| New Threat Detection Added | 2 (PCRat Malware and Earth Krahang APT) |
| New Threat Protections | 347 |
Weekly Detected Threats
The following threats were added to Crystal Eye XDR this week:
Threat name: | PCRat Malware | |||||||||||||||||||||||||||
PCRat is a malware known as a Remote Access Trojan (RAT). With its source code freely available online, it is a favourite among attackers for taking control of victim's computers. PCRat is a close relative to the Gh0st RAT family, sharing similar ways of communicating with its Command-and-Control centre. This malware allows attackers to do a bunch of harmful things like stealing files, spying on keystrokes, and even launching new attacks from the infected machine. Security researchers have seen PCRat being used by malware like BabyShark, further amplifying its reach. Since the source code is public, antivirus software is constantly updated to detect and remove PCRat. | ||||||||||||||||||||||||||||
Threat Protected: | 02 | |||||||||||||||||||||||||||
Rule Set Type: |
| |||||||||||||||||||||||||||
Class Type: | Trojan-activity | |||||||||||||||||||||||||||
Kill Chain: |
| |||||||||||||||||||||||||||
Threat name: | Earth Krahang APT | |||||||||||||||||||||||||||
Earth Krahang is a sneaky Advanced Persistent Threat (APT) group that has been around since at least 2022. They target governments around the world, aiming to steal sensitive information through spying. Their favourite tactic is spear phishing, where they send emails that look legitimate but actually contain malicious attachments or links. If you click on one of these, they can exploit weaknesses in your computer's software to install nasty tools like Cobalt Strike and XDealer. These tools give them remote access to your machine, letting them steal your data and potentially use your computer to launch attacks on others. Experts think Earth Krahang might be connected to Chinese actors, but they operate independently. There is no known easy way to stop them other than good security practices. Be super careful about the emails you open, and make sure your software is always up to date with the latest security patches. | ||||||||||||||||||||||||||||
Threat Protected: | 03 | |||||||||||||||||||||||||||
Rule Set Type: |
| |||||||||||||||||||||||||||
Class Type: | Trojan-activity | |||||||||||||||||||||||||||
Kill Chain: |
| |||||||||||||||||||||||||||
Known exploited vulnerabilities (Week 2 - June 2024)
Threat | CVSS | Description | |
CVE-2024-4577 | 9.8 (Critical) | PHP-CGI OS Command Injection Vulnerability | |
CVE-2024-4610 | 5.5 (Medium) | Arm Mali GPU Kernel Driver Use-After-Free Vulnerability | |
CVE-2024-4358 | 9.8 (Critical) | Progress Telerik Report Server Authentication Bypass by Spoofing Vulnerability | |
CVE-2024-26169 | 7.8 (High) | Microsoft Windows Error Reporting Service Improper Privilege Management Vulnerability | |
CVE-2024-32896 | 7.8 (High) | Android Pixel Privilege Escalation Vulnerability |
Updated Malware Signatures (Week 2 - June 2024)
Threat | Description | |
Nanocore | The Nanocore trojan, built on the .NET framework, has been the subject of multiple source code leaks, resulting in its widespread accessibility. Like other remote access trojans (RATs), Nanocore empowers malicious actors with complete system control, enabling activities such as video and audio recording, password theft, file downloads, and keystroke logging. | |
Remcos | Remcos functions as a remote access trojan (RAT), granting unauthorised individuals the ability to issue commands on the compromised host, record keystrokes, engage with the host's webcam, and take snapshots. Typically, this malicious software is distributed through Microsoft Office documents containing macros, which are often attached to malicious emails. | |
Lumma Stealer | A type of malware classified as an information stealer. Its primary purpose is to steal sensitive information from infected systems, including but not limited to credentials, financial information, browser data, and potentially other personal or confidential information. |
| Ransomware Report | |
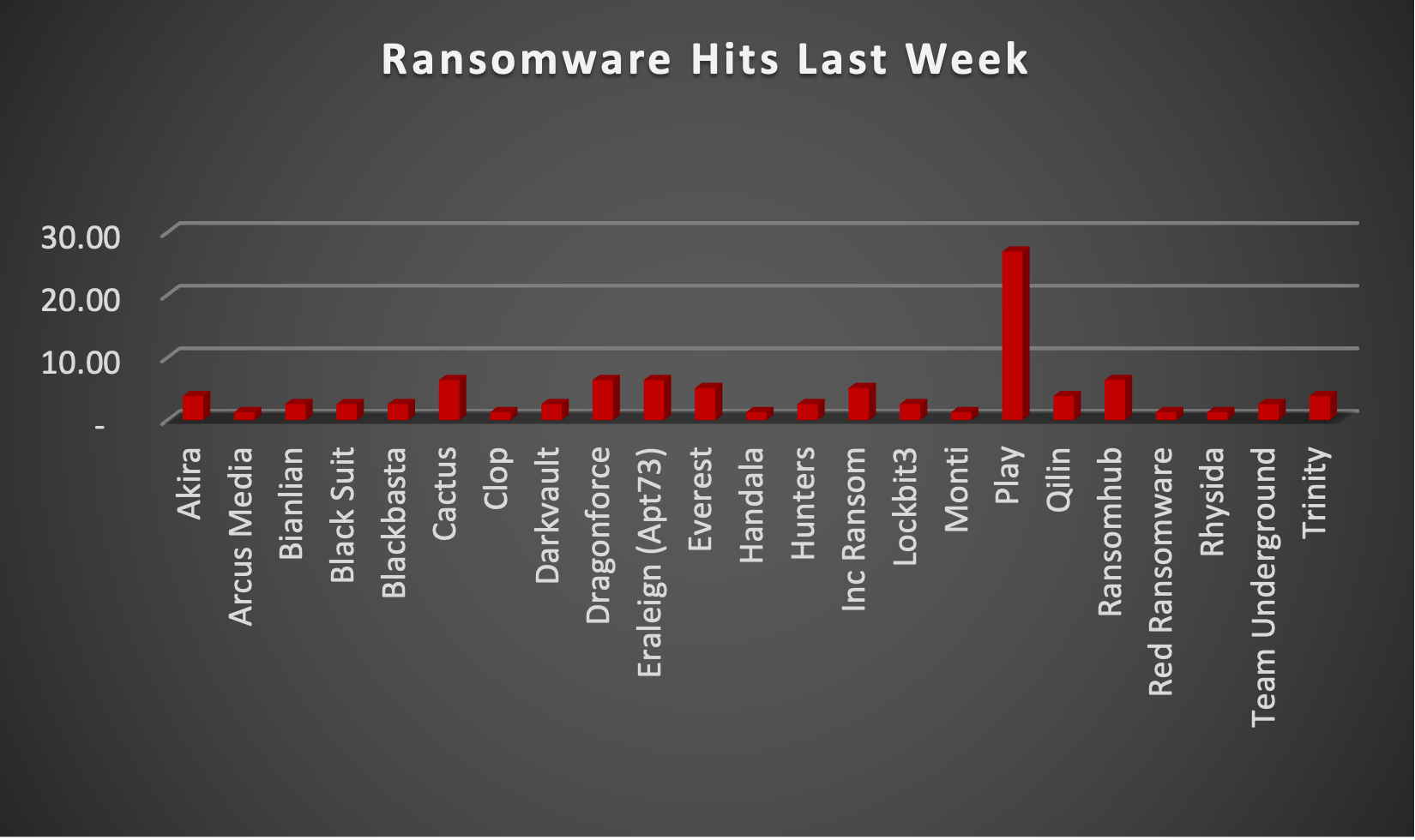
The Red Piranha Team actively collects information on organisations globally affected by ransomware attacks from various sources, including the Dark Web. In the past week alone, our team uncovered new ransomware victims and updates on previous victims across 18 industries spanning 19 countries. This underscores the widespread and indiscriminate impact of ransomware attacks, emphasising their potential to affect organisations of varying sizes and sectors worldwide. Play ransomware group stands out as the most prolific, having updated 26% of victims across multiple countries. In comparison, Cactus, Dragonforce, Eraleign (APT73), and Ransomhub ransomware updated 6% of victims each, in the past week. The following list provides the victim counts in percentages for these ransomware groups and a selection of others. | |
| Name of Ransomware Group | Percentage of new Victims last week |
Akira | 3.85% |
Arcus Media | 1.28% |
Bianlian | 2.56% |
Black Suit | 2.56% |
Blackbasta | 2.56% |
Cactus | 6.41% |
1.28% | |
Darkvault | 2.56% |
Dragonforce | 6.41% |
Eraleign (Apt73) | 6.41% |
Everest | 5.13% |
Handala | 1.28% |
Hunters | 2.56% |
Inc Ransom | 5.13% |
2.56% | |
Monti | 1.28% |
26.92% | |
Qilin | 3.85% |
Ransomhub | 6.41% |
Red Ransomware | 1.28% |
Rhysida | 1.28% |
Team Underground | 2.56% |
Trinity | 3.85% |
Cactus Ransomware
First detected in the wild around March 2023, Cactus ransomware swiftly established itself as a formidable foe in the cybersecurity landscape. This ruthless malware employs a double extortion tactic, crippling victims by encrypting their data and threatening to leak it on the dark web if ransom demands are not met. While the exact origins of Cactus remain shrouded in some mystery, security researchers believe it may be linked to a Malaysian hacktivist group of the same name. However, the technical capabilities showcased by Cactus ransomware suggest that it leverages the leaked codebase of LockBit Black, a notorious ransomware group known for its effectiveness.
Tactics, Techniques, and Procedures (TTPs):
Cactus ransomware does not rely on brute force alone. It possesses a diverse arsenal of tactics, techniques, and procedures (TTPs) to infiltrate and compromise systems. Here are some of the most common methods employed:
- Phishing Attacks
Deceptive emails designed to trick users into clicking malicious links or downloading infected attachments are a frequent entry point. These emails may appear to be from legitimate sources such as banks, logistics companies, or even colleagues.
- Exploiting Unpatched Vulnerabilities
Cactus actively seeks out unpatched vulnerabilities in software and operating systems to gain unauthorised access to networks. This underscores the importance of keeping all software and systems updated with the latest security patches. Here are some recently exploited vulnerabilities by the Cactus Ransomware group, based on credible security sources:
- VPN vulnerabilities: A key element of Cactus' attack strategy seems to be targeting vulnerabilities in Virtual Private Network (VPN) appliances. Reports suggest they may have exploited flaws in Fortinet VPN devices, but other VPN vendors could potentially be vulnerable as well.
- Qlik Sense vulnerabilities: Security researchers have observed Cactus exploiting vulnerabilities within Qlik Sense, a popular data analytics platform. These vulnerabilities might grant attackers initial access to a system.
- Lateral Movement: Once a foothold is established on a single device, Cactus can utilise various tools to move laterally across a network. This allows it to infect additional devices and escalate privileges, potentially compromising critical systems.
- Living-off-the-Land Techniques
Like other malware strains, Cactus can utilise legitimate system administration tools for malicious purposes. This makes detection more challenging as these tools may appear as normal system activity.
For more information on Living-off-the-land techniques.
- Data Exfiltration
Before encryption, Cactus often exfiltrates sensitive data like financial records, personal information, and intellectual property. This stolen data serves as additional leverage in extortion attempts, putting pressure on victims to pay the ransom.
- Strong Encryption
The malware utilises robust encryption algorithms to render files inaccessible. Decrypting them without the attacker's key is extremely difficult, if not impossible. This effectively cripples a victim's operations until a decision is made.
A Global Reach with Focused Targets:
Cactus ransomware demonstrates a lack of geographical bias, targeting victims worldwide. Here are some examples of its reach and the damage it has caused:
- Government Entities in Latin America: Early reports in July 2022 indicated widespread Cactus ransomware attacks targeting government entities in Latin America. These attacks can disrupt critical services and cause significant delays in government operations.
- Manufacturing Disruptions: Manufacturing companies across the globe have fallen victim to Cactus, experiencing data breaches, operational disruptions, and potential production delays.
- Critical Infrastructure Concerns: The increasing sophistication of Cactus raises concerns about potential attacks on critical infrastructure, such as power grids or transportation systems. A successful attack on such infrastructure could have catastrophic consequences.
Leak Site
Cactus ransomware maintains a leak site on the dark web where they threaten to publish stolen data if the ransom is not paid.
Ransom Note
The Cactus ransomware has a different ransom note for every victim. One of the Cactus ransom note is given below:
The emergence of Cactus ransomware underscores the ever-evolving landscape of cyber threats. Its use of readily available tools like LockBit Black's codebase and its focus on double extortion tactics highlight the need for organisations to prioritise robust cybersecurity measures. Here are some crucial steps organisations can take to mitigate the risk of Cactus ransomware and similar threats:
- Regular Backups: Maintain secure, offline backups of critical data to facilitate recovery in case of a ransomware attack.
- Patch Management: Implement a rigorous patch management system to ensure all software and operating systems are updated with the latest security patches.
- Security Awareness Training: Educate employees on identifying phishing attempts and other social engineering tactics used by attackers. Regular training can significantly reduce the risk of human error leading to breaches.
- Endpoint Security Solutions: Deploy endpoint security solutions that can detect and prevent malware infections at the device level. These solutions can act as a first line of defence against Cactus and other malware threats.
- Network Segmentation: Segmenting your network can limit the lateral movement of ransomware, potentially preventing it from spreading throughout your entire infrastructure.
- Incident Response Planning: Develop and regularly test an incident response plan to effectively respond to a ransomware attack and minimise damage. Having a plan in place ensures a more coordinated and efficient response during a crisis.
Kill Chain:
Tactic | Technique ID | Technique Name |
Initial Access | T1190 | Exploit Public-Facing Application |
Execution | T1059 T1053 T1072 | Command and Scripting Interpreter Scheduled Task/Job Software Deployment Tools |
Persistence | T1136 | Create Account |
Defence Evasion | T1562 T1027 T1070 | Impair Defences Obfuscated Files or Information Indicator Removal |
Credential Access | T1555 T1003 | Credentials from Password Stores OS Credential Dumping |
Discovery | T1049 T1083 | System Network Connections Discovery File and Directory Discovery |
Lateral Movement | T1072 T1570 | Software Deployment Tools Lateral Tool Transfer |
Collection | T1119 | Automated Collection |
Exfiltration | T1567 | Exfiltration Over Web Service |
Command-and-Control | T1219 T1090 | Remote Access Software Proxy |
Indicators of Compromise (IOCs)
Indicators | Indicator Type | Description |
hxxps://cactusbloguuodvqjmnzlwetjlpj6aggc6iocwhuupb47laukux7ckid.onion hxxps://cactus5dqnqkppa5ayckiyk6dttpqwczdqphv5mxh4dkk5ct544q5aad.onion | URLs (Onion) | Leak Site |
163.123.142.213 64.52.80.252 162.33.177.56 45.61.138.99 206.188.196.20 45.61.136.79 45.61.136.127 | IP | C2 |
cactus787835@proton[.]me | Email | Contact |
eba1596272ff695a1219b1380468293a e28db6a65da2ebcf304873c9a5ed086d de6ce47e28337d28b6d29ff61980b2e9 949d9523269604db26065f002feef9ae 5737cb3a9a6d22e957cf747986eeb1b3 2611833c12aa97d3b14d2ed541df06b2 1add9766eb649496bc2fa516902a596 d5e5980feb1906d85fbd2a5f2165baf7 78aea93137be5f10e9281dd578a3ba73 26f3a62d205004fbc9c76330c1c71536 be7b13aee7b510b052d023dd936dc32f 39fe99d2250954a0d5ed0e9ff9c41d81 0e4ee38fe320cfb573a30820198ff442 8d2e4bef47e3f2ee0195926bbf4a25d5 f7a6d1e6e5436bd3c10f3a26f3e9b9b9 fb467a07f44e8d58e93e3567fd7ff016 be139fc480984eb31de025f25a191035 08d2c800c93015092e14738c941ac492 02e4da16377fc85e71a8c8378b2a8a96 8b37df9d295bbc2906961f72b7cdc5fb 8af259ad55c3746926e992c82bc7e850 55e42014424c0d120ff17f11e207e4f0 5f7c3cda7759ef6e577552ad322c1f64 | Hash | File |
| |||||||||||||||||||||||||||||||||||||||||||
Upon further investigation, it has been identified that ransomware has left its mark on 18 different industries worldwide. Notably, Manufacturing bore the brunt of the attacks in the past week, accounting for 21% of victims. There are a few key reasons why the manufacturing sector is a prime target for ransomware groups:
- High Disruption Potential: Manufacturing relies heavily on interconnected systems and just-in-time production. A ransomware attack can grind operations to a halt, causing significant financial losses due to production delays and lost revenue. This pressure to get back online quickly can make manufacturers more willing to pay the ransom.
- Vulnerable Legacy Systems: Many manufacturers use legacy control systems (OT) that have not been updated for security. These older systems often lack robust security features, making them easier targets for attackers to exploit.
- Limited Cybersecurity Investment: Traditionally, cybersecurity might not have been a top priority for some manufacturers compared to production efficiency. This lack of investment in security awareness training and robust security protocols leaves them exposed.
- Valuable Data: Manufacturing facilities often hold valuable intellectual property (IP) and trade secrets. Ransomware groups may not only disrupt operations but also threaten to leak this sensitive data if the ransom is not paid.
- Success Breeds Success: The high payout potential from past attacks on manufacturers incentivises ransomware groups to continue targeting them.
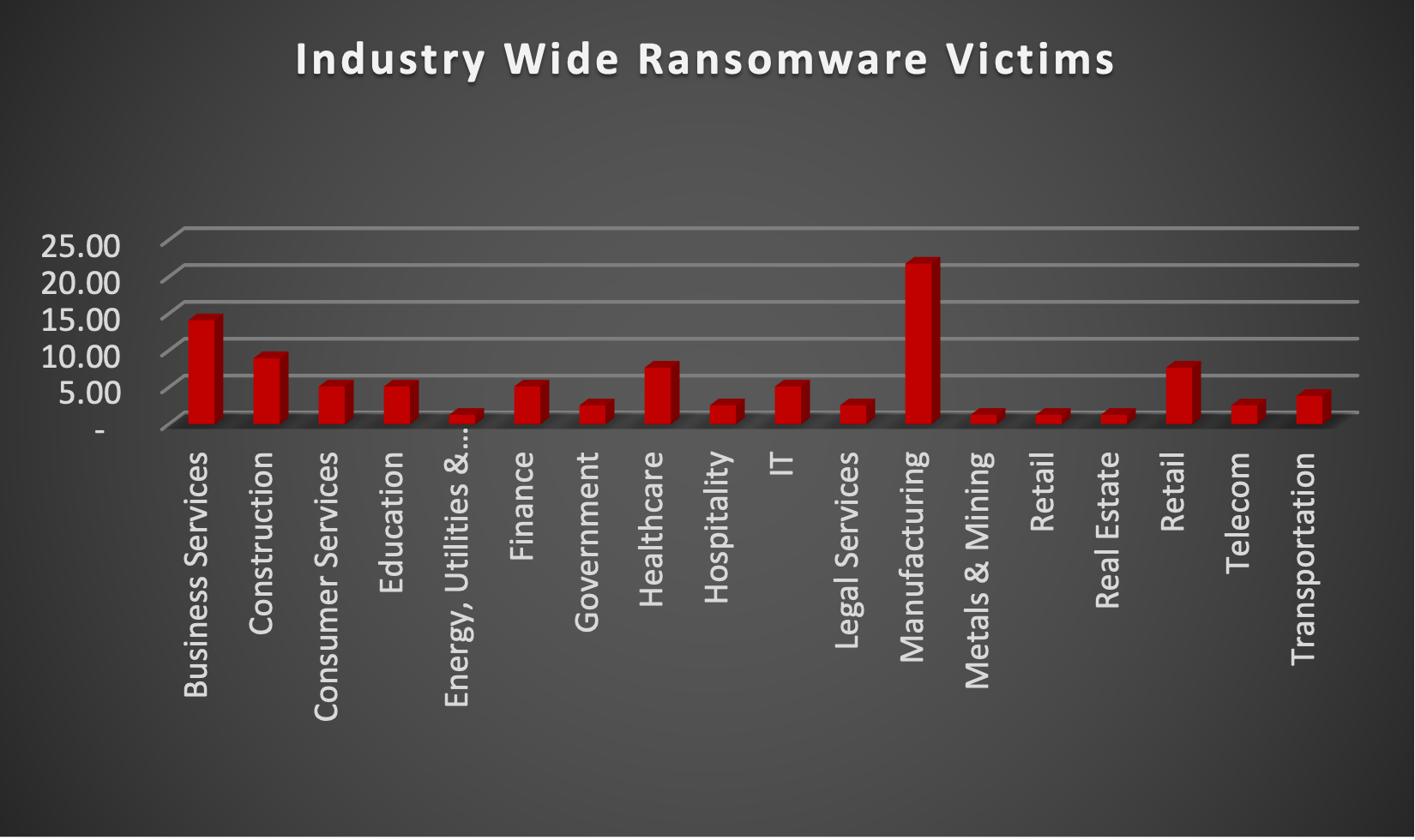
The table below delineates the most recent ransomware victims, organised by industry, shedding light on the sectors grappling with the significant impact of these cyber threats.
Name of the affected Industry | Victims Count (%) |
Business Services | 14.10% |
Construction | 8.97% |
Consumer Services | 5.13% |
Education | 5.13% |
Energy, Utilities & Waste Treatment | 1.28% |
Finance | 5.13% |
Government | 2.56% |
Healthcare | 7.69% |
Hospitality | 2.56% |
IT | 5.13% |
Legal Services | 2.56% |
Manufacturing | 21.79% |
Metals & Mining | 1.28% |
Retail | 1.28% |
Real Estate | 1.28% |
Retail | 7.69% |
Telecom | 2.56% |
Transportation | 3.85% |