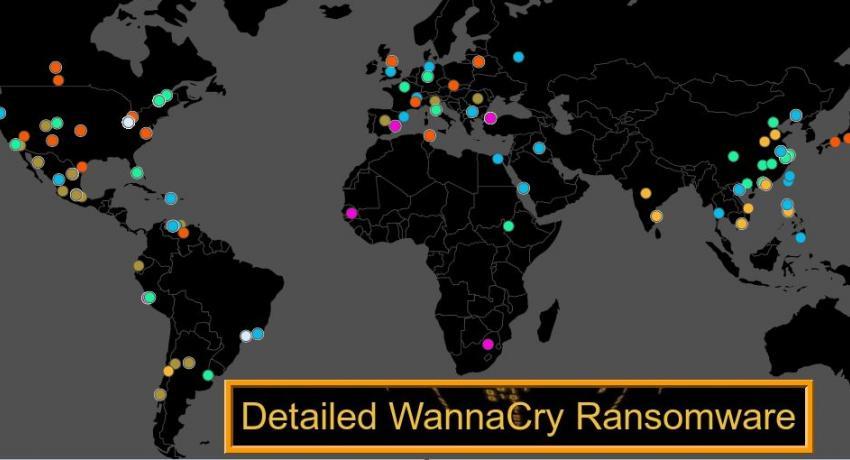
Reported to be one of the biggest Ransomware outbreak in recent history, approximately 74 countries have been targeted affecting various organisation and critical infrastructures. The infection encrypts vital database and denies access to it until a Ransom is paid to regain access. Experts believe that the Ransomware nicknamed as WannaCry is being spread using an exploitation tool called the Eternal Blue. This exploitation tool was also described and exposed in detail by the WikiLeaks in Vault 7 (a substantial collection of material about CIA activities obtained by WikiLeaks).
Update*
Since there's much confusion about this - it's an SMB worm. There's no email.
After infecting a lot of systems in Europe and Asia new infections seems to drop off. The reason infections are dropping off - it contained a kill switch, that was activated before the US woke up.
#WannaCry propagation payload contains previously unregistered domain, execution fails now that domain has been sinkholed
Also Read: Recent Shadowbrokers dump exposes over 3 million systems and the number is climbing
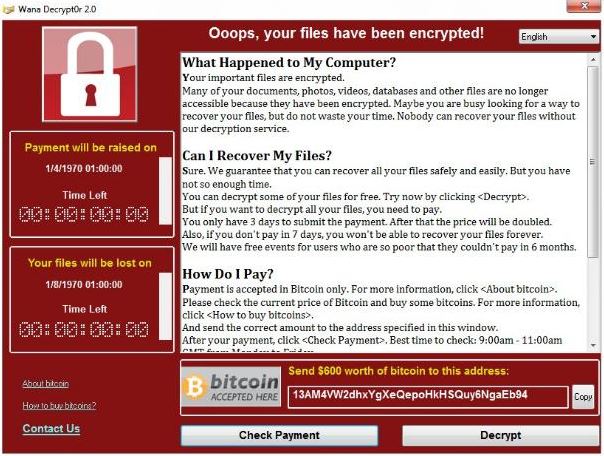
Message displayed on the computers affected by WannaCry Ransomeware
Analysts have also verified that the Ransomware outbreak could have been dealt with more effectively given the fact that vulnerable systems were updated inline with the patches released by Microsoft on March 14, 2017. The security bulletin published by the software and hardware giant shared detailed insights on the critical nature of certain vulnerabilities that could allow remote code execution similar to what the WannaCry Ransomware is using through Server Message Block.
WannaCry|WannaDecrypt0r NSA-Cybereweapon-Powered Ransomware Worm
- Virus Name: WannaCrypt, WannaCry, WanaCrypt0r, WCrypt, WCRY
- Vector: All Windows versions before Windows 10 are vulnerable if not patched for MS-17-010. It uses EternalBlue MS17-010 to propagate.
- Ransom: between $300 to $600. There is code to 'rm' (delete) files in the virus. Seems to reset if the virus crashes.
- Backdooring: The worm loops through every RDP session on a system to run the ransomware as that user. It also installs the DOUBLEPULSAR backdoor. (source: malwarebytes)
- Kill switch: If the website www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com is up the virus exits instead of infecting the host. (source: malwarebytes). This domain has been sinkholed, stopping the spread of the worm.
SECURITY BULLETIN AND UPDATES HERE: Read here
Wanacrypt0r Blog: Read here
Infections
- NHS (uk) turning away patients, unable to perform x-rays.
- Telefonica (spain)
- FedEx (us)
- University of Waterloo (us)
- Russia interior ministry & Megafon (russia)
- Сбера bank (russia)
- Shaheen Airlines (india, claimed on twitter)
- Train station in frankfurt (germany)
- Neustadt station (germany)
- the entire network of German Rail seems to be affected (@farbenstau)
- Russian Railroads (RZD), VTB russian bank
- Portugal Telecom
Malware samples
- hxxps://www.hybrid-analysis.com/sample/ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa?environmentId=100
- hxxps://transfer.sh/PnDIl/CYBERed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.EXE
- hxxps://transfer.sh/ZhnxR/CYBER1be0b96d502c268cb40da97a16952d89674a9329cb60bac81a96e01cf7356830.EXE (main dll)
Binary blob in PE crypted with pass 'WNcry@2ol7', credits to ens!
Informative Tweets
- Sample released by ens: twitter.com/the_ens
- Onion C&Cs extracted: twitter.com/the_ens
- EternalBlue confirmed: twitter.com/kafeine
- Shell commands: twitter.com/laurilove
- Maps/stats: twitter.com/laurilove
- Core DLL: twitter.com/laurilove
- Hybrid-analysis: twitter.com/PayloadSecurity
- Impact assessment: twitter.com/CTIN_Global
- Uses DoublePulsar: twitter.com/laurilove
- Your machine is attacking others: twitter.com/hackerfantastic
- Tor hidden service C&C: twitter.com/hackerfantastic
- FedEx infected via Telefonica? twitter.com/jeancreed1
- HOW TO AVOID INFECTION: twitter.com/hackerfantastic
- More of this to come: twitter.com/hackerfantastic
- C&C hosts: twitter.com/hackerfantastic
- Crypted files will be deleted after countdown: twitter.com/laurilove
- Claim of attrib [take with salt]: twitter.com/0xSpamTech
- Track the bitcoins: twitter.com/bl4sty
- keys in pem format: twitter.com/e55db081d05f58a
Cryptography details
- encrypted via AES-128-CBC (custom implementation in the binary)
- AES key generated with a CSPRNG, CryptGenRandom
- AES key is encrypted by RSA-2048 (windows RSA implementation)
- Ransomware pubkey (the ransomware pubkey, used to encrypt the aes keys)
- DLL decryption privkey (the dll decryption privkey) the CryptImportKey() rsa key blob dumped from the DLL by blasty.
Bitcoin ransom addresses
C&C centers
- gx7ekbenv2riucmf.onion
- 57g7spgrzlojinas.onion
- xxlvbrloxvriy2c5.onion
- 76jdd2ir2embyv47.onion
- cwwnhwhlz52maqm7.onion
Languages
All language ransom messages are available.
m_bulgarian, m_chinese (simplified), m_chinese (traditional), m_croatian, m_czech, m_danish, m_dutch, m_english, m_filipino, m_finnish, m_french, m_german, m_greek, m_indonesian, m_italian, m_japanese, m_korean, m_latvian, m_norwegian, m_polish, m_portuguese, m_romanian, m_russian, m_slovak, m_spanish, m_swedish, m_turkish, m_vietnamese
Close Look at Some Countries and Organisations Affected by WannaCry Ransomware
United Kingdom
The cyberattack crippled the overall functioning of NHS hospitals across England. General practitioners were not able to access patient data which describes the medical history of a patient. This information is vital while treating a patient as it relates to various health related complications a patient went through in the past. As per reports released by BBC (British Broadcasting Network), it understands that there are about 39 hospitals that has been hit by the cyber attack.
Spain
As per some unconfirmed reports the outbreak was first detected in Spain and for there on it spread worldwide. The country’s top brass is said to have given a go ahead to activate a special protocol that is designed to protect critical infrastructure across the nation. The National Center for the Protection of Critical Infrastructure (CNPIC) which does risk analysis of the strategic sectors in Spain has stated that it is working closely with over 100 providers of energy, transportation, telecommunications and financial services. The worst hit are the computers of the employees belonging to the Ministry of Energy, Tourism and Digital Agenda.
Russia
The WannaCry Ransomware is said to have affected about 1000 computers at Russia’s Interior Ministry which run on windows operating system. Interior Ministry spokesperson Irina Volk said, “The servers of the ministry have not been affected, Volk added, saying it’s operated by different systems for Russia-developed data processing machines.’’
Russian Telecom giant Megafon has also reported that more than half of its computers have been affected by the Ransomware. Pyotr Lidov, a spokesman for Megafon, said that they were able to restore all the affected computers at the call centers. However the regional offices remained closed all day long after the attacks.
U.S
FedEx an American multinational courier delivery services company headquartered in Memphis did release an official statement which pointed out towards the fact that they were experiencing interference with some of their Windows-based systems caused by the Ransomware. The impact of the cyberattack is still being evaluated on its global services and deliveries system.

Get a security risk assessment for your networks today!
