| New Threat Detection Added | 3 (Gh0stBins Malware, DarkComet RAT and DarkGate Malware) |
| New Threat Protections | 183 |
Weekly Detected Threats
The following threats were added to Crystal Eye XDR this week:
Threat name: | Gh0stBins Malware | ||||||||||||||||||
Gh0stBins is a nasty piece of malware classified as a Remote Access Trojan (RAT). This means it gives attackers full control over your device once infected. Launched in 2008, it's been a favourite tool for cybercriminals targeting governments and corporations. Be cautious of spam emails, as they're a common way Gh0stBins spreads. If infected, your privacy is at risk, you could suffer financial losses, and even have your identity stolen. | |||||||||||||||||||
Threat Protected: | 03 | ||||||||||||||||||
Rule Set Type: |
| ||||||||||||||||||
Class Type: | Trojan-activity | ||||||||||||||||||
Kill Chain: |
| ||||||||||||||||||
Threat name: | DarkComet RAT | ||||||||||||||||||
DarkComet RAT, short for Remote Access Trojan, is a malicious program that lurks in the shadows. Developed in 2008, it gives attackers remote control over your computer, allowing them to steal sensitive information, spy on your activity, and even manipulate your device. While its creator intended it as a legitimate tool, it gained notoriety for its use in cyberattacks, including the Syrian Civil War. Though development has ceased, DarkComet remains a threat. | |||||||||||||||||||
Threat Protected: | 01 | ||||||||||||||||||
Rule Set Type: |
| ||||||||||||||||||
Class Type: | Trojan-activity | ||||||||||||||||||
Kill Chain: |
| ||||||||||||||||||
Threat name: | DarkGate Malware | |||||||||||||||||||||
DarkGate malware lurks as a backdoor threat, silently granting remote access to your system. First appearing in 2017, it's become a favourite tool for cybercriminals sold as Malware-as-a-Service (MaaS). DarkGate empowers attackers with a buffet of malicious options, including stealing information, deploying cryptocurrency miners to steal your processing power for their gain, and even launching further attacks from your compromised device. Phishing emails and collaborative applications like Microsoft Teams are common ways DarkGate infiltrates systems. | ||||||||||||||||||||||
Threat Protected: | 05 | |||||||||||||||||||||
Rule Set Type: |
| |||||||||||||||||||||
Class Type: | Trojan-activity | |||||||||||||||||||||
Kill Chain: |
| |||||||||||||||||||||
Known exploited vulnerabilities (Week 3 - May 2024)
Threat | CVSS | Description | |
CVE-2024-30040 | 8.8 (High) | Microsoft Windows MSHTML Platform Security Feature Bypass Vulnerability | |
CVE-2024-30051 | 7.8 (High) | Microsoft DWM Core Library Privilege Escalation Vulnerability | |
CVE-2024-4761 | Ongoing analysis | Google Chromium V8 Out-of-Bounds Memory Write Vulnerability | |
CVE-2021-40655 | 7.5 (High) | D-Link DIR-605 Router Information Disclosure Vulnerability | |
CVE-2014-100005 | 6.8 (Medium) | D-Link DIR-600 Router Cross-Site Request Forgery (CSRF) Vulnerability |
Updated Malware Signatures (Week 3 - May 2024)
Threat | Description | |
Bifrost | A remote access trojan that enables its operator to take control of a victim machine and steal data. It is usually distributed through spam and phishing emails. | |
CoinMiner | This malicious software installs and runs cryptocurrency mining applications. | |
QuasarRat | A remote access trojan that was made available to the public as an open-source project. Once installed on a victim’s machine, it is capable of keylogging, data and screen capturing among other things. It is also known to be highly customisable depending on the threat actor’s intended need. | |
Glupteba | A malware dropper that is designed to download additional malware on an infected machine. |
| Ransomware Report | |
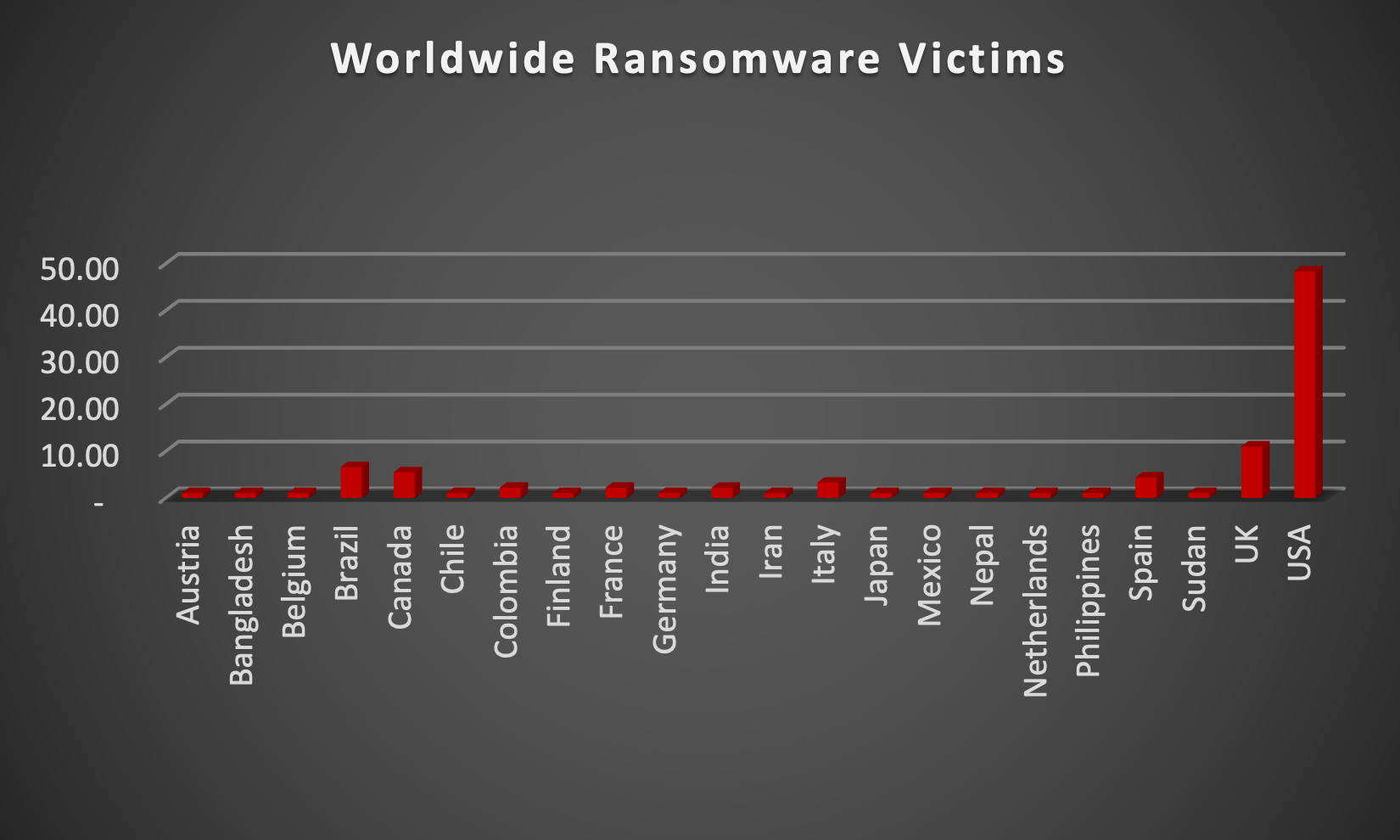
The Red Piranha Team actively collects information on organisations globally affected by ransomware attacks from various sources, including the Dark Web. In the past week alone, our team uncovered new ransomware victims and updates on previous victims across 21 different industries spanning 22 countries. This underscores the widespread and indiscriminate impact of ransomware attacks, emphasising their potential to affect organisations of varying sizes and sectors worldwide. LockBit3.0 ransomware stands out as the most prolific, having updated a significant number of victims (18%) distributed across multiple countries. In comparison, DragonForce ransomware updated 12% of victims, in the past week. The following list provides the victim counts in percentages for these ransomware groups and a selection of others. | |
| Name of Ransomware Group | Percentage of new Victims last week |
3AM | 2.20% |
8Base | 8.79% |
Akira | 3.30% |
Arcus Media | 7.69% |
Bianlian | 2.20% |
Black Suit | 2.20% |
Cactus | 4.40% |
DragonForce | 12.09% |
Everest | 1.10% |
Hunters | 2.20% |
Inc Ransom | 8.79% |
Killsec | 2.20% |
18.68% | |
Money Message | 1.10% |
Monti | 2.20% |
4.40% | |
Qilin | 3.30% |
Ransomhouse | 2.20% |
Ransomhub | 7.69% |
Rhysida | 1.10% |
Snatch | 1.10% |
Stormous | 1.10% |
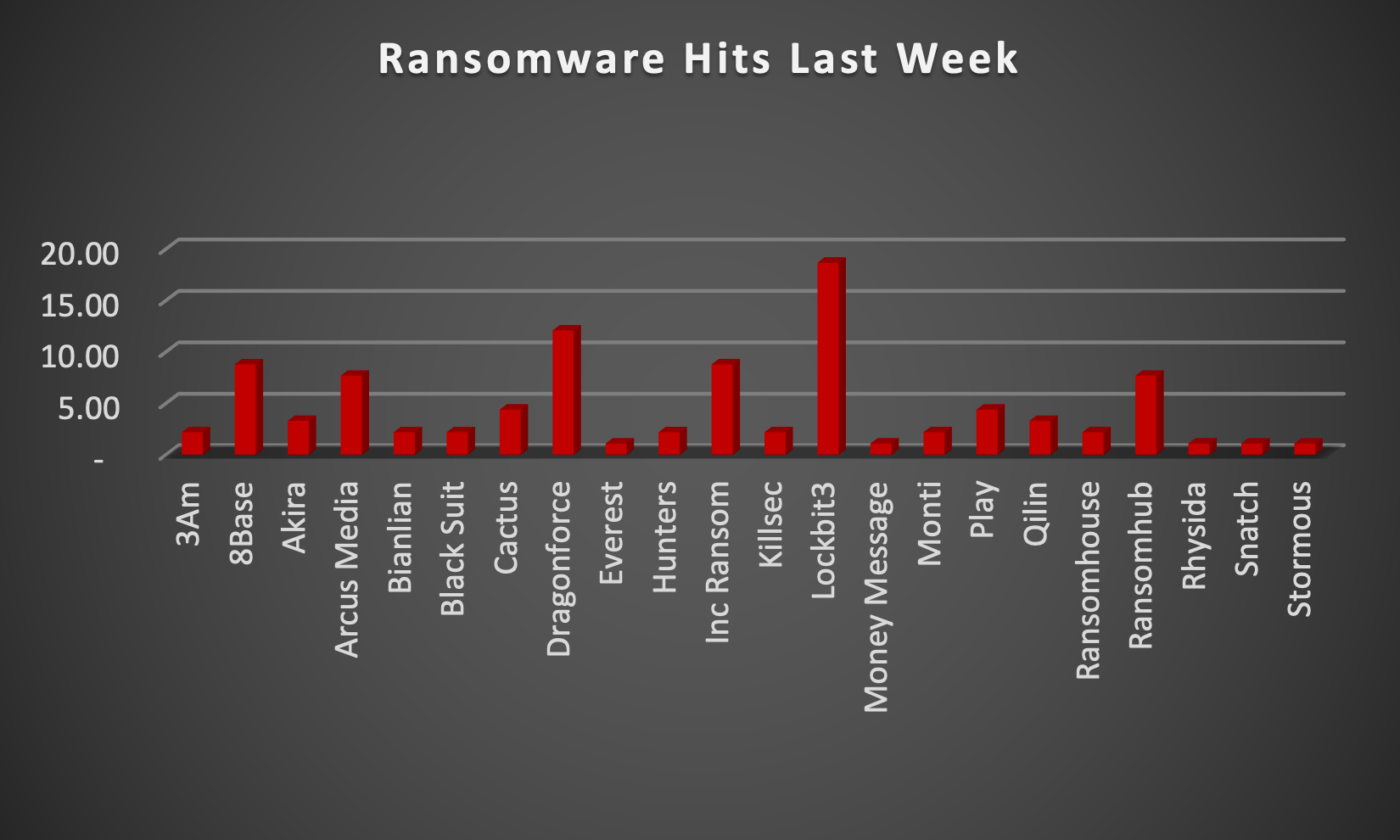
DragonForce Ransomware
Emerging in late 2023, DragonForce ransomware has quickly become a force to be reckoned with in the cybersecurity landscape. This ruthless malware employs a double extortion tactic, crippling victims by encrypting their data and threatening to leak it on the dark web if ransom demands aren't met.
The origins of DragonForce remain shrouded in some mystery. While a Malaysian hacktivist group of the same name announced plans to launch ransomware in 2022, the connection to the current DragonForce ransomware is unclear. Security researchers believe the ransomware itself is built upon the leaked codebase of LockBit Black, a notorious ransomware group. This shared lineage suggests a certain level of sophistication, as LockBit Black was known for its effectiveness.
Tactics, Techniques, and Procedures (TTPs)
DragonForce leverages a range of tactics, techniques, and procedures (TTPs) to infiltrate and compromise systems. These include:
- Phishing Attacks: Deceptive emails designed to trick users into clicking malicious links or downloading infected attachments are a common entry point.
- Exploiting Vulnerabilities: DragonForce actively seeks out unpatched vulnerabilities in software and operating systems to gain unauthorised access to networks.
- Lateral Movement: Once a foothold is established, the malware can spread laterally across a network, infecting additional devices and escalating privileges.
- Data Exfiltration: Before encryption, DragonForce exfiltrates sensitive data like financial records, personal information, and intellectual property. This stolen data serves as leverage in extortion attempts.
- Strong Encryption: DragonForce utilises robust encryption algorithms to render files inaccessible, making decryption without the attacker's key extremely difficult, if not impossible.
Famous Fallouts:
DragonForce has targeted a diverse range of victims worldwide, demonstrating its opportunistic nature. Some notable examples include:
- The Ohio Lottery: In a high-profile attack, DragonForce breached the Ohio Lottery's systems and claimed to have stolen over 600 GB of data, potentially compromising millions of records.
- Yakult Australia: Dragonforce ransomware claimed to have attacked this beverage company, boasting about stealing nearly 100 GB of sensitive company data.
- Coca-Cola Singapore: Dragonforce ransomware claimed to have attacked the Singapore branch of Coca-Cola, stealing data exceeding 400 GB.
Global Targets: Its reach extends beyond these specific cases. Reports indicate that DragonForce has targeted organisations in manufacturing, technology, healthcare, finance, and other critical sectors across various countries.
DragonForce's emergence highlights the ever-evolving threat landscape of ransomware. Its use of readily available tools like LockBit Black's codebase and its focus on double extortion tactics underscore the need for organisations to prioritise cybersecurity measures.
Leak Site: DragonForce maintains a leak site on the dark web where they threaten to publish stolen data if the ransom is not paid.
DragonForce Ransom Notes:
Tactic | Technique ID | Technique Name |
Execution | T1204.002 | User Execution |
Defence Evasion | T1562.001 T1070.004 | Impair Defences: Disable or Modify Tools Indicator Removal: File Deletion |
Discovery | T1083 | File and Directory Discovery |
Impact | T1486 | Data Encrypted for Impact |
Indicators of Compromise (IOCs)
Indicators | Indicator Type | Description |
d54bae930b038950c2947f5397c13f84 | Hash | DragonForce Ransomware |
hxxp://z3wqggtxft7id3ibr7srivv5gjof5fwg76slewnzwwakjuf3nlhukdid.onion/blog | URLs | Leak Site |
| |||||||||||||||||||||||||||||||||||||||||||||||||
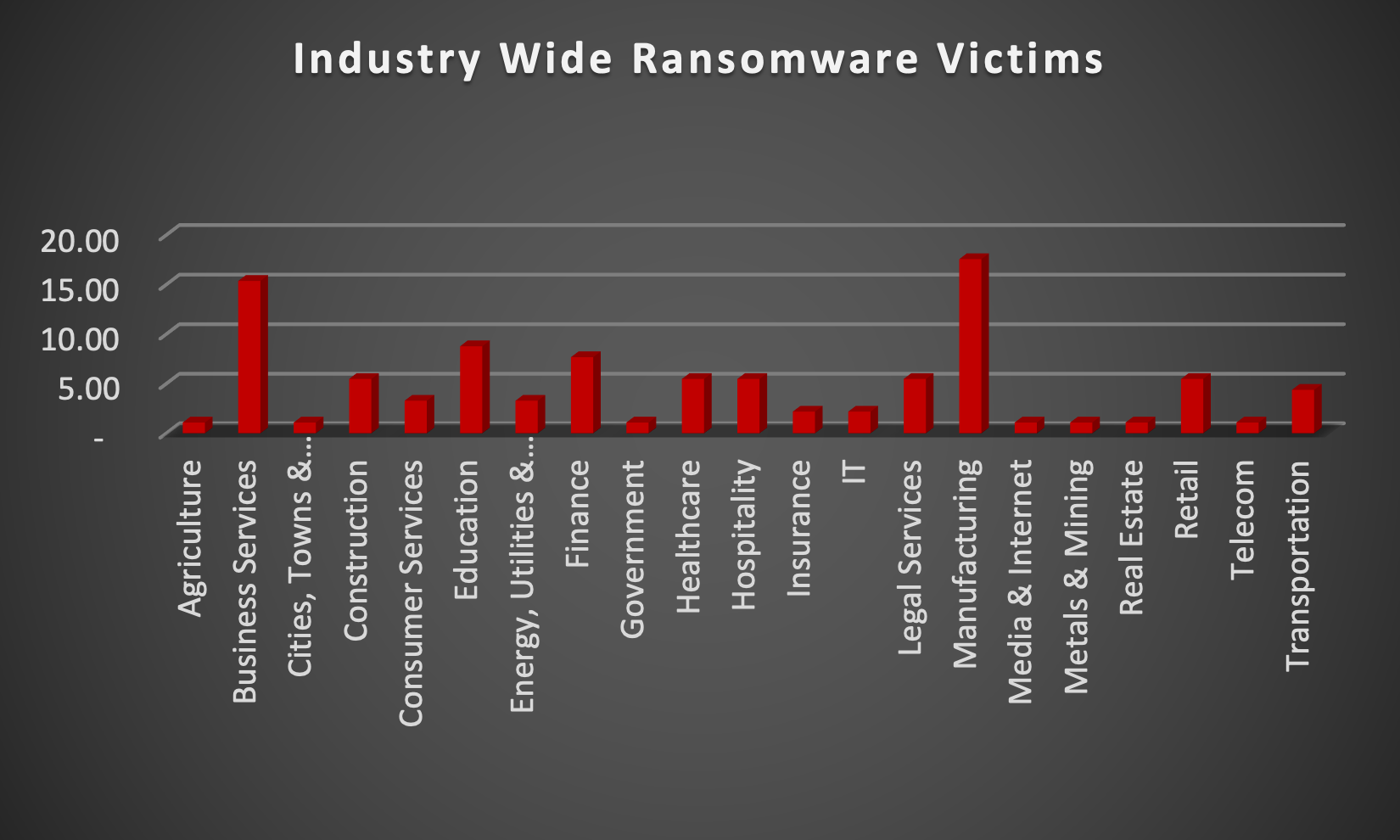
Upon further investigation, it has been identified that ransomware has left its mark on 21 different industries worldwide. Notably, Manufacturing bore the brunt of the attacks in the past week, accounting for 17% of victims. There are a few key reasons why the manufacturing sector is a prime target for ransomware groups:
- High Disruption Potential: Manufacturing relies heavily on interconnected systems and just-in-time production. A ransomware attack can grind operations to a halt, causing significant financial losses due to production delays and lost revenue. This pressure to get back online quickly can make manufacturers more willing to pay the ransom.
- Vulnerable Legacy Systems: Many manufacturers use legacy control systems (OT) that haven't been updated for security. These older systems often lack robust security features, making them easier targets for attackers to exploit.
- Limited Cybersecurity Investment: Traditionally, cybersecurity might not have been a top priority for some manufacturers compared to production efficiency. This lack of investment in security awareness training and robust security protocols leaves them exposed.
- Valuable Data: Manufacturing facilities often hold valuable intellectual property (IP) and trade secrets. Ransomware groups may not only disrupt operations but also threaten to leak this sensitive data if the ransom isn't paid.
- Success Breeds Success: The high payout potential from past attacks on manufacturers incentivises ransomware groups to continue targeting them.
The table below delineates the most recent ransomware victims, organised by industry, shedding light on the sectors grappling with the significant impact of these cyber threats.
Name of the affected Industry | Victims Count (%) |
Agriculture | 1.10% |
Business Services | 15.38% |
Cities, Towns & Municipalities | 1.10% |
Construction | 5.49% |
Consumer Services | 3.30% |
Education | 8.79% |
Energy, Utilities & Waste | 3.30% |
Finance | 7.69% |
Government | 1.10% |
Healthcare | 5.49% |
Hospitality | 5.49% |
Insurance | 2.20% |
IT | 2.20% |
Legal Services | 5.49% |
Manufacturing | 17.58% |
Media & Internet | 1.10% |
Metals & Mining | 1.10% |
Real Estate | 1.10% |
Retail | 5.49% |
Telecom | 1.10% |
Transportation | 4.40% |