| New Threat Detection Added | 2 (BluStealer Malware and CHAOS RAT) |
| New Threat Protections | 200 |
Weekly Detected Threats
The following threats were added to Crystal Eye XDR this week:
Threat name: | BluStealer Malware | ||||||||||||||||||
BluStealer is a lurking information-stealing malware with a knack for customisation. First appearing in 2021, it's known for snatching login credentials, credit card info, and even cryptocurrency wallets. This stealer uses a two-part system: a Visual Basic core that loads separate payloads written in C#. This lets attackers tailor BluStealer's thievery for each victim. Devious yet not picky, BluStealer can target both personal and business devices. It hunts for browser passwords, FTP logins, and snatches crypto wallets, info most people wouldn't store on a work computer. Frighteningly, BluStealer can mask itself, evading detection by some security software. | |||||||||||||||||||
Threat Protected: | 02 | ||||||||||||||||||
Rule Set Type: |
| ||||||||||||||||||
Class Type: | Trojan-activity | ||||||||||||||||||
Kill Chain: |
| ||||||||||||||||||
Threat name: | CHAOS RAT | |||||||||||||||||||||
CHAOS RAT, though dramatic in name, is a free, open-source tool with a double-edged sword. On the positive side, it functions as a legitimate Remote Administration Tool (RAT) for system administrators. It lets them remotely control computers, perform tasks like file transfers and screenshots, and gather basic system information. This can be useful for IT support or managing remote devices. However, the open-source nature means anyone can access and potentially misuse CHAOS RAT. In the wrong hands, it can turn malicious. Hackers could use it to establish remote connections to victims' machines, steal data, or launch further attacks. | ||||||||||||||||||||||
Threat Protected: | 01 | |||||||||||||||||||||
Rule Set Type: |
| |||||||||||||||||||||
Class Type: | Trojan-activity | |||||||||||||||||||||
Kill Chain: |
| |||||||||||||||||||||
Known exploited vulnerabilities (Week 2 - July 2024)
Threat | CVSS | Description | |
CVE-2024-23692 | 9.8 (Critical) | Rejetto HTTP File Server Improper Neutralization Vulnerability | |
CVE-2024-38080 | 7.8 (High) | Microsoft Windows Hyper-V Privilege Escalation Vulnerability | |
CVE-2024-38112 | 7.5 (High) | Microsoft Windows MSHTML Platform Spoofing Vulnerability |
For more information, please visit the Red Piranha Forum:
https://forum.redpiranha.net/t/known-exploited-vulnerabilities-catalog-2nd-week-of-july-2024/487
Updated Malware Signatures (Week 2 - July 2024)
Threat | Description | |
CoinMiner | This malicious software installs and runs cryptocurrency mining applications. | |
Trojan Miner | This malicious software installs and runs cryptocurrency mining applications. | |
Lumma Stealer | A type of malware classified as an information stealer. Its primary purpose is to steal sensitive information from infected systems, including but not limited to credentials, financial information, browser data, and potentially other personal or confidential information. |
| Ransomware Report | |
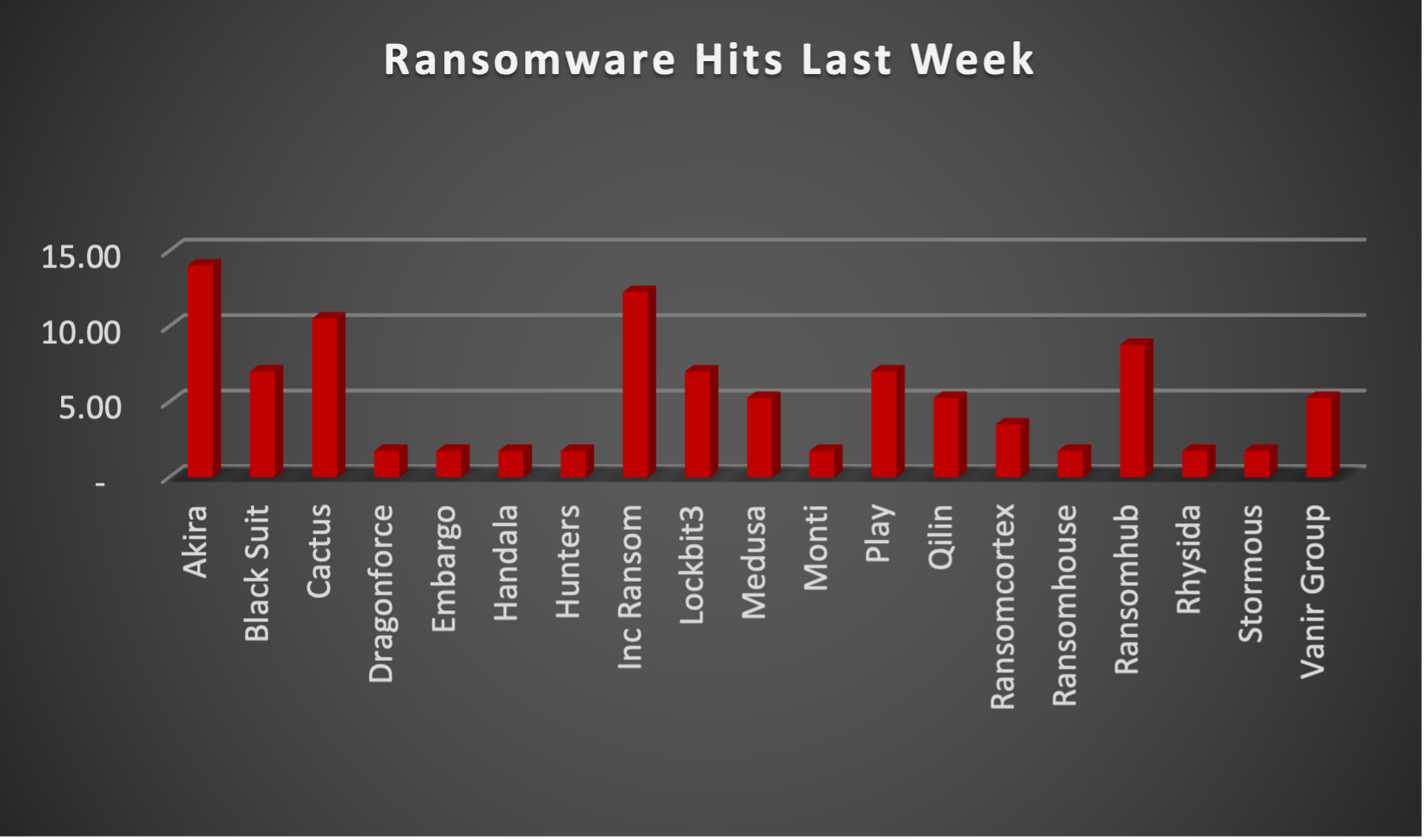
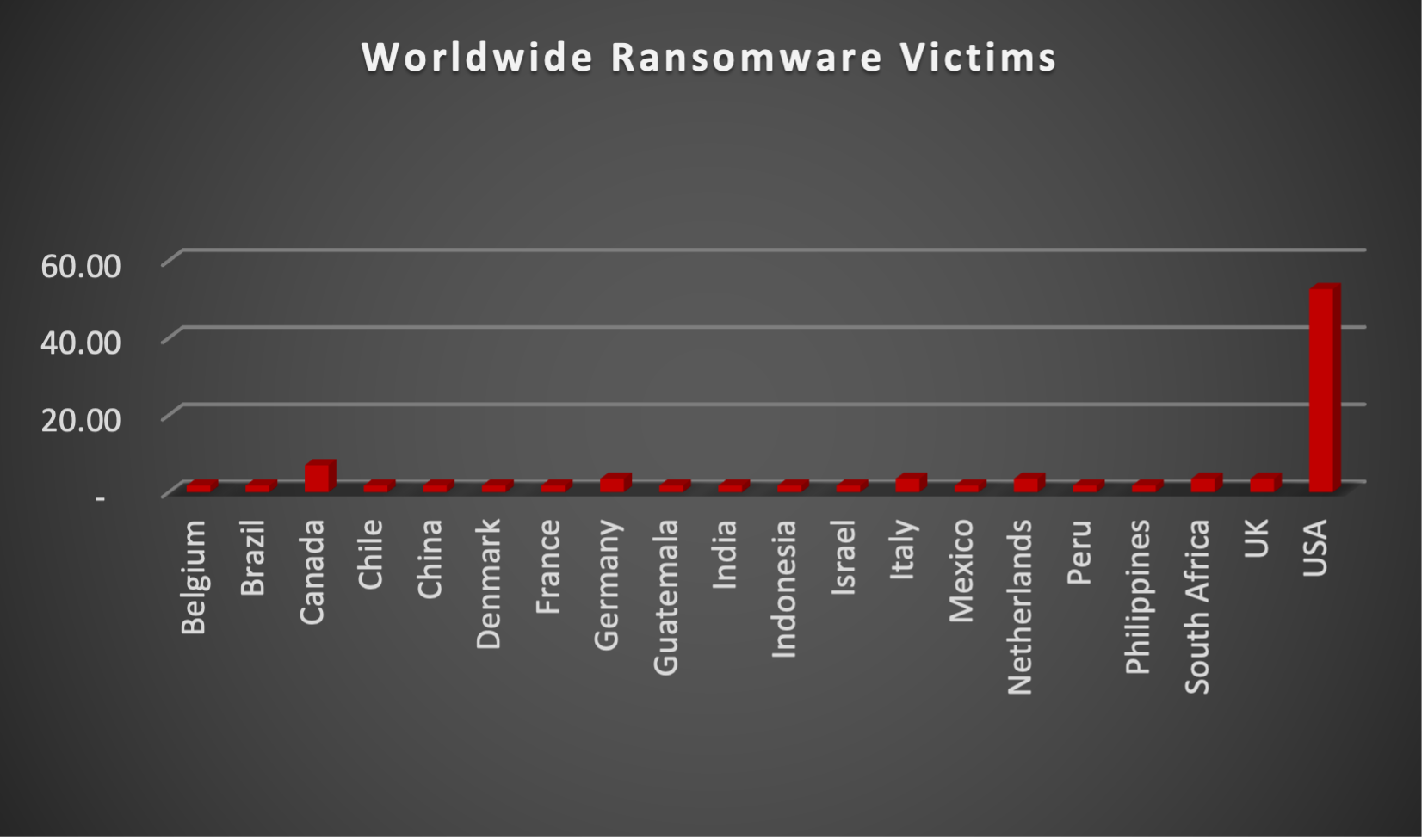
The Red Piranha Team actively collects information on organisations globally affected by ransomware attacks from various sources, including the Dark Web. In the past week alone, our team uncovered new ransomware victims and updates on previous victims across 17 industries spanning 20 countries. This underscores the widespread and indiscriminate impact of ransomware attacks, emphasising their potential to affect organisations of varying sizes and sectors worldwide. Akira ransomware group stands out as the most prolific, having updated a significant number of victims (14%) distributed across multiple countries. In comparison, Inc. Ransom ransomware updated 12% of victims, in the past week. The following list provides the victim counts in percentages for these ransomware groups and a selection of others. | |
| Name of Ransomware Group | Percentage of new Victims last week |
Akira | 14.04% |
Black Suit | 7.02% |
Cactus | 10.53% |
Dragonforce | 1.75% |
Embargo | 1.75% |
Handala | 1.75% |
Hunters | 1.75% |
Inc. Ransom | 12.28% |
7.02% | |
Medusa | 5.26% |
Monti | 1.75% |
7.02% | |
Qilin | 5.26% |
Ransomcortex | 3.51% |
Ransomhouse | 1.75% |
Ransomhub | 8.77% |
Rhysida | 1.75% |
Stormous | 1.75% |
Vanir Group | 5.26% |
Inc. Ransomware
Emerging in July 2023, Inc. Ransomware quickly carved a niche in the cybercrime landscape with its calculated approach. This malware employs a twist on the typical double extortion tactic, positioning itself as a "service" to its victims. While the exact origins of Inc. Ransomware remain unclear, security researchers suspect it may be linked to a Russian-speaking cybercriminal group.
Tactics, Techniques, and Procedures (TTPs):
Inc. Ransomware attempts to distinguish itself from its brutal counterparts by presenting a facade of offering "data recovery services" after encryption. However, this is a manipulative tactic designed to pressure victims into paying the ransom. Here's a closer look at Inc. Ransomware's tactics:
- Spear-Phishing Attacks: Unlike the ransomware strains that rely on mass phishing campaigns, Inc. targets victims with meticulously crafted spear-phishing emails. These emails appear to be from legitimate sources, such as business partners or service providers and often leverage social engineering tactics to trick recipients into clicking malicious links or downloading infected attachments.
- Exploiting Unpatched Vulnerabilities: Inc. actively seeks out unpatched vulnerabilities in software and operating systems to gain unauthorised access to networks. This reinforces the importance of keeping all software and systems updated with the latest security patches.
- Lateral Movement: Once a foothold is established on a single device, Inc. utilises various tools to move laterally across a network. This allows it to infect additional devices, escalate privileges, and potentially compromise critical systems.
- Living-off-the-Land Techniques: Similar to many malware strains, Inc. can utilise legitimate system administration tools for malicious purposes. This makes detection more challenging as these tools may appear as normal system activity.
Read more on Living-off-the-land attacks and defending against APTs. - Data Exfiltration: Before encryption, Inc. often exfiltrates sensitive data like financial records, personal information, and intellectual property. This stolen data serves as a double-edged sword. Inc. threatens to not only encrypt but also leak this data on the dark web, escalating pressure on victims.
- Deceptive "Recovery Service": Following encryption, Inc. presents victims with a ransom note disguised as a "data recovery service agreement." This facade creates a false sense of negotiation and can manipulate victims into paying the ransom, believing they are regaining access to their data.
- Strong Encryption: Despite the deceptive tactics, Inc. utilises robust encryption algorithms to render files inaccessible. Decrypting them without the attacker's key is extremely difficult, if not impossible. This effectively cripples a victim's operations until a decision is made.
A Global Reach with Focused Targets
While Inc. Ransomware exhibits a global reach, it also displays a preference for specific targets:
- Small and Medium-Sized Businesses (SMBs): SMBs are frequent targets due to their potentially less robust cybersecurity defences compared to larger enterprises. Inc.'s deceptive tactics can be particularly effective in these organisations.
- Supply Chain Attacks: There are concerns that Inc. might target vulnerabilities in software suppliers or third-party vendors to gain access to a wider network. By compromising a trusted vendor, attackers can infiltrate a larger number of victims through a single point of entry.
Leak Site: Inc. ransomware maintains a leak site on the dark web where they threaten to publish stolen data if the ransom is not paid.
Ransom Note:
The emergence of Inc. Ransomware underscores the ever-evolving landscape of cyber threats. Its focus on social engineering tactics, combined with its deceptive "recovery service" facade, highlights the need for organisations to prioritise robust cybersecurity measures and employee awareness training. Here are some crucial steps organisations can take:
- Security Awareness Training: Educate employees on identifying phishing attempts and other social engineering tactics used by attackers. Regular training can significantly reduce the risk of human error leading to breaches.
- Phishing Simulations: Conduct simulated phishing attacks to identify vulnerabilities in employee awareness and response.
- Multi-Factor Authentication (MFA): Enable MFA for all user accounts wherever possible. MFA adds an extra layer of security by requiring a second verification factor beyond just a username and password.
- Endpoint Security Solutions: Deploy endpoint security solutions that can detect and prevent malware infections at the device level. These solutions can act as a first line of defence against Inc. and other malware threats.
- Network Segmentation: Segmenting your network can limit the lateral movement of ransomware, potentially preventing it from spreading throughout your entire infrastructure.
- Incident Response Plan: Develop and regularly test an incident response plan to effectively respond.
Kill Chain:
Tactic | Technique ID | Technique Name |
Execution | T1059 | Command and Scripting Interpreter |
Discovery | T1083 T1016 T1046 T1057 T1082 T1135 | File and Directory Discovery System Network Configuration Discovery Network Service Discovery Process Discovery System Information Discovery Network Share Discovery |
Impact | T1486 T1489 T1490 | Data Encrypted for Impact Service Stop Inhibit System Recovery |
Indicators of Compromise (IOCs)
Indicators | Indicator Type | Description |
hxxp://incblog7vmuq7rktic73r4ha4j757m3ptym37tyvifzp2roedyyzzxid.onion hxxp://incapt.blog/ hxxp://incapt.su/blog/leaks hxxp://incblog6qu4y4mm4zvw5nrmue6qbwtgjsxpw6b7ixzssu36tsajldoad.onion/ blog/disclosures | URLs (Onion) | Leak Site |
fcefe50ed02c8d315272a94f860451bfd3d86fa6ffac215e69dfa26a7a5deced | Hash | Malicious File |
| |||||||||||||||||||||||||||||||||||||||||||||
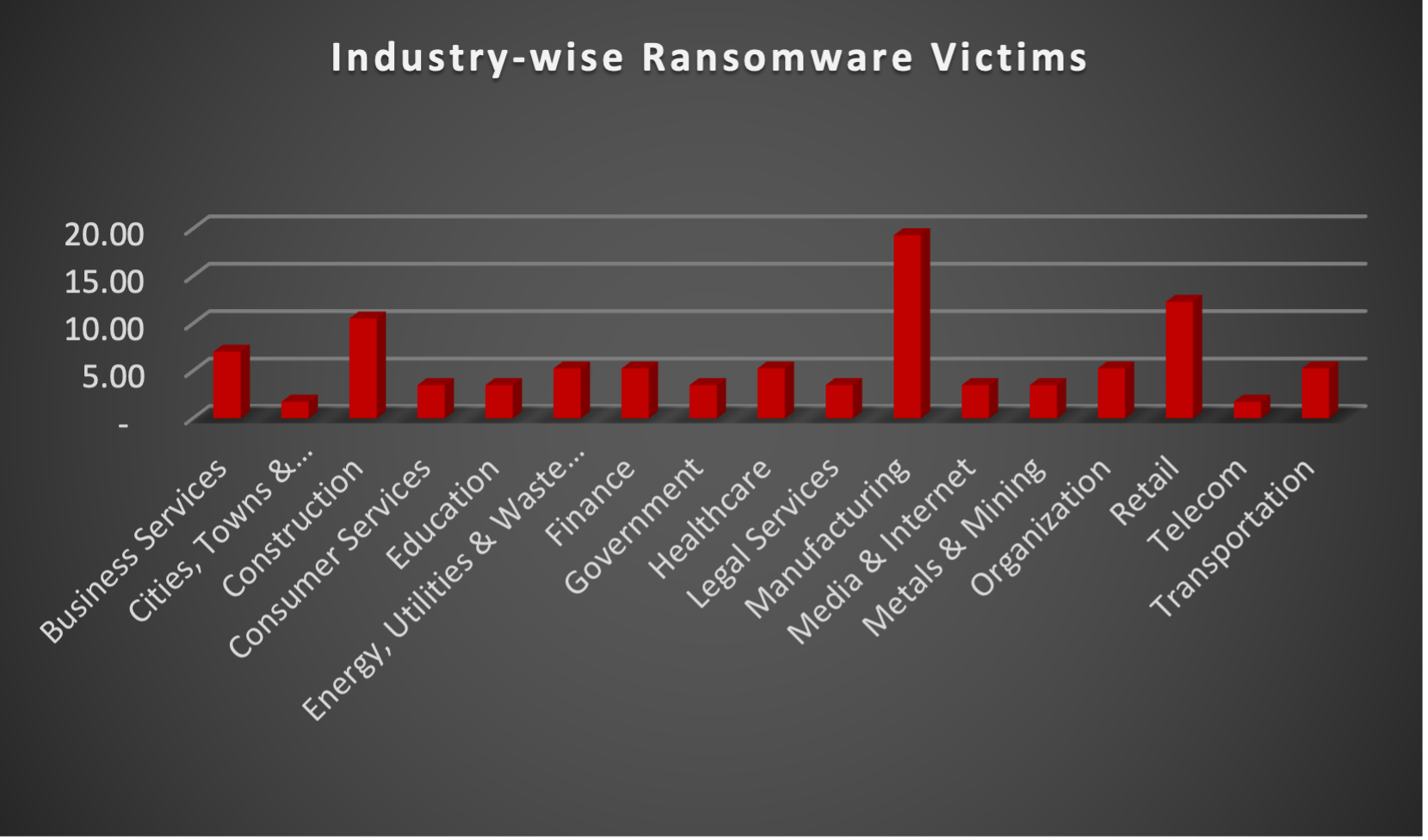
Upon further investigation, it has been identified that ransomware has left its mark on 17 different industries worldwide. Notably, Manufacturing bore the brunt of the attacks in the past week, accounting for 19% of victims. There are a few key reasons why the manufacturing sector is a prime target for ransomware groups:
- High Disruption Potential: Manufacturing relies heavily on interconnected systems and just-in-time production. A ransomware attack can grind operations to a halt, causing significant financial losses due to production delays and lost revenue. This pressure to get back online quickly can make manufacturers more willing to pay the ransom.
- Vulnerable Legacy Systems: Many manufacturers use legacy control systems (OT) that haven't been updated for security. These older systems often lack robust security features, making them easier targets for attackers to exploit.
- Limited Cybersecurity Investment: Traditionally, cybersecurity might not have been a top priority for some manufacturers compared to production efficiency. This lack of investment in security awareness training and robust security protocols leaves them exposed.
- Valuable Data: Manufacturing facilities often hold valuable intellectual property (IP) and trade secrets. Ransomware groups may not only disrupt operations but also threaten to leak this sensitive data if the ransom isn't paid.
- Success Breeds Success: The high payout potential from past attacks on manufacturers incentivises ransomware groups to continue targeting them.
The table below delineates the most recent ransomware victims, organised by industry, shedding light on the sectors grappling with the significant impact of these cyber threats.
Name of the affected Industry | Victims Count (%) |
Business Services | 7.02% |
Cities, Towns & Municipalities | 1.75% |
Construction | 10.53% |
Consumer Services | 3.51% |
Education | 3.51% |
Energy, Utilities & Waste Treatment | 5.26% |
Finance | 5.26% |
Government | 3.51% |
Healthcare | 5.26% |
Legal Services | 3.51% |
Manufacturing | 19.30% |
Media & Internet | 3.51% |
Metals & Mining | 3.51% |
Organisation | 5.26% |
Retail | 12.28% |
Telecom | 1.75% |
Transportation | 5.26% |