV:N/AC:L/Au:N/C:C/I:C/A:C)
